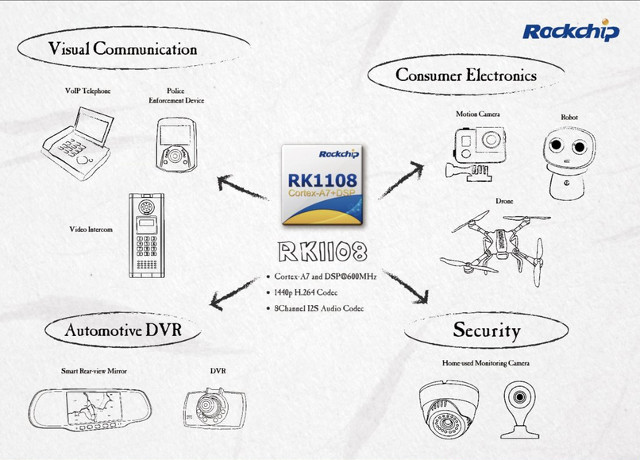
[Update May 2017: Rockchip has renamed RK1108 to RV1108.] Rockchip has introduced RV1108 ARM Cortex A7 SoC with a 600 MHz DSP targeting visual communication, consumer electronics, automotive DVR, and security applications thanks to its 8-channel I2S audio codec and 1440p H.264 video encoder and decoder. Detailed specifications can be found on the official Rockchip Wiki: CPU – Single-core ARM Cortex-A7 Core processor with NEON and FPU, 32KB/32KB L1 I-Cache/D-Cache, Unified 128KB L2 Cache, and Trustzone Video/Image DSP – Up to 600 MHz, 32KB I-TCM and 32KB I-cache, 128KB D-TCM Memory 12KB internal SRAM DDR3/DDR3L interface – 16 Bits data width, 1 ranks (chip selects), up to 512 MB RAM NAND Flash Interface – 8-bit async NAND flash, 16-bit hardware ECC eMMC Interface – Compatible with standard iNAND interface, eMMC 4.51 standard. SD/MMC Interface – Compatible with SD 3.0, MMC 4.41 System Component 2x 64-bit timers with interrupt-based operation 8x […]
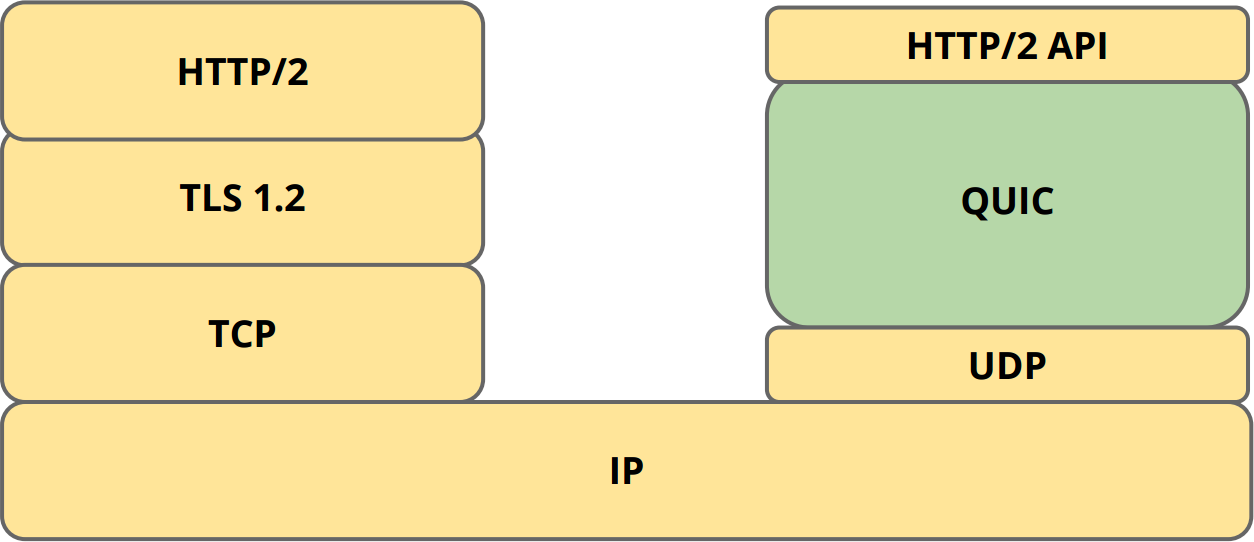
Google QUIC is a Secure UDP Protocol Aiming to Replace TCP + TLS
A lot of traffic over the Internet goes through secure https connections. Under the hood this requires a 3-way handshake to establish a TCP connection, followed by even more packets exchanged between the client and server to negotiate TLS in order to establish a secure connection. Google is now working one the new experimental QUIC protocol that uses the “send and forget” UDP protocol, together with its own crypto, and its own way to making sure the connection is properly establish. The whole idea about QUIC is to reduce the effect of latency (e.g. ping time) by exchanging less messages to achieve the same secure connectivity. For example, if there’s a 200ms latency between a server and a client, and if a TCP connection requires 4 packets, while a QUIC/UDP connection requires only 1 packet, you’ll save about 600ms. One downside with UDP according to Jim Roskind, designer of QUIC, […]
Embedded Linux Conference & IoT Summit Europe 2016 Schedule
Embedded Linux Conference & IoT summit 2016 first took place in the US in April, but the events are now also scheduled in Europe on October 11 – 13 in Berlin, Germany, and the schedule has now been published. Even if you are no going to attend, it’s always interesting to find out more about the topic covered in that type of events, so I had a look, and created my own virtual schedule with some of the sessions. Tuesday, October 11 10:40 – 11:30 – JerryScript: An Ultra-lightweight JavaScript Engine for the Internet of Things – Tilmann Scheller, Samsung Electronics JerryScript is a lightweight JavaScript engine designed to bring the success of JavaScript to small IoT devices like lamps, thermometers, switches and sensors. This class of devices tends to use resource-constrained microcontrollers which are too small to fit a large JavaScript engine like V8 or JavaScriptCore. JerryScript is heavily […]
Wanscam HW0029-4 is a Solar Powered All Weather IP Security Camera with WiFi, 3G/4G Connectivity
I’ve just watched a video on ARMDevices.net about Enlaps Tikee solar powered device designed to take timelapses over several days and transfer the pictures / video over WiFi, 3G, or 4G. The project has been fully funded on Indiegogo at the beginning of the year, and shipping is scheduled for Q4 2016. It looks like an interesting device for a niche market, but since I’ve noticed some products launched on Kickstarter already exists in one form or another in China, I’ve decided to have a look on Aliexpress, and I found Wanscan HW00269-4 solar powered camera with 3G/4G connectivity, and while it addresses a completely different need, as a 720p IP security camera, I still decided to have a closer look. Wanscam HW0029-4 specifications: SoC – Hisilicon Hi3518E ARM9 processor @ 440 MHz Storage – Built-in 16GB, expandable to 128GB Camera / video recording 1/2 1MP Star light CMOS sensor 8mm […]
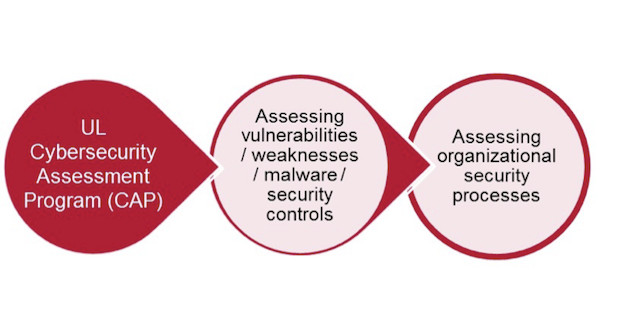
UL Goes Beyond Electrical Safety with UL 2900 IoT Security Standard
UL is a company providing testing and safety certifications with electrical, building, fire, mechanical and other codes to ensure products sold to consumers and companies are as safe as possible, and follow their UL standards. For example, you should probably look for the UL logo on any 100~240V electrical appliances, power supplies, etc… to make sure you purchase safe products, and also in order to avoid voiding any insurance you may have in case of fire. The company is now getting into cybersecurity, specifically for IoT security, with UL 2900 standard. The standard is currently divided into three parts: UL 2900-1 – Outline of Investigation for Software Cybersecurity for Network-Connectable Products, Part 1: General Requirements UL 2900-2-1 – Outline of Investigation for Software Cybersecurity for Network-Connectable Products, Part 2-1: Particular Requirements for Network Connectable Components of Healthcare Systems UL2900-2-2 – Outline of Investigation for Software Cybersecurity for Network-Connectable Products, Part […]
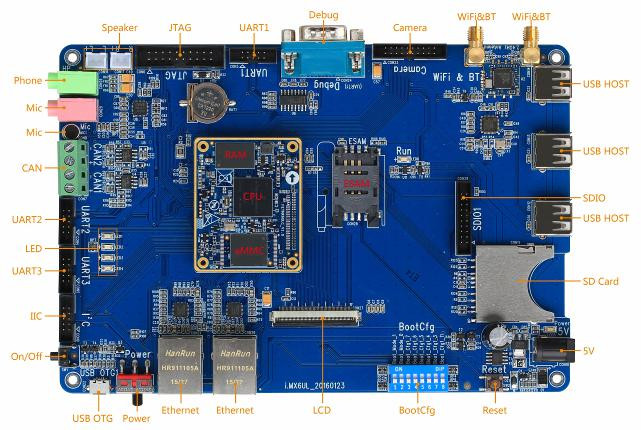
Forlinx i.MX6UL Linux Single Board Computer Supports ESAM Embedded Security Control Module
Forlinx Embedded has introduced i.MX6UL single board computer (SBC) based on NXP i.MX 6Ultralite Cortex A7 processor with 512 MB RAM, 8GB storage, that includes two Ethernet interface, an LCD interface, a CAN bus, as well as ESAM (Embedded System Access Module) support via either a SIM card like slot, or a 8-pin DIP chip compatible with ISO7816 standard, and typically used in the financial, telecommunications, transportation sectors for authentication and secure data transfer. Forlinx I.MX6UL board specifications: System-on-module: SoC – NXP i.MX 6Ultralite ARM Cortex A7 processor @ up to 528 MHz with 2D graphics GPU System Memory – 512 MB LvDDR3 memory Storage – 8GB eMMC flash (but hardware manual says 1GB eMMC flash, but also mentioned MTFC8GACAAAM-1M WT so it must 8GB after all…) 2x 80-pin board to board connectors with signals for 2x CAN bus, 2x USB device, 2x SDIO, 2x 10/100M Ethernet, 24-bit RGB, 4x […]
BusyBotNet is a Fork of Busybox with Security Tools
Busybox provides a lightweight version of common command line utilities normally found on “big” Linux into a single binary, in order to bring them to embedded systems with limited memory and storage. As more and more embedded systems are now connected to the Internet, or as they are called nowadays the Internet of Things nodes, adding security tools, such as cryptographic utilities, could prove useful for administrators of such system, and so BusyBotNet project wsa born out of a fork of Busybox. Some of the tools implemented include: fenc to encrypt stuff with salsa algo tsh. needs work, backdoor shell aes enc rathole backdoor shell, blowfish enc ssyn2 ddos tool sudp udp ddos tool jshon sh wrapper for json hydra prism userspace icmp triggered reverse shell backdoor You can access the source code and instructions on busyboxnet github repo. I’ve quickly tried it in my AMD x86 computer running Ubuntu […]
Upcoming ARM TrustZone Webinars Explaining Embedded Systems / IoT Security to Non-security Experts
Most people understand that securing the IoT is important, but security is a highly a complex subject, and as seen with the many security breaches, even specialists – who in theory should now better – get their devices or online accounts hacked. So even if you are not a security expert, but are involved in the development of embedded systems, it’s important to get acquainted with online and offline security and understand how all this all work, at least from a high level perspective, without necessarily having to dig into the technical details. ARM is organizing two webinars catering to people who are not security experts, and explaining how they can secure embedded systems using the company’s TrustZone technology. The first webinar entitled “How to build trust and security into your embedded device” will allow participant to gain an understanding of the security that will need to be applied in […]