A few years go the Spectre and Meltdown hardware security vulnerabilities impacted a wide range of processors from Intel, AMD, Arm, and others. But a newly discovered hardware security flaw impacts specifically the Atom, Celeron, and Pentium from the Apollo Lake, Gemini Lake, Denverton … low-power processors we often feature on CNX Software.
Researchers have managed to activate test or debug logic at runtime for some low-power Intel processors, which they could use to escalate privilege, retrieve the “fuse encryption key” aka “chipset key fuse” unique to each processor, and access encrypted data. Most people do not need to panic though, as the hack would require physical access to the machine, and Intel says it is releasing firmware updates to mitigate the vulnerability. High-value targets should care though as the hack only takes 10 minutes, and if a laptop is stolen or lost, a skilled attacker should be able to access the content even if it is encrypted.
Intel issued an advisory for the vulnerability with a high severity rating and has released a firmware update and that’s mean the update will come from manufacturers. Considering how often UEFI/BIOS is updated by end-users, the vulnerability is likely to linger in many devices for years to come. Intel provides the list of impacted processors as follows:
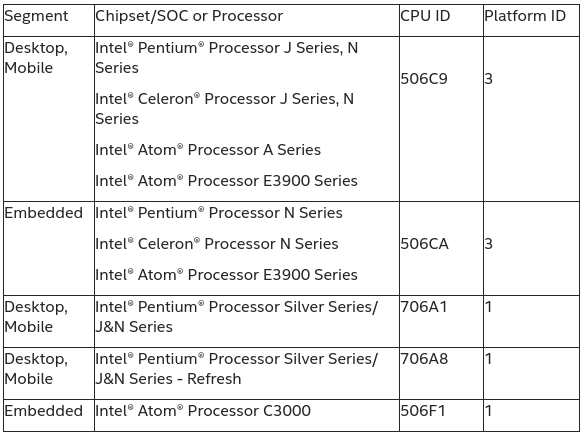 How this maps to an actual processor part is clear as mud to me. But you could check the CPU ID in Windows with AIDA64 or Intel’s own utility, while in Linux, I could run cpuid program in a terminal:
How this maps to an actual processor part is clear as mud to me. But you could check the CPU ID in Windows with AIDA64 or Intel’s own utility, while in Linux, I could run cpuid program in a terminal:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
cpuid | grep serial PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 PSN: processor serial number = false processor serial number = 0081-0F10-0000-0000-0000-0000 |
My laptop comes with an AMD Ryzen 7 2700U, and the CPUID is 810F10. Some website claim to have a list of CPU ID, but there are not easily searchable, so an option, if you don’t have the machine with you, is to download a recent Microcode Update Guidance to check the CPUID. For example, 706A8 CPU ID, Platform 1 corresponds to:
- Intel Pentium Silver J5040 Processor
- Intel Pentium Silver N5030 Processor
- Intel Celeron Processor J4125
- Intel Celeron Processor J4025
- Intel Celeron Processor N4020
- Intel Celeron Processor N4120
which are all Gemini Lake Refresh processors.
If you’d like more details about the hardware vulnerability itself, check out the CVE page (now mostly empty), Arstechnica article, or Positive technologies blog post from which reads in part:
One example of a real threat is lost or stolen laptops that contain confidential information in encrypted form … Using this vulnerability, an attacker can extract the encryption key and gain access to information within the laptop. The bug can also be exploited in targeted attacks across the supply chain. For example, an employee of an Intel processor-based device supplier could, in theory, extract the Intel CSME firmware key and deploy spyware that security software would not detect. This vulnerability is also dangerous because it facilitates the extraction of the root encryption key used in Intel PTT (Platform Trust Technology) and Intel EPID (Enhanced Privacy ID) technologies in systems for protecting digital content from illegal copying.
The automotive market could be impacted by the hardware security flaw too, as the Intel Atom E3900 Apollo Lake embedded processor is used by car manufacturers in more than 30 models, allegedly including the Tesla’s Model 3. The Atom C3000 Denverton processors are typically used in network appliances (e.g. firewall), so it may also be important to patch those as well.
Via Liliputing

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress






As security vulnerabilities go, this one is huge. So happy I have an N4020 Chromebook. 🙁
“Don’t worry, they have to have access to it.” Yeah, it’s currently at Asus for repair work. What could possibly go wrong?
@David Willmore: yes it is severe, but there is one of similar CVE severity level about every calendar year usually involving Intel ME or other Intel security layer, so it’s not new.
@Jean-Luc Aufranc: <<…Considering how often UEFI/BIOS is updated by end-users, the vulnerability is likely to linger in many devices for years to come…>>
You can also add the fact that SBC or SFF PC manufacturers are not the best adepts at releasing UEFI, BIOS or firmware updates often.
In the past I had to update the firmware of 9 Gemini Lake-based boards/boxes for an Intel ME severe security bug. They were from 3 different OEM. Only one of them included the Intel ME fix (Hard Kernel Odroid H2/H2+). The two others were still affected after the update.
means there will be no updates from most.
AFAIK Beelink mini pcs i own, celerons and atoms ones, never had any bios update.
and i update bios “semi-regularly” (whenever I distro-hop-linux-install, usually ever year or two).