The industry clearly has an issue at hand with the security of the Internet of Things, and the problem is complex as some devices are easily accessible due to bad configuration (e.g. default username/password), while others may have security flaws at various levels of the software stack from the low level bootloaders to the operating systems, and applications. Nowadays, devices also need to be upgradeable, and communicate with the cloud, and that introduces other attack vectors in case malignant firmware is installed instead, or a man-in-the-middle attack occurs.
While some people may claim security can be achieved by software only, we are seeing security evolving towards combined software and hardware solutions, for example with Arm Trustzone built into SoCs, but some companies are also introducing Secure Element chip, which Samsung has already done and integrated into their Artik modules to secure data from the hardware to the cloud.
NXP has now also launched their own A71CH Secure Element (SE), described as “a trust anchor, ready-to-use security solution for next-generation IoT devices, such as edge nodes and gateways”, and designed to secure peer-to-peer or cloud connections.
The A71CH provides the following key features:
- Protected access to credentials
- Encrypted/authenticated interface to host processor
- Certificate-based TLS set-up (NIST P-256)
- TLS set-up using pre-shared secret (TLS-PSK)
- Connectionless message authentication (HMAC)
- ECC key generation & signature verification
- Symmetric key derivation
- Encrypted vault for product master secrets (key wrapping, derivation, locking)
- Encrypted key injection
- Secure credential injection for root of trust at IC level
- Optional trust provisioning by NXP and qualified partners
- Temperature Range – Standard (-25 to +85 °C, A7101) and extended (-40 to +90 °C, A7102)
- Compact HVSON8 package
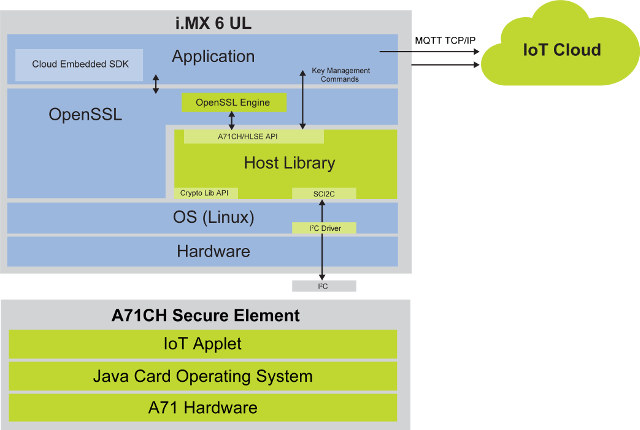
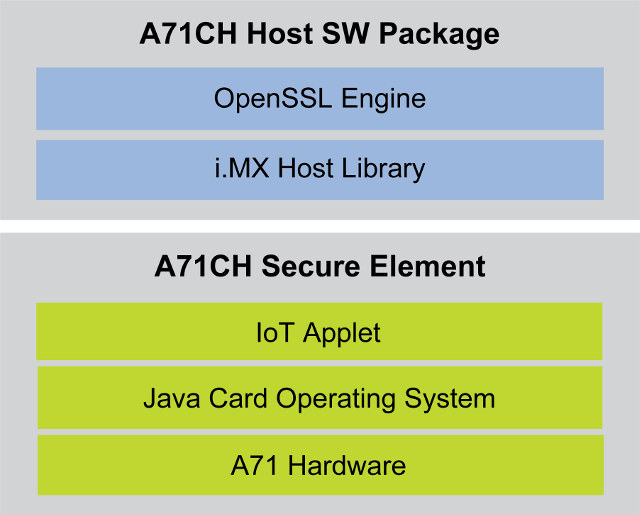
Beside the hardware itself, NXP provides the full software from the IoT applet and Java Card operating system running inside A71CH SE, to the OpenSSL engine and (i.MX & Kinetis) host library. The Secure Element is connected to the host processor via I2C, and the solution is supposed to be plug-and-play and let people securely connect to IoT clouds and services, such as AWS, without writing security code or exposing keys.
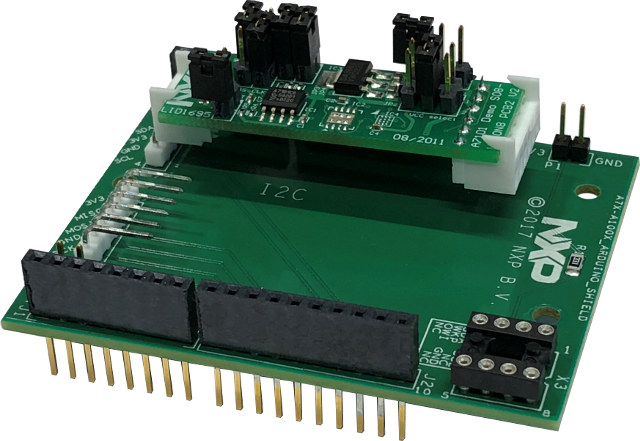
The company also provides OM3710/A71CHARD, an A71CH Arduino compatible development kit, that contains an A71CH-MiniPCB board connected to an Arduino Uno R3 compliant board through I2C male/female 4-pin strip connectors. The board can also take NXP A1006 secure authenticator device (contained in OM13589) to the same I2C bus, and works any NXP i.MX/Kinetis/LPC development board with Arduino compatible header. The documentation explains how to get started with the module, and an application notes goes into the details of electronic anticounterfeit protection with A71CH.
Both A71CH Secure Element and development kit appears to be available now (Status: Active), but no pricing has been made public. Visit the product pages for the chip and the devkit for the full details.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





All modern ARM Cortex class CPUs have this capability built in, even the Allwinner and Rockchip ones. But this chip is probably more resistant to having someone decap it and use an electron microscope to read a key out of secure storage. So if you are worried about that level of attack, then by all means get this chip.
This chip is also useful for all of the older CPUs that don’t have secure key storage.
@Jon Smirl
I can see i.MX 6UL already has Arm TrustZone, HW crypto, secure non-volatile storage, but NXP still uses ACH71 with i.MX 6UL, so it must bring something extra. Or is it just to be more resistant to actual hardware hacking as mentioned in the second sentence of your comment?
This is the special sauce….
Security licensing
NXP Semiconductors has obtained a patent license for SPA and DPA countermeasures from Cryptography Research Incorporated (CRI). This license covers both hardware and software countermeasures. It is important to customers that countermeasures within the operation system are covered under this license agreement with CRI. Further details can be obtained on request.
https://www.secureidnews.com/news-item/understanding-dpa-attacks-and-the-countermeasures-available-to-protect-smart-cards/
If you wanted to secure a SWIFT banking terminal processing millions in transactions, this chip is for you.
If you want to secure an IOT light bulb it is huge overkill.
@Jon Smirl
Speaking of bank cash machines, there is still the fake card reader and mini camera problem. I use my wallet to cover my hands as I enter my pin. And my point is they still have the human security risk in the system, but things are improving.