DEK Italia has recently introduced Telegea Smart Hub, an IoT gateway based on Raspberry Pi Computer Module 3 (CM3) with Ethernet, WiFi, RS232/485 ports, and various other I/O ports, that can leverage Raspberry Pi software ecosystem.
The company explains the device is mainly targeted at DIY home automation applications as a smart home controller which runs open source smart home software like OpenHAB and Home Assistant, but it can also be used for many other IoT applications.
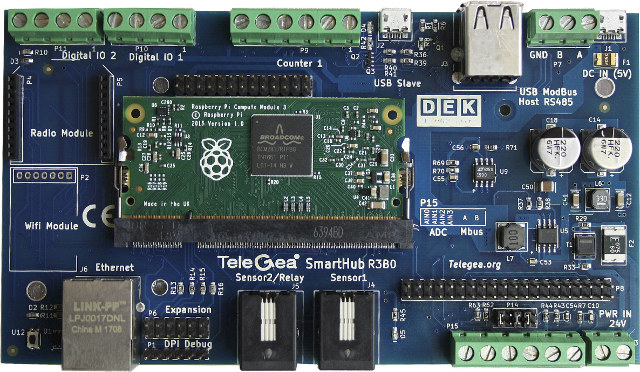
Telegea Smart Hub R3B0 specifications:
- SoC – Broadcom BCM2837 quad core Cortex A53 processor with VideoCore IV GPU
- System Memory – 1GB LPDDR2 RAM
- Storage – 4GB eMMC flash, 256 byte EEPROM
- Connectivity – 10/100M Ethernet port, optional Wifi 802.11 b/g/n at 2.4 GHz
- Serial – RS485 serial port, RS232 serial debug port
- USB – 2x USB 2.0 host ports
- Expansion
- 6xdigital inputs via screw terminals (for dry contacts or S0 interface)
- 4x analog inputs (0-5V) via screw terminals
- Dallas 1-wire bus via screw terminals
- 1x RJ14 connector for I2C bus peripherals
- 1x XBee module compatible connector for ZigBee and other RF modules
- 3x expansion headers with additional GPIO, SPI and I2C bus connections
- Sensor – SHT21 temperature and humidity sensor
- Debugging / Programing – 1x micro USB OTG port
- Misc – RTC with integrated battery, user button, user LED
- Power supply – 5VDC via micro USB connector; 24V DC / 24V AC via screw terminals
- Dimensions – 155 x 86 mm
The gateway supports a customized version of Raspbian Jessie Lite with Linux kernel 4.9.x and later. The changes to Raspbian include enablement of clock generation for integrated Ethernet bridge on GPIO pin, UART ports for RS485 connector and serial debug port, drivers for RTC/ADC/EEPROM/ I2C relay card, configuration of the 1-wire bus on screw terminals, and installation of GPIO handling command line tools and Zulu Embedded OpenJDK VM. You’ll find source code, hardware and software documentation on Github, and get support on Telegea Google Groups.

The boards has been designed to fit into a commercial Camdenboss CNMB/9 DIN rail enclosure as shown above, in which case the model is called TSH-CM R3B0.
Telegea Smart Hub R3B0 board is sold on eBay without the Raspberry Pi module for 179.00 Euros, while the TSH-CM R3B0 modle with DIN rail enclosure and RPi CM3 module goes for 219.00 Euros. The complete kit is also sold on Tindie for $249.99. Visit the product page for more information.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





Hope they patch the Wifi security issue http://www.bbc.co.uk/news/technology-41635516
@theguyuk
Hope people mentioning Wifi security issues would understand those. Throwing around with insecure http links is really somewhat stupid given that one of the KRACK issues is that affected devices can get malware ‘injected’ by nearby attackers over any http link. Better refer to https://www.krackattacks.com instead since the BBC link above contains a flash movie which could be considered insanely stupid in this context (security vs. flash player)
And to try to get a little bit on-topic again. One of the few reasons to rely on such a Raspberry Pi compute module and Raspbian is that there exists excellent upstream security support. Just like Debian Raspberry folks provide a patched wpa_supplicant package: http://archive.raspbian.org/raspbian/pool/main/w/wpa/
Here we go again…
In the lack of better arguments, you mix two different things, and in that process you also label as stupid all the IT people from BBC… great! 🙂
For ages it is know that, if you are *serious* about security, you will never use wi-fi.
Wi-fi will never be safe, now and ever.
I m amazed by a too easy to fail OS device when device propose only few Gpio/Analog input.
An ESP8266 / ESP32 will be more reliable and more easy to update and it’s not forbidden to put an remote Raspbbery pi to help ESPXXX in calculation
As expected you missed the ‘in this context’ part and I was not talking about BBC (IT) staff though their CTO could be called irresponsible still allowing http and putting their readers at risk. You as the one calling Jean-Luc’s switch to TLS here in the blog and readers warning about irresponsibly connecting Windows XP to the Internet in 2017 STUPID (emphasis by you) will not be able to understand this. But it’s really simple…
The current KRACK WPA2 vulnerabilities lead to your own wireless network being as insecure as ‘the Internet’ behind. It allows others physically close to you to hijack your network connection in your local network as it’s currently more or less only possible in the Internet for 3 letter agencies — a web search for ‘finfly isp’ should help with understanding.
Now with these KRACK vulnerabilities being known anyone near to you can insert packets into your Wifi connection as long as you use insecure (http) connections. Connections that use an additional security layer (https/TLS) are not affected.
So if I want to inform others about a potential security problem making them vulnerable to visiting HTTP links providing such a HTTP link pointing to an article using a flash video is just… $whatever (everyone interested in his own IT security has deleted the flash player long time ago since this https://www.cvedetails.com/vulnerability-list/vendor_id-53/product_id-6761/Adobe-Flash-Player.html is just insane!)
Tkaiser, i’m sure your intentions are good – to warn people – but your reasoning is still weak.
I can destroy your arguments phrase by phrase, but will focus on this:
if you are just a regular, nobody of interest, internet user, why on earth your neighbour would want/like to inject packets into your home wi-fi, spy on you? how he/she will have both the computing power and the deep skills needed to do that?
Unless you are currently editing the North Korea nuclear documents, no one will have any interest on you.
But then, if you’re doing illegal, or even non-ethical things over your wi-fi, you have bigger problems, right?
The point is that the chance of a regular John Doe be hacked via wi-fi interception is almost negligible, and should worry no-one. You have much bigger risks with what you eat or when you drive your car around.
If you are concerned about your data, use cable, or just turn on your wi-fi router when you need. Wi-fi will never be secure, that is an illusion, it was designed from the ground up to have backdoors, so that governments intelligence officials could sleep well.
And also… don’t share and expose your thoughts and privacy on facebook, google gmail (use pgp, please), windows 10, etc…… 😉
Instead of waiting for the others to make you “feel safe”, just do your own homework.
(and yes, I still use XP on a old pentium 4 – mostly on winter, it helps to keep the room warm ;-), without any antivirus, no problems ever, and smile when friends tell me “wow, this is faster than my core 2 duo, etc.” )
Ha, and yes, CNX has made a poor choice both when moving to https and with the TLS level.
but, i know, google ranks rules….
I’m not concerned about KRACK that much. It’s a huge mess from a software design point of view but the practical impact for individuals is currently pretty low, especially for people who use additional encryption layers (that’s the HTTPS vs HTTP thing for example you still seem to not understand).
KRACK will become a problem in another area and that’s IoT devices that don’t receive upgrades. To turn surveillance cameras or IoT devices into parts of botnets attackers now don’t need those devices being openly accessible from the Internet but they can explore/own them automatically by ‘war driving’.
And again to get back on topic: A device like this here which relies on the RPi Compute Module (which I would consider a pretty weird choice from a hardware point of view) clearly has an advantage in this context when relying on Raspbian hopefully with unattended-upgrades activated. Since it will be patched automagically unlike other IoT devices relying on less popular SoCs and ‘distros without upgrades’ leaving them vulnerable to such exploits.