Found in most microcontrollers and processors, JTAG is an industry standard for verifying designs and testing printed circuit boards after manufacture, and that is also often used for low-level debugging or reverse-engineering.
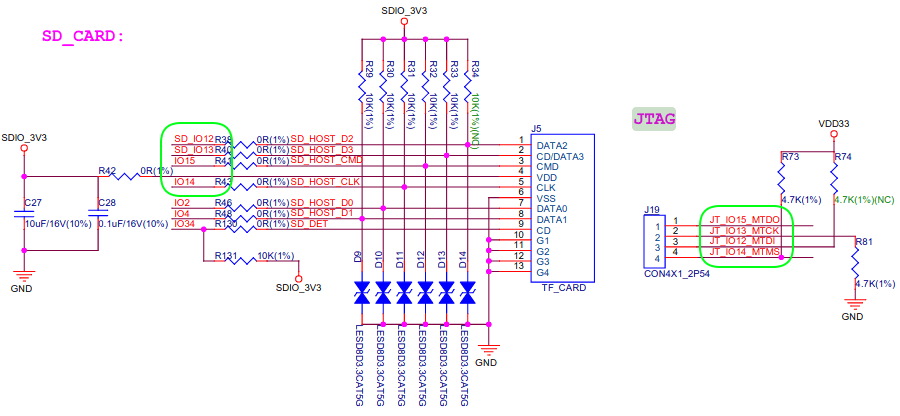
Espressif ESP32 also has a JTAG interface, but interestingly it’s shared with the SD card interface, and in ESP32 LyRaT audio development board where both MicroSD card slot and JTAG header are present selection is made by jumpers.
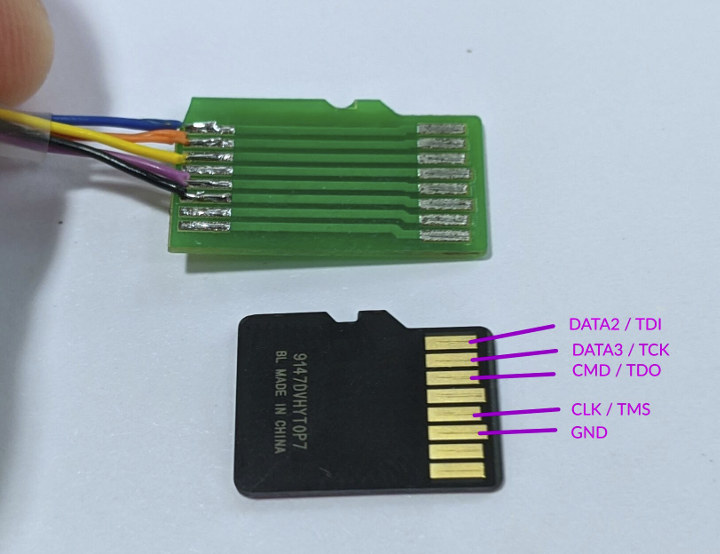
The extract from ESP32 LyRaT schematics above shows IO’s 12, 13, 14 and 15 can present on the SD card and 4-pin JTAG header. Some boards may not come with a JTAG header but may feature a MicroSD card slot, but you don’t have to solder wires to the board to access JTAG, and instead, you could simply use a custom MicroSD card adapter to insert into the MicroSD card socket of the board and access JTAG as explained by cibomahto on Twitter.
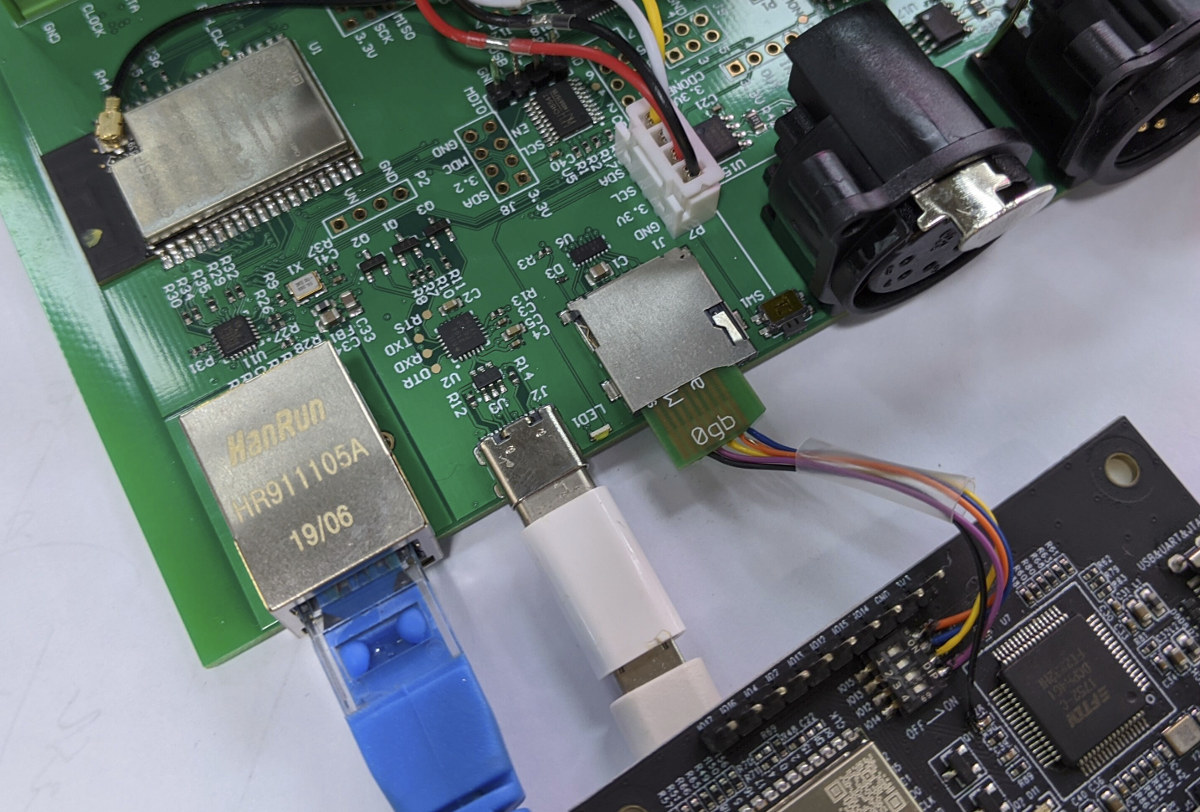
Nice little hardware trick! The photo below shows what it looks like when an ESP32 board is connected to a “JTAG debugger” (actually ESP32-Ethernet-Kit development board with FTDI chip). If your board comes with a full-sized SD card socket using a standard MicroSD to SD adapter should work too.
Reading comments on Twitter also informs use ESP32 is not the first platform with this trick, as (some?) Allwinner processors also route JTAG signals via the SD card interface.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress