NXP recently launched the EdgeLock A30 Secure Authenticator chip, a Common Criteria EAL 6+ certified secure authentication designed for IoT devices, including battery authentication applications. It complies with the EU’s Batteries Regulation 2023/1542, which mandates the inclusion of a Digital Product Passport (DPP), by 2027 to ensure traceability, sustainability, and safety in battery manufacturing and recycling. Alasdair Ross, Senior Director, NFC IoT Security, NXP explains:
Secure authentication helps to ensure brand protection, consumer safety, and product traceability, fostering trust and shielding devices from physical damage. Smaller than a grain of rice, the EdgeLock A30 is designed to fit into even the smallest of devices. It supports multiple authentication use cases, making it easier for developers to support a variety of devices and accessories with a single solution, including device to device, cloud to device, counterfeit protection, and storage or protection of device identity.
To address these requirements NXP’s EdgeLock A30 comes with security features such as AES-128/256, ECDSA, ECDH, PKI-based key management, and a Random Number Generator (RNG) compliant with NIST SP800-90B standards. Certified to the AVA_VAN.5 vulnerability analysis assurance level, the chip is designed to handle sophisticated attacks. With its compact WLCSP and HVQFN20 packages, extended operating temperature range (-40°C to +105°C), and support for NXP’s EdgeLock 2GO IoT platform for secure certificate provisioning, the chip is ideal for batteries, industrial equipment, medical devices, chargers, and other applications requiring high security and compliance with regulatory standards for secure and sustainable product designs.
NXP EdgeLock A30 specifications:
- Secure RISC-V core
- Memory – 16 kB free user memory
- Cryptographic features
- Symmetric algorithms – AES-128/256 (ECB, CBC, CMAC, CCM, GCM)
- Hashing – SHA-256, SHA-384, HMAC, HKDF (RFC5869)
- Asymmetric Algorithms
- ECDSA and ECDH (NIST P-256, Brainpool P256r1)
- Key management and provisioning via PKI
- Random Number Generator (RNG) – NIST SP800-90B compliant
- Interfaces
- I²C 100 kHz, 400 kHz, or 1 MHz
- Two configurable General-Purpose IOs
- Hardware features
- TRNG – NIST SP800-90B, AIS31
- DRBG – NIST SP800-90A, AIS20
- Power
- Supply voltage – 1.0V to 2.0V
- Deep power-down mode max. 5 μA (activated via T=1‘ over I2C)
- Package
- WLCSP
- HVQFN20
- Operating temperature – -40°C to +105°C
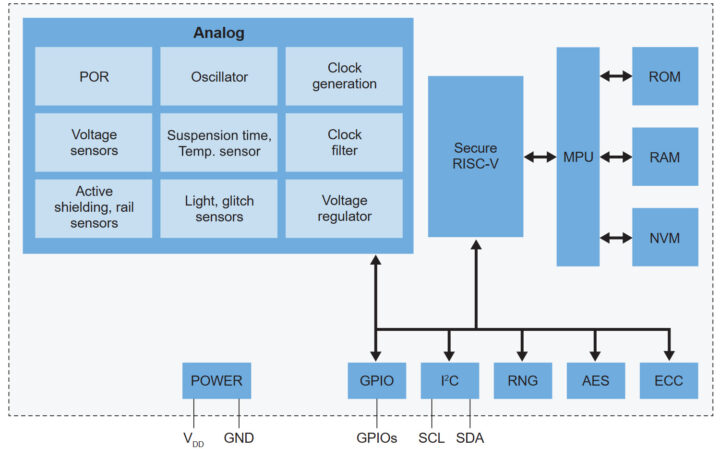
The MPU (Memory Protection Unit) in the EdgeLock A30 acts as an intermediary between the Secure RISC-V processor and the memory subsystems, including ROM, RAM, and Non-Volatile Memory (NVM). The MPU separates secure and non-secure data or processes, especially in cryptographic and secure applications. The MPU manages memory resources effectively, with ROM typically storing immutable secure boot code, RAM handling runtime operations, and NVM securely storing configuration data, credentials, or cryptographic keys. By preventing unauthorized access and protecting memory integrity, the MPU protects data against attacks like buffer overflows or memory tampering, making it a vital component of the EdgeLock A30’s secure architecture.
The company provides various software and tools that simplify integration and deployment. It supports the EdgeLock 2GO platform, which handles secure certificate generation, delivery, and provisioning for IoT devices. Additionally, tools, examples, and documentation are available on GitHub.
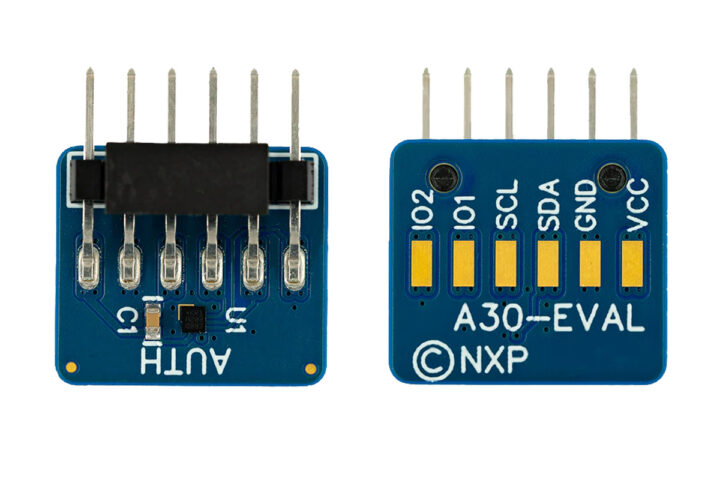
The A30-EVAL development kit (breakout board) supports platforms like Arduino, Raspberry Pi, and other MCUs via I²C connections, enabling seamless evaluation of the EdgeLock A30’s features.
Previously, we have written about the A71CH Secure Element Chip which is specifically designed for TLS-based communication in IoT and provides secure cloud connectivity and provisioning. The A30 focuses on authentication and anti-counterfeiting.
The EdgeLock A30 Secure Authenticator chip is priced at $0.77 each for 1,000-unit trays, though you have to order a minimum of 10,000 units. More information about the product can be found on its product page and press release.
Debashis Das is a technical content writer and embedded engineer with over five years of experience in the industry. With expertise in Embedded C, PCB Design, and SEO optimization, he effectively blends difficult technical topics with clear communication
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress






Well, I guess the real and sole purpose will be to allow product vendors to more easily perform vendor lock-in on batteries like cartridges with printers. They don’t like it at all when their customer prolong products lives by replacing dead batteries, so that will be a nice way to force customers to trash the device and buy a new one.
I wasn’t aware of the EU regulation mentioned above. I’ve glanced over it. It’s amazing to see that we’re paying people to write 135 pages of details as tiny as the size of a logo on a battery to indicate its constituents and whether it’s rechargeableor not (and translated in all languages). No wonder the EU is currently engluing itself by spending so much energy on so insignificant tasks! It’s even possible that the outcomes of the total energy spent on this overweights the savings expected by the slightly better recycling. Actually the only possibly positive thing they could have done would have been to mandate repairability by explicitly forbidding battery authentication. But they failed at that as well…
[ we, then, just wait for the group of people, requesting payment for summarizing these more easy 117 pages (for the English translation, for the ‘Official Journal
of the European Union’ edition it’s even ~191 pages) to ‘ordinary’ customers/consumers 🙂
, what else shall people do within, never stagnating, ‘capitalism'(?)
Give the poor something to eat, instead! ]
Makes no sense, EU policies are aimed at saving e-waste, why this would become a way to create more of it? mmm, I wonder what issue will cause…
[ or the burden of updating IoT-devices @theBillions
, sure having to remember this for keeping it on recent software and for devices having a digital device passport (“A Digital Product Passport (DPP) is a digital record that provides comprehensive information about a product and its entire value chain. This includes everything from the origin of the product, materials used, environmental impact, and disposal recommendations.”).
Hopefully ‘they’ get digital voting systems ‘secure’, more improved than digital medical reports storage and data exchange(?)
If it’s a mass product of 1k-10k devices, a product certification (sheet of paper -> .pdf) for all this information should be enough (with a firmware included, read-only, product identification, like done for e.g. USB devices)?
We ‘share’ Your (authenticated) data, ‘anonymously’, but ‘secure’ (for ‘us’)(?) ]
Unfortunately, as usual with incompetent bureaucracy, there’s a huge gap between the original intent and the outcome. Authenticating batteries will definitely mean non-repairable devices very quickly. They *are* opening the doors for trashable devices. I’m certain that was not the intent but that’s what will happen. On the opposite they ought to have forbidden component authentication (batteries, cartridges etc) to permit serviceability and repairability beyond the vendor’s support and at reasonable prices. We’ve all seen people replace a printer instead of a cartridge because it’s the same price. Here it will be the same with entry-level laptops, smartphones and most consumer products when only the vendor will be able to sell a battery at half the price of the replacement product.
EUxit! Now!