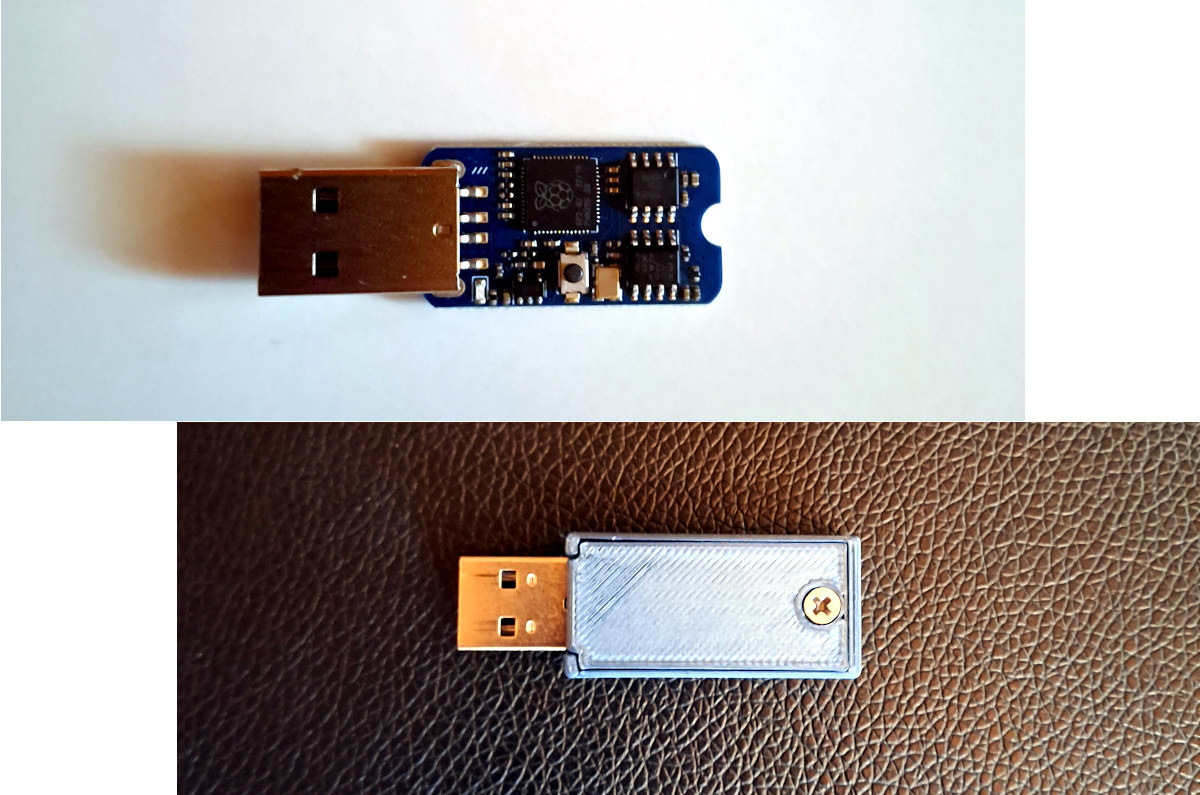
Machdyne’s Blaustahl is a USB storage device equipped with a Raspberry Pi RP2040 MCU and 8KB of FRAM with a potential lifespan of over 200 years and designed for long-term storage of text up to about 8,000 characters. FRAM (Ferroelectric RAM) has been around for years delivering ultra-low power consumption, faster writes, and ultra-long write endurance (one million billion read/write cycles) compared to EEPROM or NOR flash, but the cost is quite higher and it’s mostly used in applications that require ultra-low power consumption and non-volatile storage write capabilities such as data logging, sensor networks, batteryless applications. The Blaustahl storage device and USB text editor is one of those. Blaustahl speciications: Microcontroller – Raspberry Pi RP2040 dual-core Cortex-M0 processor at 133MHz and 264kB RAM. Storage 4MB (32Mbit) NOR flash for firmware 8KB (64Kbit) FRAM (Fujitsu MB85RS64) Lifespan – 95 years @ +55°C, over 200 years @ +35°C Endurance – 10^12 […]
The New IoT Device Security Specification 1.0 unifies various standards into one
The Connectivity Standards Alliance has recently introduced its IoT Device Security Specification 1.0, a way to defragment many security standards into one. This common scheme and certification standard will ensure that devices meet local requirements in each country. With this approach, a single test from the alliance ensures that the product can be sold globally without any compliance issues. IoT Device Security Specification 1.0 at a glance: Unified Security Standard – Integrates the major cybersecurity baselines from the United States, Singapore, and Europe into one comprehensive framework. Product Security Verified Mark – A new certification mark that indicates compliance with the IoT Device Security Specification, designed to enhance consumer trust and product marketability. No Hardcoded Default Passwords – Ensures all IoT devices utilize unique authentication credentials out of the box, improving initial security. Unique Identity for Each Device – Assigns a distinct identity to every device, crucial for traceability and secure […]
Kryptor FPGA – Tiny MAX10 FPGA board works as a hardware security module (Crowdfunding)
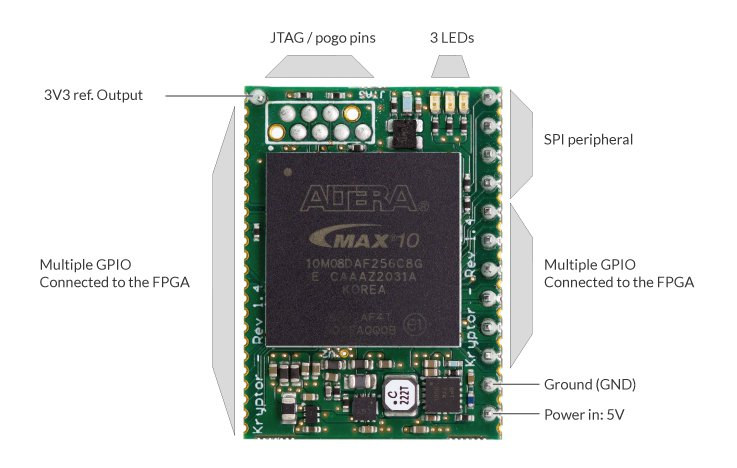
Kryptor FPGA, sometimes just called Kryptor, is a compact Intel/Altera MAX10 FPGA development board mostly designed for encryption, and acting as a dedicated Hardware Security Module (HSM) with a custom soft-core from Skudo OÜ. But obviously, you could also use the FPGA board for other purposes. Hardware encryption can be quite more secure than software-based encryption with reduced attack surfaces, especially since data processing can be done in the FPGA RAM. The HSM can be used to encrypt files, videos, emails, IoT messages, etc… from various hardware platforms including Arduino and Raspberry Pi boards. Contrary to closed-sourced commercial solutions, the soft-core is open-source and as such can be verified by third parties to make sure there aren’t any backdoors or security flaws. Kryptor FPGA specifications: FPGA – Intel/Altera MAX10 8K LE ( 10M08DAF256C8G) FPGA @ 100 MHz with 8000 logic elements (LE), 1376 Kb flash, 378 Kb total RAM, up […]
Linux 5.8 Release – Main Changes, Arm, MIPS, and RISC-V Architectures
Linus Torvalds has just released Linux 5.8: So I considered making an rc8 all the way to the last minute, but decided it’s not just worth waiting another week when there aren’t any big looming worries around. Because despite the merge window having been very large, there really hasn’t been anything scary going on in the release candidates. Yeah, we had some annoying noise with header file dependencies this week, but that’s not a new annoyance, and it’s also not the kind of subtle bug that keeps me up at night worrying about it. It did reinforce how nice it would be if we had some kind of tooling support to break nasty header file dependencies automatically, but if wishes were horses.. Maybe some day we’ll have some kind of SAT-solver for symbol dependencies that can handle all our different architectures and configurations, but right now it’s just a manual […]
Seeeduino Crypto Board Combines Microchip ATmega4809 MCU and ECC608 Crypto Chip
With the advance of IoT, security has become critical since devices are often connected to the Internet. There are several ways to improve security and one of them is to implement hardware security via crypto chips. One of those chips is Microchip ECC608 (aka ATECC608A) secure element which we previously found in Linux based hardware such as USB Armory MK-II USB Linux computer, and the official Arduino Nano 33 IoT Board. Seeed Studio has now introduced a new Arduino compatible board with Microchip ECC608 crypto chip: Seeeduino Crypto board powered by a Microchip ATmega4809 8-bit AVR MCU. Seeeduino Crypto specifications: MCU – Microchip ATMEGA4809-AFR 8-bit AVR microcontroller @ 16 MHz with 48KB flash, 6,144 Bytes RAM USB – 1x USB Type-C port Expansion Arduino Uno headers with 6x analog inputs, 14x digital I/O pins, 5x PWM 2x I2C Grove headers 1x UART Grove header HW Security – Microchip ECC608 secure […]
Linux 5.0 Release – Main Changes, Arm, MIPS & RISC-V Architectures
Linus Torvalds has just released Linux 5.0: Ok, so the last week of the 5.0 release wasn’t entirely quiet, but it’s a lot smaller than rc8 was, and on the whole I’m happy that I delayed a week and did an rc8. It turns out that the actual patch that I talked about in the rc8 release wasn’t the worrisome bug I had thought: yes, we had an uninitialized variable, but the reason we hadn’t immediately noticed it due to a warning was that the way gcc works, the compiler had basically initialized it for us to the right value. So the same thing that caused not the lack of warning, also effectively meant that the fix was a no-op in practice. But hey, we had other bug fixes come in that actually did matter, and the uninitialized variable _could_ have been a problem with another compiler. Regardless – all […]
Linux 4.6 Release – Main Changes, ARM and MIPS Architectures
Linus Torvalds released Linux Kernel 4.6 earlier today: It’s just as well I didn’t cut the rc cycle short, since the last week ended up getting a few more fixes than expected, but nothing in there feels all that odd or out of line. So 4.6 is out there at the normal schedule, and that obviously also means that I’ll start doing merge window pull requests for 4.7 starting tomorrow. Since rc7, there’s been small noise all over, with driver fixes being the bulk of it, but there is minor noise all over (perf tooling, networking, filesystems, documentation, some small arch fixes..) The appended shortlog will give you a feel for what’s been going on during the last week. The 4.6 kernel on the whole was a fairly big release – more commits than we’ve had in a while. But it all felt fairly calm despite that. Linux 4.5 added […]
AES-256 Encryption and File names encryption with 7-Zip (7z)
If you need to safely backup some of your confidential files (email, financial info, marketing info, source code,…), you can use 7-Zip (aka 7z) to compress and encrypt your archive with AES-256 as well as hide the name of the files. This should give you the level of security used by the (in-)famous insurance file (insurance.aes256) released by Wikileaks last year (if it indeed has been encrypted with AES-256). 7-Zip is available for Windows, Linux (multiple architectures) and Mac OS. Since 7-Zip source code is open, it can theoretically be ported to any platform. The first thing I did was to use a Password Generator to get a 256-bit key such as DFF61FFB56B26158718457E5E47F3511080130C855C8E6F689A3A7664EBE2C9A. In this example, I backup “My Documents” directory in Windows, but the same command line (just different paths) could be used in Linux as well:
|
1 |
C:\>"c:\Program Files\7-Zip\7z" a -t7z mydoc_backup_22022011.7z "C:\Documents and Settings\Jean-Luc\My Documents" -xr!*BitTorrent*\ -xr!*Cache*\ -pDFF61FFB56B26158718457E5E47F3511080130C855C8E6F689A3A7664EBE2C9A -mhe -v4480m -mx9 |
Here’s the description of the parameters in the command line: a […]