Bouffalo Lab BL602, and its big brother BL604 with extra GPIOs, are RISC-V microcontrollers with WiFi and Bluetooth LE that offer an alternative to Espressif Systems ESP32 Xtensa based WiSoC, although Espressif has also designed its own RISC-V solution: ESP32-C3.
Soon after the “announcement” in October 2020, we found out the SDK and a relatively cheap BL602 board, but the SDK has many closed-source binaries. Soon after Sipeed and Pine64 expressed their interest in developing an open-source toolchain and even an open-source WiFi (and BLE) stack. Time has passed and even got a Pinecone board in January, but did not do anything with it, especially seeing the status of the software.
The same cannot be said for Lup Yuen Lee (aka MrTechBlog) who spent a lot of time doing interesting with Pine64 BL602 module and board including playing and thoroughly documenting his work with Tensorflow Lite, connecting the board to a LoRa module, and more (scroll down that link to the Publications section for more posts).
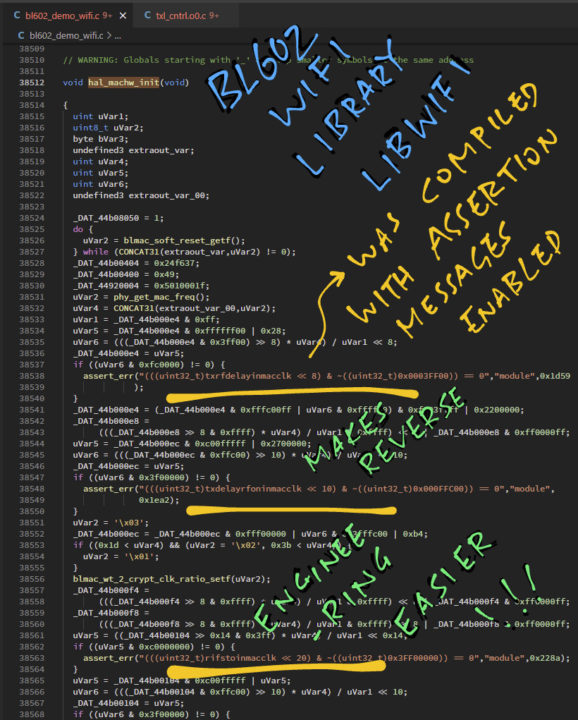
More recently he decided to work on the Nutcracker challenge to create an open-source WiFi and Bluetooth stack, and wrote a long post going through the reverse engineering process for the WiFI code in BL602 SDK.
This includes going through all functions of the code to understand basics like connecting to a WiFi router and sending some HTTP packets using the demo firmware, Since some of the code is binary only it was decompiled into C language for further analysis. That part is not quite easy since variable and function names are not exactly meaningful, but he went through it to check out which part may be leveraged for reverse engineering as illustrated below.
Then the whole process is a dance between the SDK source code and the decompiled C source to try to understand what’s going on… and eventually, it appears the WiFi code comes from CEVA RivieraWaves firmware/software used in many WiFi solutions. Lup Yuen Lee even noticed the code for BL602 looks very similar to the one for the RK3399 WiFi supplicant code.
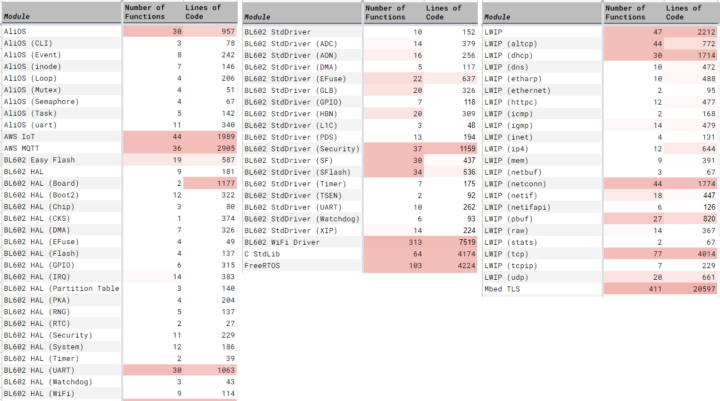
Most of the non-WiFi functions are open-sourced and the analysis also found out the SDK uses source code from various projects including AliOS embedded framework for multitasking and device drivers, AWS Cloud for IoT and MQTT (Message Queue) services, EasyFlash embedded database, FreeRTOS running underneath AliOS, Lightweight IP (LWIP), and Mbed TLS.
But all this work is just a starting point for further work. You may learn a lot about reverse engineering a WiFi stack by reading the full post.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress