Arm TechCon will take place on October 8-10, 2019 at San Jose Convention Center to showcase new solutions from Arm and third-parties, and the company has now published the agenda/schedule for the event. There are many sessions and even if you’re not going to happen it’s always useful to checkout what will be discussed to learn more about what’s going on currently and what will be the focus in the near future for Arm development. Several sessions normally occur at the same time, so as usual I’ll make my own virtual schedule with the ones I find most relevant. Tuesday, October 8 09:00 – 09:50 – Open Source ML is rapidly advancing. How can you benefit? by Markus Levy, Director of AI and Machine Learning Technologies, NXP Over the last two years and still continuing, machine learning applications have benefited tremendously from the growing number of open source frameworks, tools, […]
Winston Privacy Filter Lets You Browse the Web Anonymously, Ad-free & Tracking-free (Crowdfunding)
More and more people are worried about their privacy online, so products and solutions aiming to protect people against tracking, targeted ads, cookies, and various other threat have been popping up. Fingbox and Firewalla are such devices, but their hardware may be limited, and software solutions like PiHole are also an option, but may not be suitable for everyone. Winston privacy filter is another plug-and-play solution, but based on an actual network processor, namely a Marvell ARMADA dual core Arm Cortex-A53 SoC, that should make sure your network performance is not impacted, and even provides a boost of performance for most visited websites due to the resources that are being blocked out. Winston “privacy filter” hardware specifications: SoC – Marvell ARMADA dual core Arm Cortex-A53 processor @ 1.0 GHz with security and data acceleration engines System Memory – 1GB DDR4 @ 800 MHz Storage – TBD Networking – Dual Gigabit […]
Reolink Argus Eco Review – A Sub-$100 Solar Powered Security Camera
I’ve been thinking about installing one or more IP camera in my home for a while, and for ease of installation and considering I’m renting, my preference was to go with one of those battery IP cameras similar to Amazon (Immedia) Blink IP camera or Eufy EverCam security camera that last six months to one year on a single charge. But earlier this year I came across Reolink Argus 2 battery powered security camera that looks like good value at $100, and also came with an optional solar panel so you don’t have to ever charge the camera. The company latter contacted me to know whether I’d be willing to try out their latest Reolink Argus Eco camera with similar features but an even lower $89.99 price tag. I got my sample a few weeks ago, and I had time to install it, and play around with the camera during […]
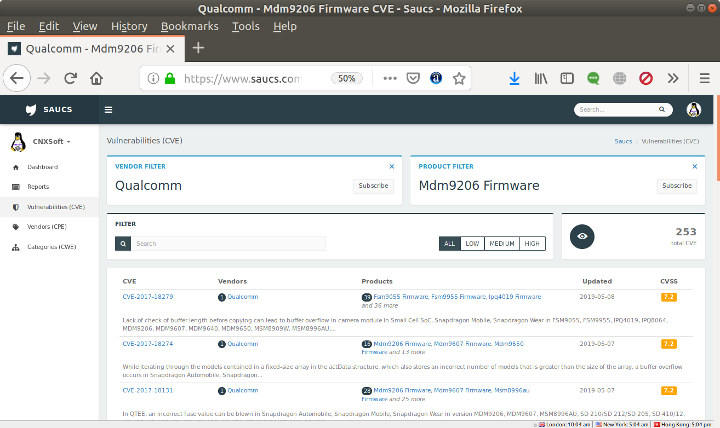
SAUCS is a Search Engine for Security Vulnerabilities (CVE Database)
Every so often we hear about critical security vulnerabilities in the news, but new ones are actually discovered daily, so it would be nice to have some sort of search engine to find out which known security vulnerabilities a given product or processor may have before purchasing it, or even more importantly starting a project. SAUCS does just that by having robots checking out the CVE update list, parsing the XML feed and formatting it. You can search for products or process, or subscribe to the vendors and products you want, and receive an email as soon as new changes as detected. I found out about SAUCS thanks to a comment from Thomas who pointed out the Qualcomm MDM9607 processor found in Quectel EC25 LTE module had a fairly long list of CVE (Common Vulnerabilities and Exposures) entries while using the default? firmware as shown in the screenshot above. Each […]
Embedded Linux Conference & Open Source Summit 2019 Schedule
In the last few years, I covered the Embedded Linux Conference and IoT Summit schedules since both were happening at the same time and in the same location. But the Linux Foundation have recently announced the Embedded Linux Conference will combine with the Open Source Summit, so the IoT Summit appears to have been phased out. The full schedule for the events taking place on August 21 – 23, 2019 at the Hilton San Diego Bayfront, USA, has also been released, so I’ll create a virtual schedule with some of the sessions most relevant to this blog. Wednesday August 21, 2019 11:30 – 12:05 – What’s New with U-Boot? by Simon Glass, Google LLC U-Boot is a widely used bootloader in embedded systems. Many users are unaware of the wide feature-set of U-Boot, particularly features added in the last few years. This talk aims to bring users (and prospective users) […]
More Intel Processor HW Security Flaws. Meet Microarchitectural Data Sampling (MDS)
2018 did not start so well for processor vendors, especially Intel, but also AMD, Arm and others as some of their processors leveraging speculative execution were impacted by Spectre and/or Meltdown hardware security bugs. The workarounds to improve security had a downside as they affected performance in some specific use case. Panic ensued as the bug was revealed to the public a bit too early, so companies were not fully ready with their mitigations / workarounds. Then in summer of 2018, another hardware security flaw known as Foreshadow or L1 Terminal Fault came to light. The new flaw potentially enabled the attacker to access data stored in L1 cache. Provided you have updated your operating systems to the latest version, your computers and devices should be protected against those vulnerabilities, and you can even check with a script working in Linux or FreeBSD. But this now looks like a never […]
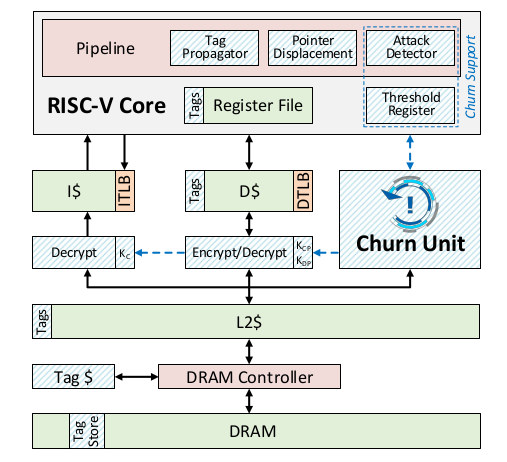
MORPHEUS Claims to be an Unhackable RISC-V Processor Architecture
Code gets continuously written and updated for new features, optimizations and so on. Those extra lines of code sometimes come at a cost: a security bug gets inadvertently introduced into the code base. The bug eventually gets discovered, a report is filled, and a software fix is committed to solve the issue, before the new software or firmware to push to the end user. This cycle repeats ever and ever, and this means virtually no software or device can be considered totally secure. The University of Michigan has developed a new processor architecture called MORPHEUS, and that blocks potential attacks by encrypting and randomly reshuffling key bits of its own code and data several times per second through a “Churn Unit”. The new RISC-V based processor architecture does not aim to solve all security issues, but focuses specifically on control-flow attacks made possible for example by buffer overflows: Attacks often […]
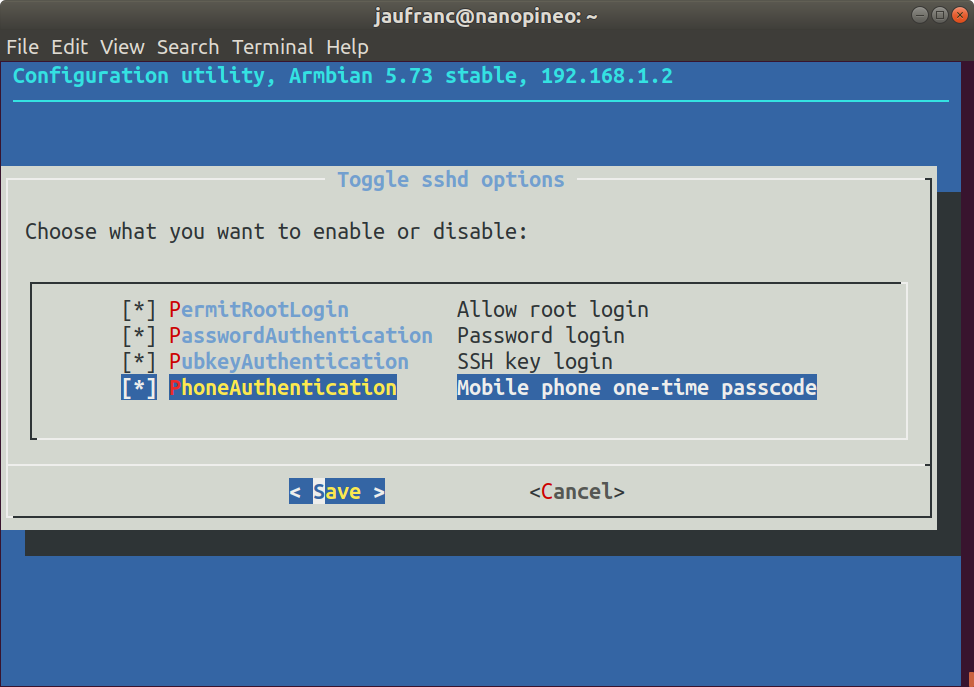
Enabling Two-Factor Authentication for SSH Access in Armbian
Until today, I only knew of two authentication methods for SSH: the traditional username/password and key-based login with private/public keys with the latter being more secure and not requiring any password. But I’ve just found out it’s also possible to login to SSH using two-factor authentication relying on your smartphone to get an OTP code like you would to access some banking services as it can easily be enabled in Armbian. First you’ll want to enable key-based login with private/public keys, or you won’t be able to access your board anymore after enabling 2FA except via the serial console. Now simply start armbian-config, and go to System Settings->Reconfigure SSH daemon to enable PhoneAuthentication “mobile phone one-time passcode”. We’re not done yet, so don’t close Armbian-config You’d then need an Android or iOS phone running Google Authenticator app to receive the OTP (one-time password). After enabling PhoneAuthenticator in armbian-config, you’ll see […]