Now a lot of the traffic on the Internet is secure, and for example, if you visit this blog your traffic will be encrypted, so your ISP, government or hackers will not know which exact page you visit on the website. But unless you use a VPN or the Tor Network, they’ll still know/or find out you visited CNX Software as most DNS requests are now unencrypted. Hackers may also use a spoofed DNS to steal your credit card info while you think you input your details into a trusted website. Beside using a VPN service, one solution is to use DNS over HTTPS (DoH) which encrypts the DNS request so that even your ISP or the government (unless there’s a backdoor) may not know which websites you visit. On top of improving privacy, DoH also improves security, as it’s harder to spoof DNS servers and by extension internet websites. […]
USB Armory Mk II USB Linux Computer Targets Security Applications (Crowdfunding)
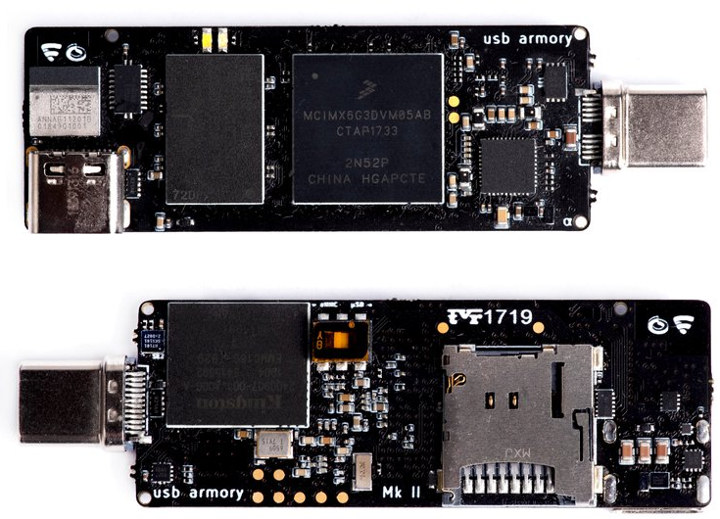
Back in 2014, Inverse Path launched USB Armory computer dongle running headless Linux from a MicroSD card and designed for security applications. The company got bought by F-Secure Foundry in 2017, and the latter has now launched another crowdfunding campaign for an upgraded version USB Armory Mk II keeps a similar USB dongle form factor but replaces the NXP i.MX53 Cortex-A8 processor with a more efficiency NXP i.MX 6ULZ Arm Cortex-A7 processor, the USB type-A port with a modern USB-C port, adds 16GB eMMC flash, Bluetooth 5 LE connectivity, and new security features. USB Armory Mk II specifications: SoC – NXP i.MX6ULZ Arm Cortex-A7 @ 900 MHz System Memory – 512 MB DDR3 RAM Storage – 16 GB eMMC flash + external microSD Connectivity – Bluetooth 5 LE + mesh module (U-blox ANNA-B112) with Arm Cortex-M4 MCU (nRF52832) USB – 2x USB type-C ports: 1x DRP (Dual Role Power) receptacle […]
Signet High-Capacity Thumbdrive Supports 2FA, Password & Secure Data Storage (Crowdfunding)
Signet HC Crowdfunding Started The latest version of the Signet thumbdrive is the Signet HC. The HC has a number of enhanced features and a lower price point, making it an attractive alternative to other high-security flash drives. The drive is high capacity storage, with secure storage technology, 2 Factor Authentication (2FA) token and encryption. It also has a password manager and enhanced database features. The company has started its crowdfunding campaign and there are several device quantity options and peripherals. Features of the Signet HC The Nth Dimension has announced the Signet HC recently, bringing to the forefront of its latest device, the all-in-one aspects of the drive’s capabilities. The Signet HC is certainly positioned to be one of the top featured, encrypted password protected, and 2FA storage devices of its size. The data on the drive is encrypted, and password protected and can be accessed through cross-platform […]
PhyWhisperer-USB Python Controlled USB 2.0 Sniffer Enables USB Security Testing (Crowdfunding)
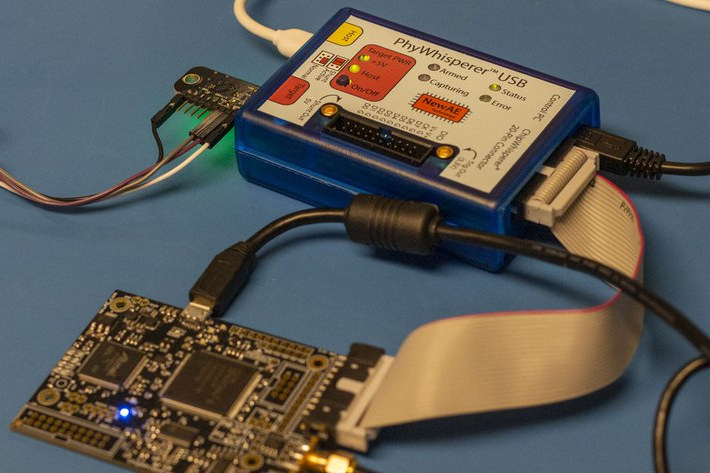
PhyWhisperer-USB is a hardware USB sniffer & triggering platform that allows users to test the security of USB devices using side-channel power analysis and fault injection using a Python 3 interface, beside simply capturing packets. This has become especially important now as some USB devices include Bitcoin Wallets, FIDO2 keys, and encrypted drives with valuable data. PhyWhisperer-USB hardware specifications: FPGA – Xilinx Spartan 7S15 with 12,800 logic cells USB USB 2.0 Low/Full/High Speed mode PC connection – Micro-USB 2.0 HS port Host connection – Micro-USB port Target connection – USB-A female connector Trigger pattern – 1 – 64 bytes with mask Trigger delay – 0 – 1048576 cycles of 240 MHz internal clock derived from USB clock USB sniffer FIFO – 8192 bytes (FPGA block RAM, adjustable depending on FPGA utilization) Expansion – Spare digital I/O: 8 data pins, 1 clock pin routed to FPGA (on front panel) Clock output […]
Linaro Connect San Diego 2019 Schedule – IoT, AI, Optimizations, Compilers and More
Linaro has recently released the full schedule of Linaro Connect San Diego 2019 that will take place on September 23-27. Even if you can’t attend, it’s always interested to check out the schedule to find out what interesting work is done on Arm Linux, Zephyr OS, and so on. So I’ve created my own virtual schedule with some of the most relevant and interesting sessions of the five-day event. Monday, September 23 14:00 – 14:25 – SAN19-101 Thermal Governors: How to pick the right one by Keerthy Jagadeesh, Software Engineer, Texas Instruments With higher Gigahertz and multiple cores packed in a SoC the need for thermal management for Arm based SoCs gets more and more critical. Thermal governors that define the policy for thermal management play a pivotal role in ensuring thermal safety of the device. Choosing the right one ensures the device performs optimally with in the thermal budget. […]
Somu Tiny Open Source FIDO2 Security Key Enables Passwordless Login & Two-factor Authentication (Crowdfunding)
Tomu is a tiny, open source USB connector-sized board powered by a Silicon Labs Happy Gecko Cortex-M0+ MCU that adds two keys to your computer and can work as a Universal 2nd Factor (U2F) token to support two-factor authentication (2FA). But the board is not secure enough for FIDO2 support, and Tomu’s developer worked on a secure USB key called Solokey, and shrank it to Tomu form factor. Meet Somu open-source and secure key with FIDO2 support for compatibility with your Google, Twitter, and GitHub accounts for two-factor authentication, or your Microsoft account passwordless login. Somu hardware specifications: Secure MCU – STMicro STM32L432KC Arm Cortex-M4 microcontroller with TRNG, security isolation for keys, two levels of locked flash Crypto Algorithms – ECC P256 (as per FIDO2 standard) Supported Protocols – FIDO2, U2F Host Interface – USB type-A port Misc – Two touch buttons ( in FIDO2 firmware the two buttons behave […]
Group Theoretic Cryptography (GTC) Offers an Alternative to TLS’s ECC/RSA Security for Microcontrollers
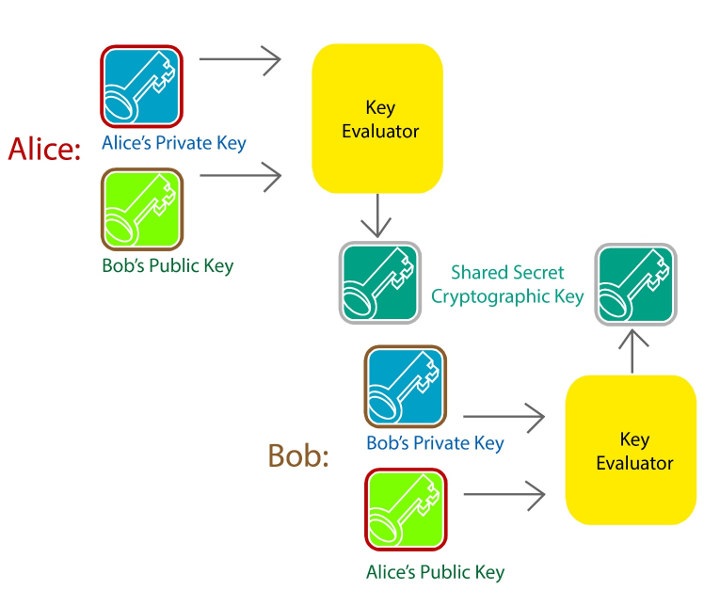
The Transport Layer Security (TLS), sometimes incorrectly referred as its predecessor: Secure Sockets Layer (SSL), helps securing messages over the network using symmetric cryptography, and optionally public-key cryptography (aka asymmetric cryptography). This works well in servers and computers, but with the Internet of Things, even low-power sensor nodes would benefit from secure communication. The trouble is that today’s commonly-implemented RSA- and Diffie-Hellman-type public-key protocols have a memory footprint that will not fit on resource-constrained microcontrollers systems, e.g. Arm Cortex-M0 based ones, and power consumption may also be an issue since many of those are battery-powered. I’m writing about this topic today, as there may be a better alternative for resource-constrained microcontrollers which I noticed in Arm Techcon 2019 schedule, with SecureRF Corporation’s session entitled “When it comes to connect IoT devices, how small is small?” that will present an alternative to TLS’s ECC and RSA based security that relies on […]
Ameba Z2 IoT Board Features Realtek RTL8720CM Armv8-M KM4 Secure Wireless MCU
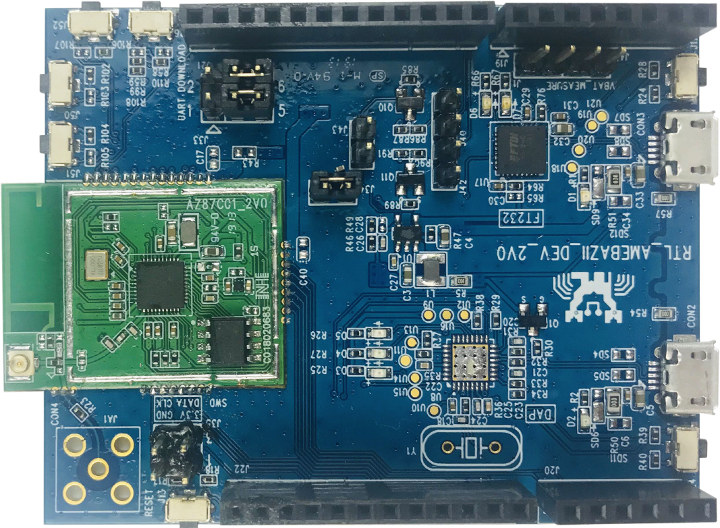
In 2016 we discovered Realtek Ameba wireless microcontrollers combining an Arm Cortex-M3 core with WiFi connectivity, and that could potentially become an ESP8266 competitor with modules selling for as low as $2. But the solution never really took off, because it was about the same price as ESP8266, and the latter already had a solid software ecosystem and community. But RealTek has now introduced a new Ameba Z2 IoT development board powered by RTL8720CM microcontroller featuring an Armv8-M KM4 core clocked at 100 MHz. What’s an Arm KM4 core you may ask? Seeed Studio informed me Arm and RealTek worked together on the KM4 core, so it looks like a custom Armv8-M microcontroller. Ameba Z2 IoT Development Board Ameba Z2 (ZII) specifications: Wireless MCU – Realtek RTL8720CM single core Armv8-M KM4 core @ 100MHz with 4.2MB internal RAM, WiFi and Bluetooth radios Storage – 2MB external flash on module Connectivity […]