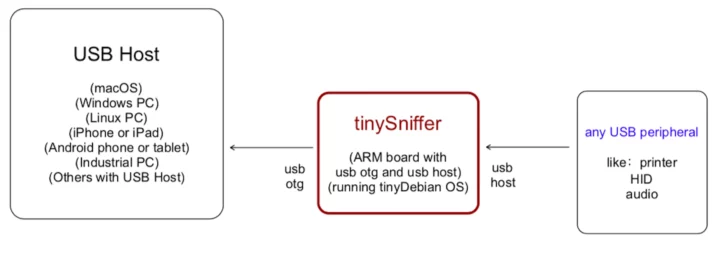
TinySniffer is a USB sniffer based on the Allwinner H3-powered NanoPi Neo Air SBC, designed to capture USB 1.x and 2.0 packets remotely, and whose captured data is compatible with the popular Wireshark packet analyzer tool.
Wireshark can already be used to capture USB packets on its own and I reverse-engineered a USB capture video solution that way in the past, but this method has some limitations, for instance, it does not capture some low-level USB packets, in which case a hardware USB sniffer like Total Phase Beagle USB, the PhyWhisperer USB, or the tinySniffer is required.
The micro USB OTG port of the NanoPi NEO Air SBC is connected to the host computer and the company added a USB 2.0 Type-A port connected to the USB interface on the GPIO header to connect a device under test such as a USB keyboard, a USB Ethernet dongle, a USB printer, and so on.
After configuring WiFi, the user can access the tinySniffer USB capture tool remotely by going to the https://www.usb7.net/ website and selecting My Devices. It will open a terminal window in your browser, and you’ll be able to capture packets with the sniff command
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
sniff@tinySniffer:~$ sniff -h Usage: sniff [-h] [-i] [-u UPLOAD_FILENAME] [-s] [-r] [-R] [-F [FILTERS]] tinySniffer starts usb capture when: 1) tinySniffer (with usb peripheral plugged) is connected to usb host (this powers on tinySniffer) (save to new file) 2) usb peripheral is unplugged and re-plugged to tinySniffer (save to new file) 3) run "sniffer.py -r" to restart usb capture and save to new file 4) run "sniffer.py -R" to emulate usb peripheral unplug / replug, restarts usb capture and save to new file optional arguments: -h, --help show this help message and exit -i, --info show usb capture info -u UPLOAD_FILENAME, --upload UPLOAD_FILENAME stop usb capture and upload captured file -s, --stop stop usb capture -r, --restart restart usb capture and save to new file -R, --RESTART emulate usb peripheral unplug / replug, restart usb capture and save to new file -F [FILTERS], --FILTERS [FILTERS] set capture filter, support multiple filters, separated by "," must use together with -r or -R argument to restart usb capture supported capture filters are: URB_ISO_OUT, URB_ISO_IN, URB_BULK_OUT, URB_BULK_IN examples: sniff -F URB_ISO_OUT,URB_ISO_IN -r sniff -F URB_BULK_OUT -R sniff -F URB_ISO_OUT,URB_ISO_IN,URB_BULK_OUT,URB_BULK_IN -R sniff -F -R # this is to clear capture filters |
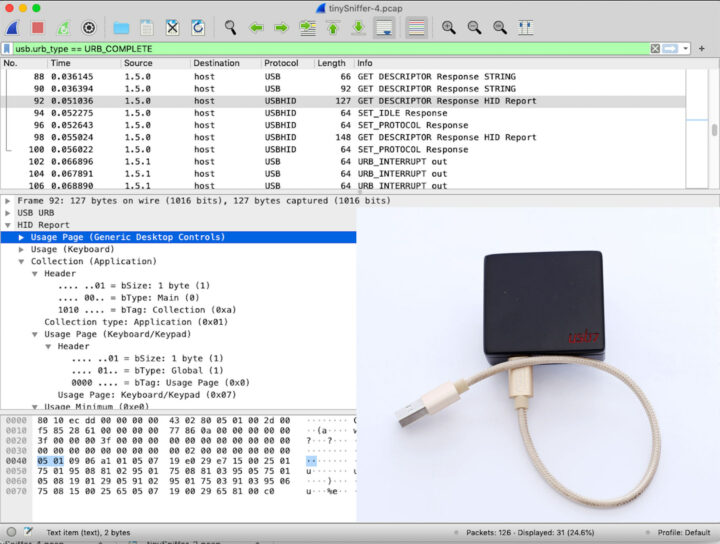
You can copy those to your computer and analyze them in Wireshark. Since it’s a software solution, I don’t think it captures all USB packets (including low-level ones), and the main advantage of the solution is remote access. More details can be found in the documentation.
Note the tinySniffer runs the tinyDebian Linux distribution that we first noted in an article a NanoPi NEO Air SBC modified with a dual-band WiFi module from the same company. Neither tinyDebian OS nor the sniff command appears to be open-source so you can’t replicate this USB sniffer if you already own a NanoPi NEO Air board.
There’s a significant markup for the tinySniffer compared to the $23 asked for the NanoPi Air NEO as it’s sold for $199 on Tindie, a pricing similar to FPGA-based USB capture solutions.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress






Lol trying to sell the open-source cloned solution as a product… I guess the license of the code doesn’t matter to some people.
Do you know which project it is? I have a pile of SBCs that could use a purpose 🙂
No, there is no existing open-source solution for this project. The author writes clearly in the article: neither tinyDebian OS nor the sniff command appears to be open-source
Please keep your facts straight.
No company is not required to give you the sources if you are not a customer, not even under GPL. There is no law against selling GPL-ed software, especially in combination with selling hardware.
There are 2 options the GPL works for you. Either software from your hand is being distributed or you obtained (bought) the product legally. If you are not the progammer or a customer the GPL is irrelevant. The GPL-sources must be distributed at cost, but:
“You may copy and distribute verbatim copies of the Program’s source code as you receive it, …” (Clause 1 from GPLv2.)
Most companies stay clear from this quagmire by selling “support” instead of “software”.
usbmon + tcpdump does the trick for free in linux, and if you need to monitor USB in Windows, run a VirtualBox instance.
Few scenarios where it’s not possible and it’s required a hardware solution.
True, but there are several FPGA-based USB capture solutions as well.