Developer and engineer Oliver Fabel has developed a port that is designed to run MicroPython on the Flipper Zero. This port allows users to write programs for Flipper Zero in Python, instead of built-in JavaScript. Till now you can access GPIO, ADC, PWM, the speaker, buttons, the display, and infrared communication with this but it doesn’t have support for NFC or RFID yet, and it’s still under development. Previously we have written about various addon boards for the Flipper Zero like the Mayhem v2, the ESP8266 Deauther board, the CAN bus addon board, and other powerful alternatives of the Flipper like The M1 and the HackBat. Feel free to check those out if you are interested in the topic. The process is simple, and you don’t have to do a firmware update to work with MicroPython, you can download the application from the community-driven Flipper app store and are good […]
Mayhem v2 expansion for Flipper Zero adds Wi-Fi, BLE, camera, microSD card slot, and NRF24 or CC1101 radio support
Erwin Ried‘s Mayhem v2 is an all-in-one ESP32 and NRF24L01-based expansion board designed for Flipper Zero. This board adds Bluetooth and Wi-Fi through an ESP32-S module, features 2MP camera with flashlight, a microSD card slot, and support for either an NRF24L01 module (for sniffing and mousejacking) or a CC1101 module (for external radio communication). These features make this Flipper Zero add-on board useful for WiFi and Bluetooth penetration testing, motion detection, QR code reading, and as a nanny cam with remote access. Previously we have written about similar expansion boards like the Flipper Zero ESP8266 Deauther which adds de-authentication capabilities and the Flipper Add-On CANBus which can be used to sniff, send, and log CAN bus packets directly from the Flipper Zero. Feel free to check those out if you are interested in those tools. Mayhem v2 Flipper Zero add-on board specification Wireless Module – ESP32-S WiFi 802.11 b/g/n + […]
nRFBOX V2 ESP32 wireless hacking tool can scan, analyze, spoof, and jam the whole 2.4GHz spectrum
CiferTech has recently introduced the nRFBOX V2 ESP32-based wireless hacking tool designed for spectrum analysis, jamming, BLE device emulation, and more. The device is built around an ESP32-WROOM-32U module and includes an NRF24 module covering the whole 2.4GHz spectrum. Additionally, the device has a 0.96-inch OLED display, a five-way microswitch control pad, and a WS2812 RGB LED for feedback. The device can also be operated with a single 3.7V lithium battery, and that batter’s charging is handled by a TP4056 charging IC. All these features make this device useful for wireless security testing, educational environments, research, and hobbyist projects. Previously we have written about similar portable hacking tools like the DSTIKE Deauther Watch X, the HackBat pen-testing device, and the popular Flipper Zero wireless hacking tool. Feel free to check those out if you are looking for similar products. nRFBOX V2 specifications Microcontroller – ESP32-WROOM-32U with ESP32 dual-core wireless microcontroller […]
Flipper Zero hacking tool gets ESP8266 Deauther add-on for Wi-Fi security and research
PCB Studios has just launched the “Flipper Zero ESP8266 Deauther” adapter board for Flipper Zero that enables users to conduct de-authentication attacks on Wi-Fi networks. Running a modified version of SpacehuhnTech’s ESP8266 Deauther software, this board has a variety of actions for testing 802.11 wireless networks. Its primary function, deauthentication, sends deauthing packets to the target network, disconnecting devices from their 2.4 GHz Wi-Fi networks. In our last post about Flipper Zero, we wrote about Flipper Add-On CANBus a CAN bus hacking tool that can sniff, send, and log CAN bus packets. Other than that we have seen similar tools like the M1 multitool and HackBat which can be considered as Flipper Zero alternatives with STM32H5 and Raspberry Pi RP2040 MCUs and Wi-Fi connectivity. We have also written about various ESP8266 and ESP32-based Deauther tools like the DSTIKE Deauther Watch X, the Cheap Evil Tech Deauther board, and ESP32 Marauder […]
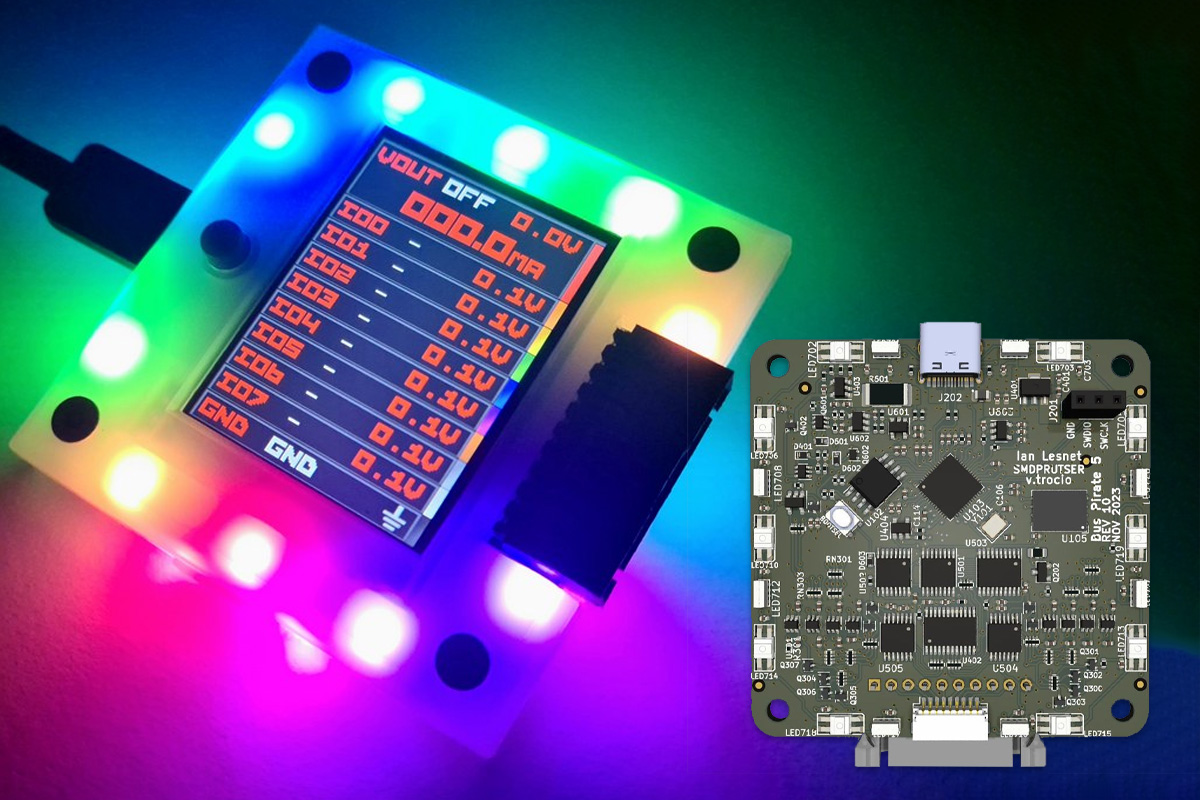
Bus Pirate 5XL and 6 hardware debugging tools utilize Raspberry Pi RP2350A and RP2350B microcontrollers
The Bus Pirate 5XL and 6 are open-source hardware debugging tools respectively based on Raspberry Pi RP2350A and RP2350B and designed to simplify interaction with various bus protocols like 1-Wire, I2C, SPI, UART, several LEDs, and more. The idea is to send commands to a chip or sensor and get the response, without writing a single line of code making it ideal for hardware hacking and tinkering. The devices feature buffered I/O pins with voltage and current measurement, a programmable power supply with current limiting, an RGB LCD for pin status and info, and an auxiliary header for connecting logic analyzers. All these features make this device useful for applications like debugging circuits, prototyping projects, and reverse engineering devices. The new devices are updates to the Bus Pirate 5 based on Raspberry Pi RP2040 MCU. You’ll find Bus Pirate specifications for the three models in the table below. The original […]
Flipper Zero hacking tool gets CAN bus add-on board for vehicle diagnostics and security research
Electronic Cats’ Flipper Add-On CANBus is a new add-on board for the Flipper Zero adding CAN bus communication to the popular wireless hacking tool. Built around the MCP2515 CAN controller chip this add-on card communicates with the Flipper Zero through an SPI interface. It allows users to sniff, send, and log CAN bus packets directly from the Flipper Zero, which means now you can analyze and manipulate CAN bus traffic for vehicle diagnostics, security research, and DIY projects. Previously we have seen Flipper Zero add an RP2040-powered video game module, and before that, we noted the developers launched their own app store with open-source apps. Additionally, we have written about Flipper Zero alternatives such as the M1 multitool so feel free to check those to know more about those solutions. Electronic Cats Flipper Add-On CANBus specifications Compatibility – Flipper Zero CAN Controller – Microchip MCP2515 CAN bus controller with SPI […]
Minino ESP32-C6 board is designed for IoT security and penetration testing
Minino security tool is a kitty-shaped ESP32-C6 powered cybersecurity device for analyzing 2.4GHz communications and probing IoT devices. It supports Bluetooth Low Energy, Wi-Fi 6, Zigbee, Thread, and Matter, and has a dedicated GNSS radio for receiving signals from various satellite constellations. Minino is compatible with CatSniffer analysis tools and Wireshark software, and can log packet captures on a microSD card. These features make this suitable for applications like assessing IoT device security, network analysis, and wireless protocol research. We have previously written about similar IoT security and pen testing tools like the ESP8266 and ATmega32U4-based Diabolic Drive, the ESP32 Marauder Pocket Unit v2, the ThingPulse Pendrive S3, and many others, feel free to check those out if you are interested in the topic. Minino security tool specifications Wireless Module – ESP32-C6-WROOM-1U SoC – ESP32-C6 CPU Single-core 32-bit RISC-V clocked up to 160 MHz Low-power RISC-V core @ up to […]
The ESP32 Marauder Pocket Unit v2 is a wireless penetration device with an onboard GPS module and touchscreen
The ESP32 Marauder Pocket Unit with GPS v2 is a portable Wi-Fi and Bluetooth penetration tool powered by an ESP32 module and used to test and analyze wireless networks. It features a 2.8-inch touchscreen, two 18650 batteries, an SD card slot, an LED battery indicator, and two external antennas for 2.4GHz Wi-Fi and GPS. ESP32 Marauder Pocket Unit v2 specifications: Microcontroller – ESP32 Wi-Fi & Bluetooth SoC Storage – MicroSD card slot for file sharing, backup, and firmware updates (8GB SanDisk memory card included) Display – 2.8-inch capacitive touchscreen USB – USB-C port for charging GNSS – Embedded GPS module Antenna – External dual antenna SMA connectors for WIFI and GPS Misc 1x battery status indicator Reset and Power buttons Power – 2x 18650 batteries Dimensions – 92 x 71 x 46mm The ESP32 Marauder device is based on JustCallMeKoko’s ESP32Marauder Project, a suite of Wi-Fi/Bluetooth offensive and defensive tools […]