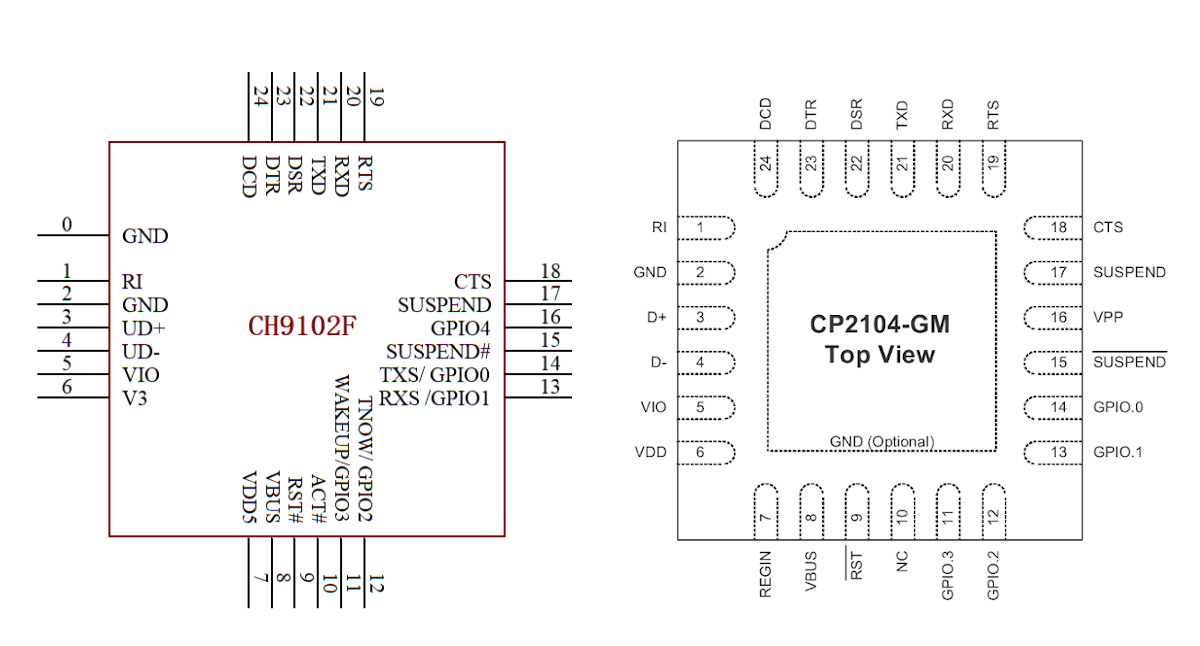
I’ve just mentioned Silabs CP2104 USB to UART chip price had increased, and indicated WCH CH9102F chip could be used as an alternative instead in a post about LILYGO T-Display boards. I had never heard about CH9102 chips before (CH9102F and CH9102X), so I decided to investigate a bit more by checking out both CH9102 and CP2104 datasheets. The good news is that CH9102F and CP2104 have basically both the same pinout albeit with some small differences that may or may not matter depending on the application, and come in a 4x4mm 24-QFN package (4x4mm) meaning if you run out of CP2104 chips, CH9102F can be used as an alternative, and should be a drop-in replacement. CH9102X is pretty similar to CH9102F but offered in a 5x5mm 28-QFN package with extra GPIOs. Back to the main contenders… According to LILYGO, one of the differences between CH9102F and CP2104 is the […]
Cynthion board enables USB Hacking through Lattice ECP5 FPGA (Crowdfunding)
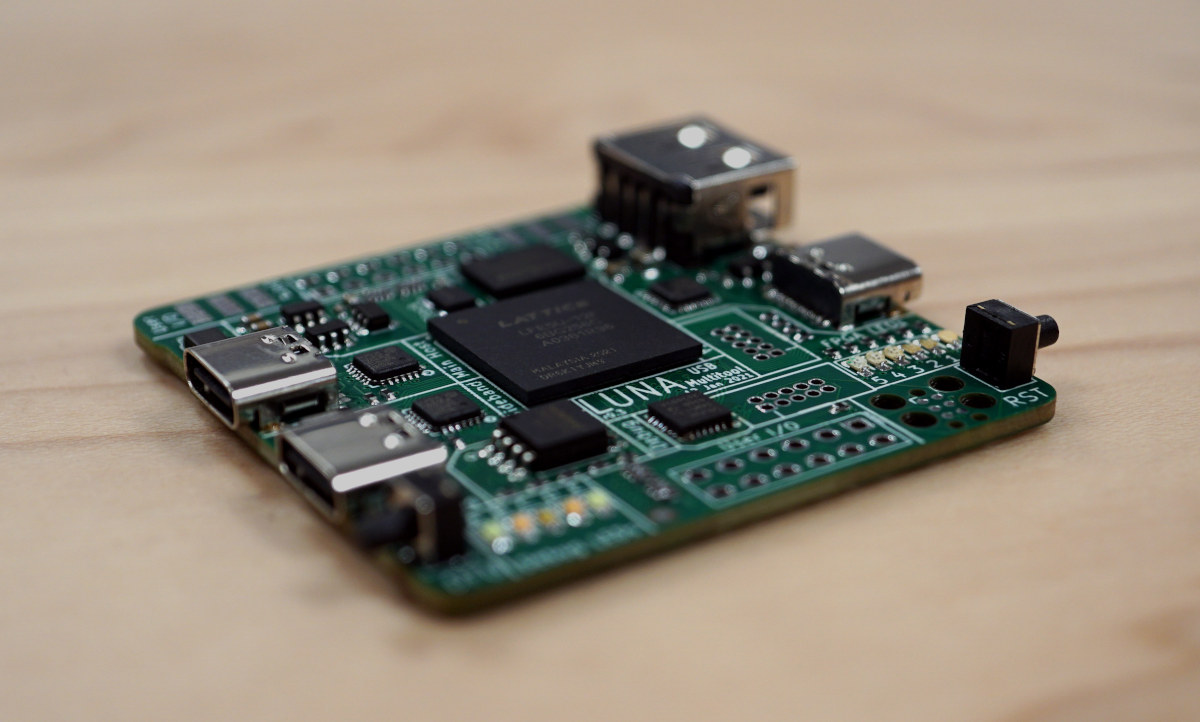
Update 16/02/2023: The LUNA board has been renamed to Cynthion, but the gateware framework continues to be called LUNA. Several USB hacking/debugging boards were launched in 2020 either based on microcontrollers or FPGA with the likes of Tigard (FTDI FT2232HQ), Ollie (STM32F042), Glasgow Interface explorer (Lattice Semiconductor iCE40), or Protocol Droid (STM32). All those were launched on Crowd Supply, and there’s now another one with LUNA “multi-tool for building, analyzing, and hacking USB devices” based on a Lattice Semiconductor LFE5U-12F ECP5 FPGA that raised over $100,000 in a few days. Cynthion hardware specifications: FPGA- Lattice Semiconductor LFE5U-12F ECP5 FPGA with 12K LUTs System Memory – 64 Mbit (8 MiB) RAM for buffering USB traffic or for user applications Storage – 32 Mbit (4 MiB) SPI flash for PC-less FPGA configuration USB – 3x High-Speed USB interfaces, each connected to a USB3343 PHY capable of operating at up to 480 Mbps. […]
PC-based Logic Analyzers Comparison: PGY-LA-EMBD vs Logic16 Pro vs SP209
Building an embedded system requires multiple devices to communicate with the central processor, generally through an SPI or I2C bus. If your system is quite complex and things don’t work out as expected, then a Logic Analyzer might save your day. So, choosing the correct Logic Analyzer is critical to a successful project. This article gives a PC-based Logic Analyzers comparison, and we’ll compare products from three companies: Prodigy Technovations, Saleae, and Ikalogic. Factors to keep in mind while selecting a Logic Analyzer Before we dive into the comparison part, we should be aware of a few points based on which we’ll compare them. Logic analyzers come with a certain number of channels. The higher the number of channels is, the costlier is the product. So, select the number of channels appropriately depending on the size of your project. Several other technical specifications should also be considered, which are listed […]
$3.5 RV-Debugger Plus UART & JTAG debug board comes with BL702 Zigbee & BLE RISC-V SoC
USB to UART debug boards are a necessity for anyone playing with single board computers, at least when using bleeding-edge bootloader or Linux kernel where the target board may not always boot, or when troubleshooting booting problems. Those are often based on FDTI or WCH chips, but Sipeed RV-Debugger Plus features Bouffalo Lab BL702 Zigbee & Bluetooth LE RISC-V SoC instead and offers both UART and JTAG interfaces. So let’s have a look at both the board and SoC. Sipeed RV-Debugger Plus USB to TLL debug boards are meant to be simple and that’s the case for Sipeed latest BL702 board as it comes with a 12-pin connector with Tx/Rx for UART, 8 signals for JTAG, plus 5V, 3.3V, and GND power signals. We can also see pads for Tx/Rx/CTS, a boot button, a crystal oscillator, and a USB-C port to connect to the host computer. What I don’t see […]
Timesys Embedded Board Farm enables remote access to hardware for software development & QA
When you design a new board with an international team working in multiple locations, there may only be a couple of boards available for testing, and that’s mean some members of the team may not have access to the hardware. The same problem can be true for test farms with a larger number of boards. So it would be good to have a solution to remotely access and control the hardware to speed up development. A few years ago we wrote about MuxPi board using NanoPi NEO SBC to enable remote testing of development boards, but now Timesys has come up with a more advanced solution with the Embedded Board Farm (EBF) capable of sharing multiple boards across teams spread around the world. The solution is comprised of three main components besides the target boards: The Master Server integrated with LAVA test automation framework – It handles docker images, firmware/file […]
Arm introduces Open-CMSIS-Pack and Keil Studio Cloud for MCU software development
Arm has just announced two new initiatives that aim to boost the productivity embedded, IoT, ML, and MCU software developers: the Open-CMSIS-Pack project and Keil Studio Cloud. The Open-CMSIS-Pack Project The Cortex Microcontroller Software Interface Standard (CMSIS) packs have been around for years providing a vendor-independent hardware abstraction layer for microcontrollers, mostly Cortex-M based, but others too, and currently support close to 9000 different microcontrollers. I always assumed CMSIS was open-source as the source code is available in Github under an Apache 2.0 license. But apparently, not all components are, and Arm has now announced the Open-CMSIS-Pack project that will move part of CMSIS into the open project in collaboration with the Linaro IoT and Embedded Group. Linaro, Arm, and other partners like STMicro and NXP will initially focus their work on command-line tools and CMake workflows, with the ultimate goal of making the CMSIS-Pack technology into a true open […]
JTAG Hat for Raspberry Pi eases debugging with OpenOCD
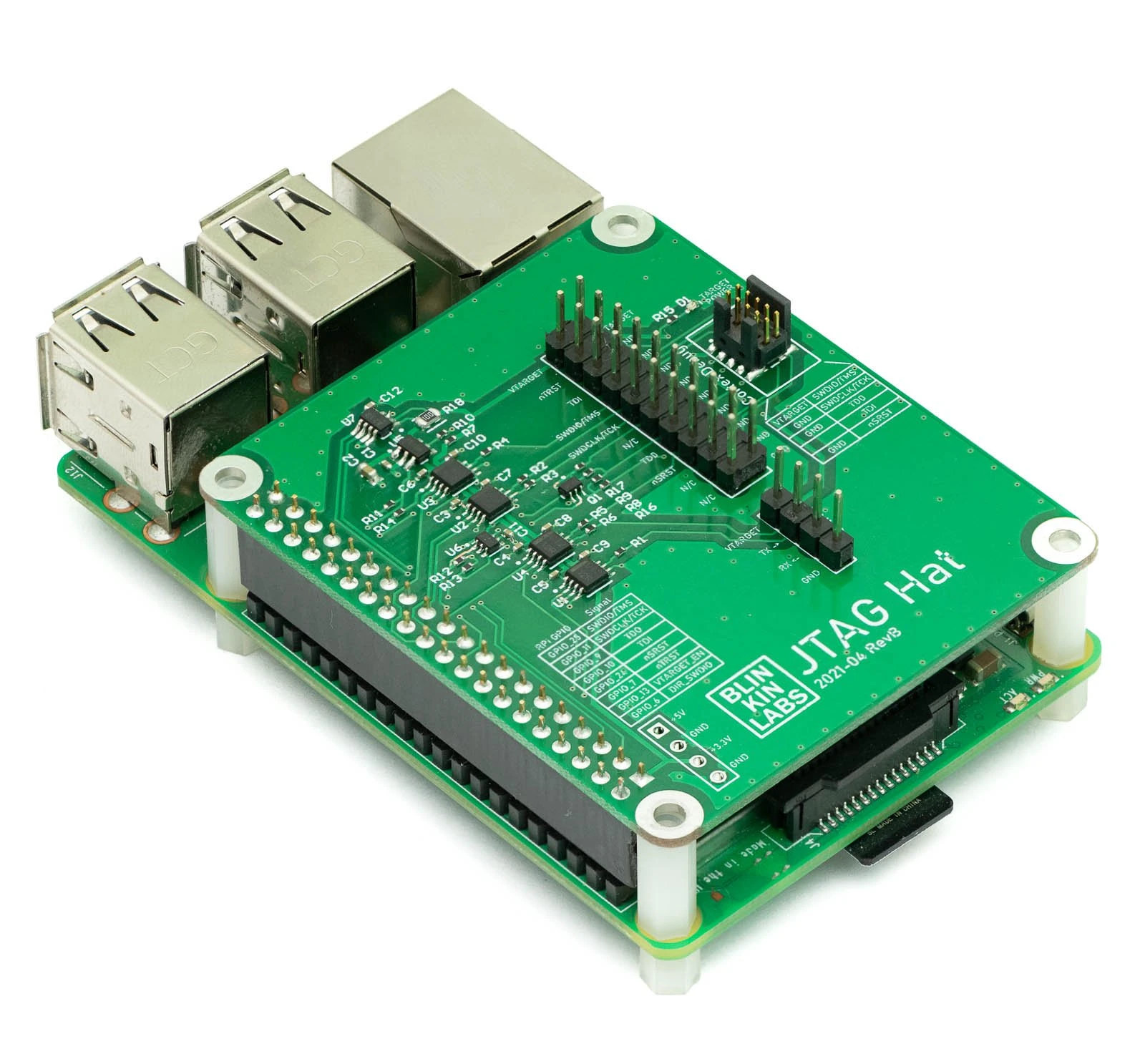
Low-level debugging can be performed with a JTAG debugger and OpenOCD open-source software, but since not everybody may have a JTAG debugger at home, some have reverted to using the Raspberry Pi as a JTAG debugger, and you’ll find instructions for cabling and installing the software on the Internet. Matt Mets of BlinkinLabs have been using the Raspberry Pi SBC and OpenOCD to debug Arm-based microcontroller boards for a while, but found it to be a pain to find jumper wires and look up the pin-outs manually each time. So he designed a JTAG Hat with properly labeled 20-pin .1″ and 1.27mm Cortex debug connectors to speed up the process. The expansion board also adds level-shifting buffers to interface with targets running at 1.8-5V, transistor-based power reset pins, a power switch for optionally supplying 3.3V to the target, a voltage/current sensor for measuring the target power consumption, and a buffered […]
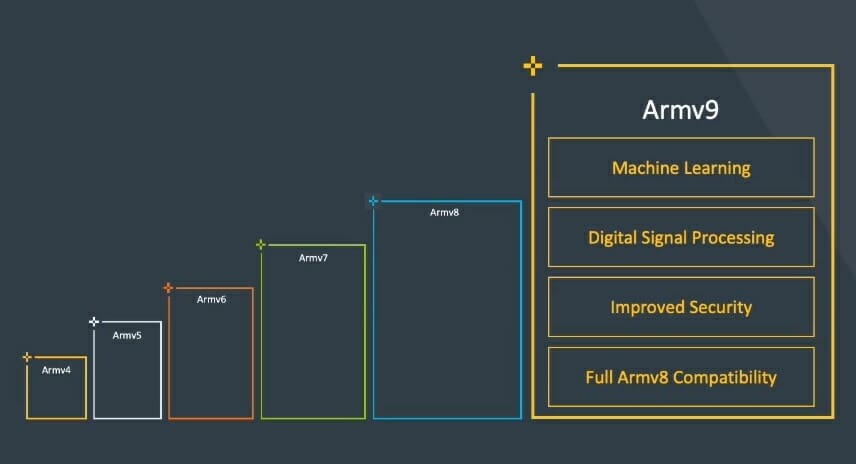
Armv9 architecture to focus on AI, security, and “specialized compute”
Armv8 was announced in October 2011 as the first 64-bit architecture from Arm. while keeping compatibility with 32-bit Armv7 code. Since then we’ve seen plenty of Armv8 cores from the energy-efficient Cortex-A35 to the powerful Cortex-X1 core, as long as some custom cores from Arm partners. But Arm has now announced the first new architecture in nearly ten years with Armv9 which builds upon Armv8 but adds blocks for artificial intelligence, security, and “specialized compute” which are basically hardware accelerators or instructions optimized for specific tasks. Armv9 still supports Aarch32 and Aarch64 instructions, NEON, Crypto Extensions, Trustzone, etc…, and is more an evolution of Armv8 rather than a completely new architecture. Some of the new features brought about by Armv9-A include: Scalable Vector Extension v2 (SVE2) is a superset of the Armv8-A SVE found in some Arm supercomputer core with the addition of fixed-point arithmetic support, vector length in multiples […]