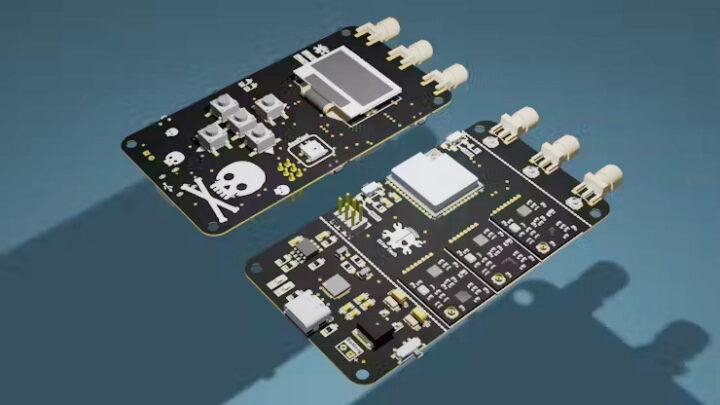
CiferTech has recently introduced the nRFBOX V2 ESP32-based wireless hacking tool designed for spectrum analysis, jamming, BLE device emulation, and more. The device is built around an ESP32-WROOM-32U module and includes an NRF24 module covering the whole 2.4GHz spectrum. Additionally, the device has a 0.96-inch OLED display, a five-way microswitch control pad, and a WS2812 RGB LED for feedback. The device can also be operated with a single 3.7V lithium battery, and that batter’s charging is handled by a TP4056 charging IC. All these features make this device useful for wireless security testing, educational environments, research, and hobbyist projects.
Previously we have written about similar portable hacking tools like the DSTIKE Deauther Watch X, the HackBat pen-testing device, and the popular Flipper Zero wireless hacking tool. Feel free to check those out if you are looking for similar products.
nRFBOX V2 specifications
- Microcontroller – ESP32-WROOM-32U with ESP32 dual-core wireless microcontroller
- CPU – Dual-core Xtensa 32-bit microprocessor @ 240MHz
- Memory and Storage – 16MB flash, 2MB PSRAM, and 520KB internal SRAM
- Wireless – Wi-Fi 802.11b/g/n, and Bluetooth (4.2 and BLE)
- Display – 0.96-inch OLED with 128×64 resolution
- Wireless – NRF24 GTmini Modules (x3 for advanced BLE jamming)
- USB – 1x USB-C port for power, charging, and programming via CP2102 USB to UART IC
- User control – 5-key D-Pad
- Misc
- 2x user LEDs,
- 2x system buttons
- 6-pin header for 3.3V, 5V, RX, TX
- Slider switch for switching between battery power and USB power.
- WS2812B RGB LED for notification
- Power Supply
- 5V via USB Type-C port
- 2-pin JST connector for 3.7V Lithium charged by a TP4056 charger IC.
- Dimensions – 87 x 48 mm
The board has three SMA connectors, each with a U.fl connector underneath for flexible configuration. You can use a coaxial cable to connect an antenna to the ESP32 and you are left with two more antennas for the Bluetooth module, or you can change the configuration and connect three antennas to three NRF24 Bluetooth modules for other purposes, such as BLE jamming.
The device has mainly three main features scanning, analyzing, and jamming. The scanner can scan the 2.4 GHz frequency spectrum for both Bluetooth and WiFi to identify active channels and detect nearby wireless devices and the signals of each device. The analyzer can capture and analyze packets to find out the least crowded channels, and can also used to monitor for unusual activity and detect net for attacks. The jammer sends out noise or signals on the same frequency as the target devices disrupting communication between devices, it can also be used to prevent unauthorized drone operations or to secure an area from wireless communication temporarily.
The ESP32 wireless hacking tool is completely open-sourced so you can make one yourself on a breadboard, and all the documentation related to the projects like schematics (JPG) and Arduino source code can be found on cifertech nRFBox GitHub repository. Cifertech also posted details about the project on Hackster.io so some more information can also be found there as well.
Debashis Das is a technical content writer and embedded engineer with over five years of experience in the industry. With expertise in Embedded C, PCB Design, and SEO optimization, he effectively blends difficult technical topics with clear communication
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress








For blocking unauthorized WiFi communications inside a room (e.g. meeting room), I found that combining 4 video transmitters configured on different channels was sufficient to avoid communications within a few meters (3-5m) because their frequency bands were quite large. I also tried with a 2.4 GHz VCO which I fed with a sawtooth generator. It works fine as well including against bluetooth within a meter or two, but is not efficient at all since it’s visiting many intermediate frequencies (linear scan) instead of performing discrete frequency hopping. I stopped researching on this topic when 5GHz arrived. Also I doubt it is possible to avoid drones with the device above, because usually you’re competing against another device’s transmitter which itself is set to the right frequency and has many more opportunities for sending its packets than this device which randomly tries many channels. If it’s able to detect the channel by scanning then jamming it, it can be different, though. Anyway, some transmitters (particularly video ones) are using 5 GHz now.
About the idea that this has a legitimate use in jamming “unauthorized” drone operation: jamming Wi-Fi signals is illegal in the USA at least. It doesn’t matter if you have a beef with a drone, you don’t get to jam Wi-Fi. I don’t even have to get into the fact that you don’t get to “authorize” drone operation, either it’s legal or it isn’t, but either way you don’t get to take vigilante action against it.
To be more specific, I guess you could say that the FAA has the ability to “authorize” drone operation, but they’re not going to be operating sketchy devices like this. But an individual person doesn’t get to buy something like this and use it just because they see a drone in the area and they don’t like it.
Can we not give the time of day to cancerous devices, please? Jamming is the lowest form of scriptkiddie-sm. I’d expect better from a journal like this.
Did you step out of 1998? “scriptkiddie”? Seriously? Go back to your ActiveX plugins, MSIE 4 and active desktop, dude. At least a coherent article written here, so give the author some credit for sharing his knowledge. Let us determine if for educational purposes or not. We don’t need your compass.
The ultimate drone jamming tool is the Daisy, which broadcasts in the BB band.