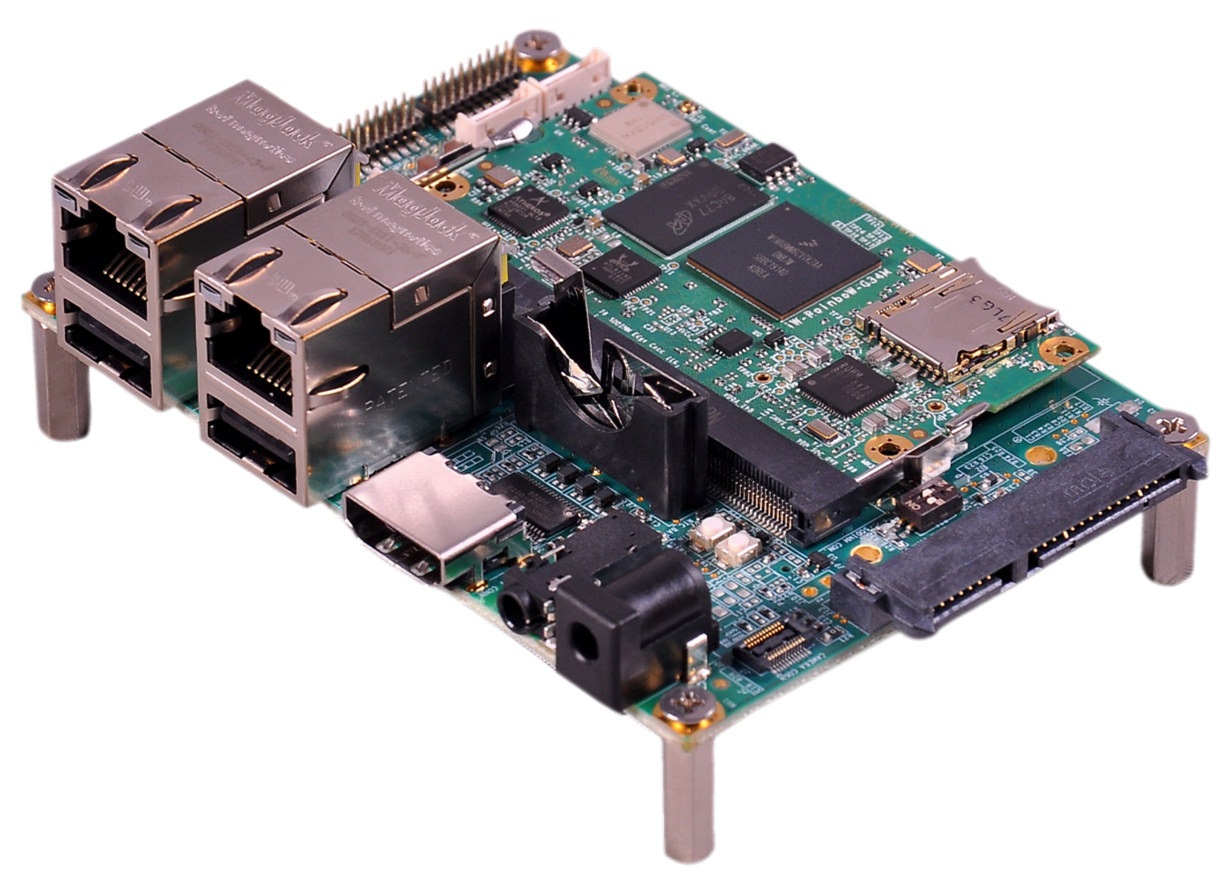
iWave Systems i.MX8M Mini Board is a development platform based on an update versions of the company’s iW-RainboW-G34M-SM i.MX 8M Mini system-on-module and designed specifically for low-cost facial recognition systems thanks to NXP eIQ ML software, and MIPI display and camera.
iWave Systems i.MX8M Mini (aka iW-RainboW-G34D) specifications:
- SoM
- SoC – NXP i.MX8M Mini Q/QL/D/DL/S/SL with up to 4x Cortex-A53 cores, 1x Cortex-M4F real-time core, Vivante 3D and 2D GPUs
- System Memory – 1GB LPDDR4 (Expandable up to 4GB)
- Storage – 8GB eMMC Flash (Expandable), optional 2MB QSPI Flash optional Micro SD slot
- Wireless – Dual-band 802.11a/b/g/n/ac WiFi 5 and Bluetooth 5.0.
- PMIC – BD71847AMWV
- i.MX8M SODIMM Carrier Board
- Storage – MicroSD slot
- Display I/F – MIPI DSI display connector
- Camera I/F – MIPI CSI camera connector
- Audio – Audio codec, 3.5mm Line In/Out jack
- Networking – Up to 2x Gigabit Ethernet ports (One is Optional)
- USB – 2x USB 2.0 Host ports, 1x USB 2.0 device port
- Debugging – Serial console on Micro USB Port, JTAG header
- Expansion – 1x Data UART, GPIO Header, eCSPI (Enhanced Configurable Serial Peripheral Interface) header
- Misc – RTC Coin cell, boot mode switch; ON/OFF, reset Switch
- Dimensions – 100 x 72 mm (Pico-ITX form factor)
- Display – 5.5” HD AMOLED MIPI DSI display
- Camera – OV5640 camera module up to 1080p30
- Power Supply – 5V @ 1A DC Input
- Temperature Range – 0°C to +60°C
- Compliance – REACH & RoHS
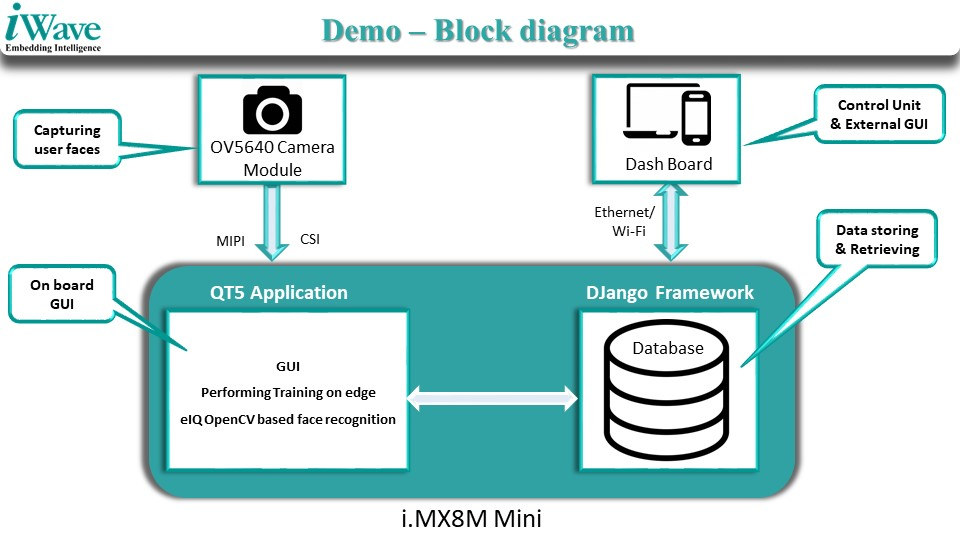
A facial recognition demo is included with the development kit. It relies on a Qt5 GUI, eIQ OpenCV ML software to compare the faces captured by the camera against registered face images in a database using the Django framework. The board also sends real-time data to the cloud via Ethernet and WiFi, so that authorized access and unauthorized detection can be visualized on a web dashboard.
One of the main use cases of the development kit is access control with face recognition solutions being much safer than fingerprint-based access control solutions in the time of COVID-19, as it enables zero-contact access application by using individuals’ faces to authorize access to a commercial/industrial space, home/office, transportation, banking, and government sites.
There’s no information about availability nor pricing. You may read a bit more about the solution on the press release, and/or contact the company via the product page.
Via LinuxGizmos

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





