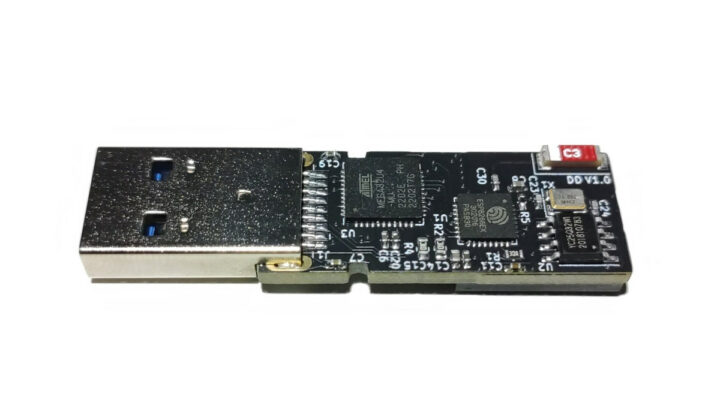
Diabolic Drive may look like a 64GB USB flash drive and show as such when you insert it into your computer, but it’s actually a wireless keystroke injection tool with a Microchip ATmega32U4 8-bit AVR microcontroller and an Espressif Systems ESP8266 WiFi SoC.
Egypt-based UNIT 72784 says their cyber security tool enables Red Teaming – the practice of rigorously identifying an attack path to breach a device’s security – as it behaves like a flash drive while being able to deploy keyboard strokes wirelessly through the ESP8266 WiFi MCU.
Diabolic Drive specifications:
- MCUs
- Microchip ATmega32U4 microcontroller @ 16 MHz (5V) acting as a Serial Bridge
- Espressif Systems ESP8266EX microcontroller @ 160 MHZ (3.3V) with WiFi 4 support
- ATmega32U4 and ESP8266 are connected via Serial and I2C protocols thanks to an LDO regulator.
- Storage
- 64 GB flash storage up to 20MB/s read, 10MB/s write
- 4MB W25Q32 SPI flash memory o
- Antenna – High gain 4.1 dBi ceramic chip 2.4 GHz wireless antenna
- USB – 1x USB 3.0 Type-A port for power and data like a standard flash drive
Both the Microchip ATmega32U4 and Espressif Systems ESP8266 are very popular microcontrollers that you can program with supported firmware (e.g. Arduino), but for cyber security testing, the developers suggest (Arduino) firmware such as WiFiDuck wireless keystroke injection attack platform or ESPloitV2 WiFi keystroke injection tool designed for an Atmega 32u4/ESP8266 paired via serial. Other firmware suggestions can be found on GitHub along with further technical details and documentation about the Diabolic Drive.
The Diabolic Drive is an especially bad boy since it can be hard to detect for an unsuspecting user because it’s compatible with many commercial USB flash drive enclosures, and while it exposes mass storage, HID device, and virtual COM port, it does so simultaneously, so that an operating system like Windows will only trigger an audio notification once like a normal flash drive.
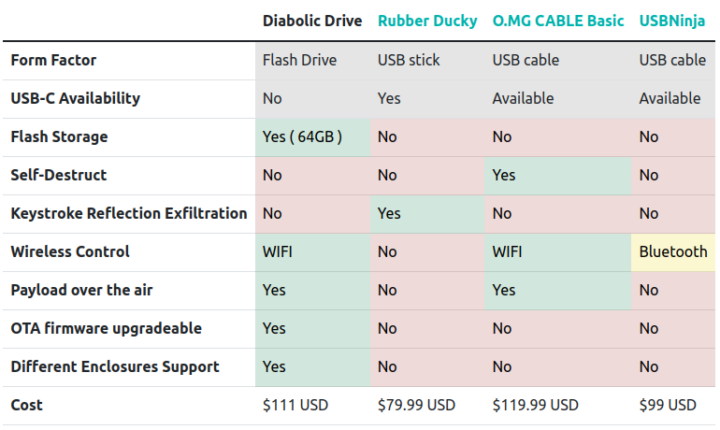
 UNIT 72784 has just launched the Diabolic Drive on Crowd Supply with a $10,000 funding target. There’s a single reward with the Diabolic Drive going for $111 with free shipping to the US, and $12 to the rest of the world. That feels quite expensive for the hardware involved, but it should be expected for this type of niche hardware, and other similar devices are in this price range too as shown in the table below. Delivery is scheduled to start at the very end of 2023.
UNIT 72784 has just launched the Diabolic Drive on Crowd Supply with a $10,000 funding target. There’s a single reward with the Diabolic Drive going for $111 with free shipping to the US, and $12 to the rest of the world. That feels quite expensive for the hardware involved, but it should be expected for this type of niche hardware, and other similar devices are in this price range too as shown in the table below. Delivery is scheduled to start at the very end of 2023.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress







Okay, many issues here. Let’s start with the hardware design. It’s crap. You have a USB-FS interface chip that’s hard to find and over priced (because it’s much loved in the arduino world and clones were sucking chips up). Then you have a separate WiFi chip that itself is well past its ‘sell by’ date and you have them connected by a serial link? As if the 12Mb/s of the FS-USB wasn’t slow enough.
Why not use use a ESP32S2 with native USB? It would cost less and take less board space–allowing you to use a better antenna design. Which is to say that those chip antennas are horrible. They’re little better than a 50 ohm resistor.
And then there’s the price. WTF? You could have this custom made by someone like JLCPCB in quantity *one* for a tiny fraction of that! The board layout is literally a simple afternoon project, so there’s no value there. Already uses Arduino for the software? No value there. What value are these guys bringing to the table?
Flash storage? No, I don’t know.. it’s just really bad.. and.. why WiFi? It’s not like you can connect to a company WiFi with this anyways. Or are you supposed to have a 4g-modem hidden somewhere too? I really don’t understand this product.
FWIW wifi can be quite discrete these days, given how many access points you find when scanning. So they just have to configure yet-another-one that seems totally innocuous and to connect to it from the street.
There’s always ESPnow which is a connectionless point to point protocol that uses WiFi type air transmissions to send small amounts of data–plenty for exfiltrating keyboard/mouse traffic with little exposure. No need for a constantly beaconing AP and none of the characteristic setup handshakes, etc. In other words, a lot less for a sniffer/IDS to see.
Then again, if they had used the ESP32S2, they’d have BT/LE which is even stealthier for a few reasons. One, it’s much harder to sniff because it was designed to be resistant to that. Two, because everything and its brother is on BT these days doing everything. A modern office must have 2-10 BT devices per occupant.
Hello and.elf 🙂 implementing a 4G modem is such a nice idea for individual to implement in that type of tools! could you please refer to WHID Elite ? taking a look on the PCB dimensions and consider it is only GSM-enabled not a 4G board .. Are you kidding me ? a tiny board with the dimensions of Diabolic Drive PCB with a 4G modem ?! then adding it to my kitchen to start cooking on it due to the heat generated from a 4G modem! and trust me this is the simplest problem you will face with that .. I’m afraid I’m not that cruel, I’m not coming from Mars and I have no aliens that can help me with that 🙂
Gotta say, as the author of one of the earliest wifi ducky tools (USaBUSe), I’m sad that 7 years has not brought any innovation in this space, beyond the OMG devices (form factor, USB and UX wise).
This is just “Meh!”, I’m afraid.
I held out hope that they had done something on the software features side, but the author seems to indicate that the hardware was designed to be as backwards compatable as possible–which doesn’t shout “we improved the software features”. Quite the opposite.
Hello Rogan .. with all of my respect to you 🙂 but after 7 years why you didn’t bring that innovation yourself ? was it that difficult ? or you just don’t care and you are waiting for someone to bring it and while this happens you are enjoying criticizing new ideas without getting hands on them to review them on reality ? also I’m wondering if you can help me with getting a true use case for an effective real world social engineering scenario to trick an adult to plug a USB cable to his laptop .. for me I can’t remember anytime beyond the era of Nokia Symbian phones I did that with a cable! with all my respect to the creator and all my appreciation of his hard and innovative work but even the cable is coming from Mars and made by aliens with bionic features still has very few social engineering scenarios to be used with .. it takes about 30,000 volts to transfer through the air per 1 centimeter distance while 1 volt can go through a tiny wire ( real world social engineering scenarios ) and get the job done effectively .. hope my thoughts are clear 🙂 and not forget to mention I’m considering building a unique software but it takes time cause I’m working on everything my own 🙂
Hello David 🙂 I think you are little hasty , the reason for using the Atmega32u4 and esp8266 is they have the widest community support and the widest variety of available firmware ready to use and easy to custom edit like WIFI duck , WIFI ducky , supreme Duck , Esploitv2 , WHID injector and much more and they are connected with each other via both Serial and I²C protocols to support almost any firmware exists for both chips .. hardware is still capable and can get the job of injecting wireless keystrokes easy and precisely .. Diabolic Drive is not about the wireless keystroke mechanism the value I’m bringing to the table is the 64 GB OF HS-USB 480 Mb/s flash memory that acts completely the same as a normal flash drive with writing speed of 12 Megabyte and reading speed of 22 Megabyte per second masking Diabolic Drive true use-case in a completely stealthy and unsuspecting way with Universal tiny PCB shape fits in many unsuspicious modern USB 3.0 Flash drive enclosures and regarding your opinion about the chip antennas I think you better test it on a Diabolic Drive before you judge cause I’m sure you will be surprised with the range and the performance 🙂 by the way neither esp32-s2 nor esp32-s3 was available for purchase in my country and still Diabolic Drive can do amazing job with that old hardware cause these chips role is limited and simple to wirelessly inject keystrokes .. if it’s available in your country you better go for one of them and build yours, but Diabolic Drive will always be the first to introduce this to the world and this is just version 1.0 I promise it will keep evolving with all the community support 🙂 and finally it took 270 simples after noon to complete.
How does the flash connect to the PC? You have one D+/D- set for USB HS and you have to share that with the 32U4, but there’s no hub on the board.
So, your hardware choice was to make it compatable with other people software, so no innivation on the software side, just a novel form factor with some storage grafted on.
And none of that justifies the cost.
Hello David 🙂 Would you mind subscribe to the Diabolic Drive campaign page on Crowd Supply to catch up with the upcoming updates instead of making blind judgments ? Diabolic Drive is double sides 4 layers PCB and trust me it’s not that simplicity you are expecting and FYI it already has HS USB hub chip on the bottom side alongside with other components and after all it gets what job it was designed for completely stealthy and regarding the software I’m considering building completely unique one my self but it takes time cause I make everything on my own and I didn’t want to waste extra time before releasing it but I intentionally made the hardware to be future proofed with the firmware I plan to build 🙂 may be by the beginning of 2024 it will be ready to rock and finally the pricing is within range with other useless tools with no effective real world social engineering scenarios also there are too many deductions of it as it’s a crowd funding project .. hope everything now is more clear to you and we are not fighting at all we are just discussing and having some arguments only 🙂