Security is becoming more and more important with critical data exposes to the Internet. Traditionally some PCs, laptops, motherboards, or single board computers would be equipped with a TPM (Trusted Platform Module) designed to secure hardware through integrated cryptographic keys. More recently, we’ve started to read more and more about secure elements providing hardware-based security for lower-end platforms.
Those are external chips, but companies have also started to providing hardware-security within the processor with solutions such as Arm Trustzone or Intel SGX (Software Guard Extensions). But more recently, Google and Microsoft have made announcements about hardware-security IP with respectively OpenTitan open source project and Microsoft Pluton security chip both meant to be embedded into processors.
OpenTitan

It was announced last year, but Google recently published an update detailing some of the progress made by the project:
- More than doubled the number of commits at launch (November 2019): from 2,500 to over 6,100 (across OpenTitan and the Ibex RISC-V core sub-project).
- Grew to over 141K lines of code (LOC) of System Verilog digital design and verification.
- Added 13 new IP blocks to grow to a total of 29 distinct hardware units.
- Implemented 14 Device Interface Functions (DIFs) for a total 15 KLOC of C11 source code and 8 KLOC of test software.
- Increased our design verification suite to over 66,000 lines of test code for all IP blocks.
- Expanded documentation to over 35,000 lines of Markdown.
- Accepted contributions from 52 new unique contributors, bringing our total to 100.
- Increased community presence as shown by an aggregate of over 1,200 Github stars between OpenTitan and Ibex.
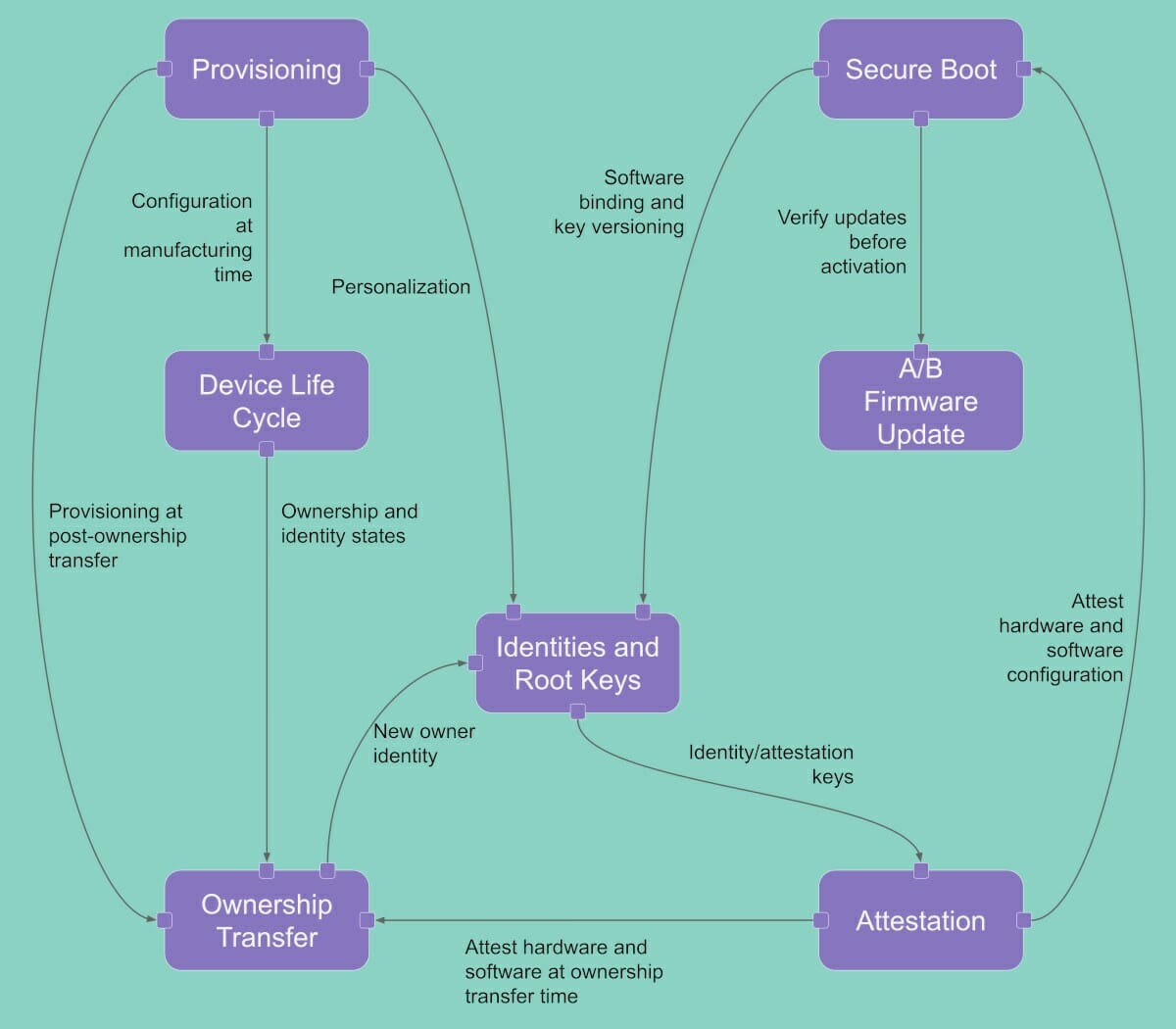
The company also said OpenTitan is the first project to publish an open Security Model for a silicon root of trust and covers provisioning, secure boot, device identity, and attestation, and our ownership transfer mechanism, among other topics.
Since OpenTitan is open-source any chip designers could integrate it into their processor(s), but there’s no ETA for when this may happen, as the project still seems to be a work in progress. You’ll find all details on the main website.
Microsoft Pluton
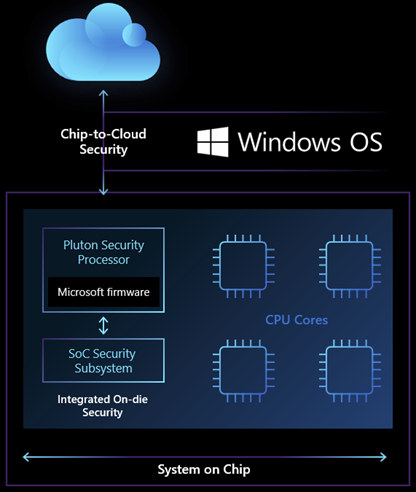
On the other side, we have Microsoft Pluton that was first introduced in 2018 inside MediaTek M3620 Cortex-A7/Cortex-M4 processor with support for Microsoft Azure Sphere OS. The main news for 2020 is that Microsoft announced Pluton will now aim to replace the external TPM chip with an embedded hardware-security solution built into Intel, AMD, and Qualcomm processors found in Windows PCs and laptops.
Based on the diagram above, it appears Pluton may address a different layer of the security stack compared to OpenTitan, as it acts between the SoC security subsystem and the cloud, and is designed to provide more secure cloud connectivity. External chips may be prone to physical attacks, with a bad actor capable of capturing data between the processor and the TPM using a logic analyzer, and then work on the capture data, but this would be much more challenging or even impossible to do the same with Pluton security processor as it’s part of the main SoC.
Other advantages touted by Microsoft include support for the Open Compute Project’s Project Cerberus providing a secure identity for the CPU, and the ability to keeping the system firmware up to date more easily as Pluton firmware updates will be delivered through the Windows Update process.
Just like with OpenTitan, there were no specific processor announced with Pluton, nor specific availability announcement, but I’d assume some of the processors from Intel, AMD, and Qualcomm announced or launched in 2021 will come with Pluton security chip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress