I’ve just read an interesting article entitled “who makes the IoT things under attack“, explaining that devices connected to the Internet such as router, IP cameras, IP Phones, etc.. may be used by Botnet to launch DDoS attacks, and they do so using the default username and password. So you may think once you’ve updated the firmware when available, and changes the default admin/admin in the user interface, you’d be relatively safe. You’d be wrong, because the malware mentioned in the article, Mirai, uses Telnet or SSH trying a bunch of default username and password. That made me curious, so I scanned the ports on my TP-Link wireless router and ZTE ZXHN F600W fiber-to-the-home GPON modem pictured below, and installed by my Internet provider, the biggest in the country I live, so there may be hundred of thousands or millions of such modems in the country with the same default […]
How to Use an ESP8266 Board as a WiFi to Serial Debug Board
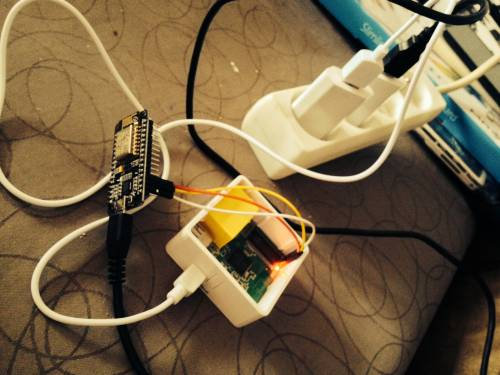
Telnet and SSH are great to access a Linux device, machine and computer remotely when they are already running, but when you are working on the bootloader and/or kernel themselves, you’ll have to use a serial port to access the terminal / serial console. Boards used to get an RS232 port which you connected to your computer with a NULL modem cable, but these days, most boards and devices expose TTL signals and require a USB to TTL debug board to access the console via a USB cable. If you only have one device close to you computer that’s fine, but if your testbed is a little further. or you need to access the serial console on multiple boards you could consider using ESP8266 module to export the terminal over WiFi. This is exactly what Zoobab did above with a GL.inet router running OpenWRT and NodeMCU board with ESP-12(E) module […]
Linux Based Zsun WiFi Card Reader Has Been Hacked Too…
A little while ago, I purchased Zsun SD111 W-Fi USB flash drive, and after several tentatives, I finally found a way to access the device’s serial console. Since then the company announced another wireless storage device with Zsun Wi-Fi card reader, and Zoobab decided to try to hack it too. Since the device is pretty hard to open without damaging the enclosure, connecting the serial pin was not really an option, and the first exploit was to input shell commands in the web interface SSID field… For example, entering reboot there, would indeed reboot the device. However, this would still not allow full shell access, and finally after a broader port scan, it was found out that TCP port 11880 was open for telnet daemon. You can then access the shell as root with the same password as SD111: “zsun1188”. For some reasons, telnet can’t work with the device, and […]