You may have heard a few things about Intel Management Engine in recent months, especially as security issues have been found, the firmware is not easily upgradeable, and the EFF deemed it a security hazard asking Intel for ways to disable it.
In recent days, I’ve seen several media reports about the Management Engine being based on an Intel Quark x86-based 32-bit CPU running MINIX open-source operating system. Keep in mind, there’s nothing nefarious about MINIX, it’s just that Intel keeps its own developments on top closed. One of sources for the information is a blog post explaining how to disable Intel ME 11, but ZDNET also points to one of the talks at the Embedded Linux Conference Europe 2017 entitled “Replace Your Exploit-Ridden Firmware with Linux” by Ronald Minnich, Google which explains the problem, and proposes a solution to (almost) disable Intel’s ME, and replace UEFI by a small open source Linux kernel and ramdisk.
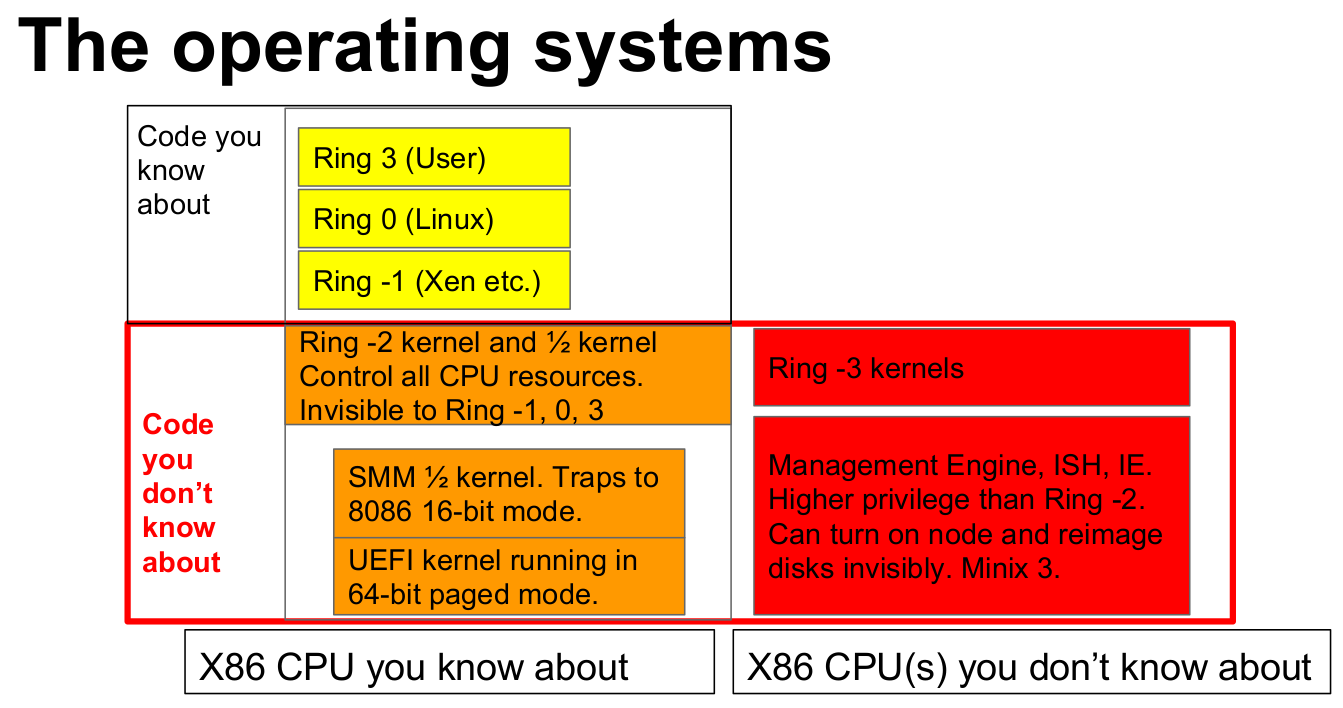
To better understand about the issue, we’ll first need to talk about rings… yes… rings. Protection rings with numbers from -3 to +3 indicate the level of privileges with Ring 3 being the lowest priviledge, and Ring -3 giving full access to all hardware. It’s unrelated to OS privileges and normal users and root are are part of the same Ring 3 privileges.
Ring 0 to 3 are well documented, Ring -1 is for hypervisors like Zen so “known to mankind”, but while we know something about Ring -2 CPU, the code for the UEFI kernel and SMM half kernel are not always known, and in the case of Ring -3 kernels which include the Management Engine, Integrated Sensor Hub (ISH), and Innovation Engine (IE) we know very little about the hardware and software, despite them having the highest privilege.
We do know the Management Engine Ring -3 OS provides the following features.
| Full Network manageability | ICC Over Clocking |
| Regular Network manageability | Protected Audio Video Path (PAVP) |
| Manageability | IPV6 |
| Small business technology | KVM Remote Control (KVM) |
| Level III manageability | Outbreak Containment Heuristic (OCH) |
| IntelR Anti-Theft (AT) | Virtual LAN (VLAN) |
| IntelR Capability Licensing | TLS |
| Service (CLS) | Wireless LAN (WLAN) |
| IntelR Power Sharing Technology (MPC) |
If you have no idea what some of the feature do, that’s OK, as even Richard is unclear. The important part is that the firmware has a full network stack, and web servers are running for remote management, which has recently become a serious problem as Intel found a vulnerability in “Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology” that can allow “an unprivileged attacker to gain control of the manageability features”. It requires a firmware update, but considering this affect Intel’s first to seven generation, the bug is at least 9 years old, and most systems won’t be updated. Read this PDF for a detailed (71 pages) security evaluation of Intel’s ME
Beside the Management Engine, the presentation also goes through Ring -2 OS (UEFI), an extremely complex kernel (millions of lines of code) running on the main CPU, and whose security model is… obscurity. UEFI exploits also exist, and can be made permanent since UEFI can rewrite itself. The firmware also always runs, and exploits are undetectable by kernels and programs.
The solution proposed to address the privacy and security issues related to ME and UEFI is called NERF (Non-Extensible Reduce Firmware).
 It’s only a partial solution because the system cannot fully boot without ME, but they’ve managed to reduce the size from 5MB to 300KB, removing the web server and IP stack in the process on Minnowboard MAX board thanks to me_cleaner. The SMM Ring -2 semi kernel can be disabled however.
It’s only a partial solution because the system cannot fully boot without ME, but they’ve managed to reduce the size from 5MB to 300KB, removing the web server and IP stack in the process on Minnowboard MAX board thanks to me_cleaner. The SMM Ring -2 semi kernel can be disabled however.
UEFI stands for Unified Extensible Firmware Interface, so to simplify the code and make it less vulnerable to exploits they’ve made their implementation NON-extensible, and as a result it’s much simpler, as illustrated in the diagram below.
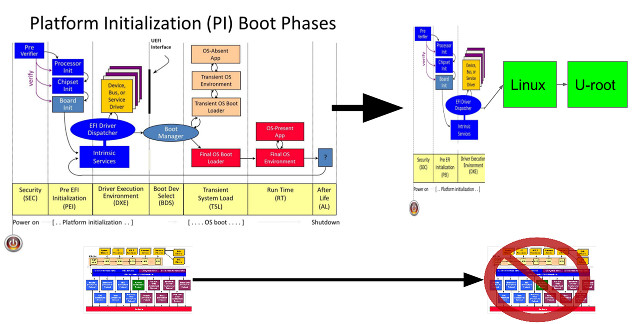
UEFI DXE stage is replaced with a single Linux kernel (tied to the BIOS vendor), and a 5.9MB firmware-based root file system written in Go (u-root.tk). If you are interesting in the details watching the 38 minutes ELCE 2017 presentation.

You may also be interested in the slides.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





when you look at it. the raspberry pi and its non-intel content is actually more secure….
i’d rather have an ARM or a MPIS etc…. than anything intel or AMD from now on!
Andrew S. Tanenbaum (Creator of MINIX 3) open letter to Intel:
http://www.cs.vu.nl/~ast/intel/
You managed to choose the only popular ARM device where situation is as bad as with Intel. The primary operating system on these boards is proprietary and runs on the VideoCore IV (euphemistically called ‘the firmware’), the ARM cores run a secondary OS that has no real control over the hardware.
RPi is really a bad example. Also this applies to lot of other ARM/MIPS which vendors who do not provide sources for their firmware/bootstrap code.
On the other hand APU2 (from PC engines) is x86/amd64 and yet it provides full source code (on request) to their BIOS. That’s IMHO best example. Another may be users modifying their x86/amd64 machines by uploading libreboot/coreboot to avoid Intel/AMD closed service processors bits…
@tkaiser
and, are you sure that at least some of the chinese arm soc’s does not have (hidden?) code “running” (listening) at the lowest level?
I will not trust Allwinner on this at all…
@cnxsoft
If they really are using Minix3 then they can at least help out upstream a little. When the EU reliable computing funds run dry, upstream was soon to follow and now the project is basically frozen. While the permissive license lets them get away with not giving back, by taking advantage of this now, Intel is basically shooting itself in the foot with regards to LLVM since now it won’t be long before someone releases their LLVM work as GPL to prevent Intel from taking advantage of them.
https://twitter.com/h0t_max/status/928269320064450560
Can this security issue be avoided by just using a pcie networks card?
LOL! https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00086&languageid=en-fr
If the ME has a driver for the NIC chipset, then NO.
E.g. Intel 82599 10G chipset has a special 1st stage filter function dedicated to Intel AMT traffic, therefore i reckon that it can be used by the Intel ME. I guess that a non mainstream (i.e. not Intel or Broadcom) USB NIC can be a good starting point if you want to avoid the issue.
“Keep in mind, there’s nothing nefarious about MINIX, it’s just that Intel keeps its own developments on top closed.”
The fact that Intel pays no thought to the security risk and possible government abuse IS A PROBLEM to a LOT of
people. Trying to soft peddle this buys you no friends sir….
@ss
MINIX is a fully open source project completely unrelated to Intel.