Security is hard. Just as Espressif Systems announced PSA Level 2 for the ESP32-C6 microcontroller, Spain-based cybersecurity company Tarlogic published their findings about a hidden Bluetooth functionality that can be used as a backdoor in the previous generation ESP32, and gave a presentation in Spanish at Rootedcon 2025.
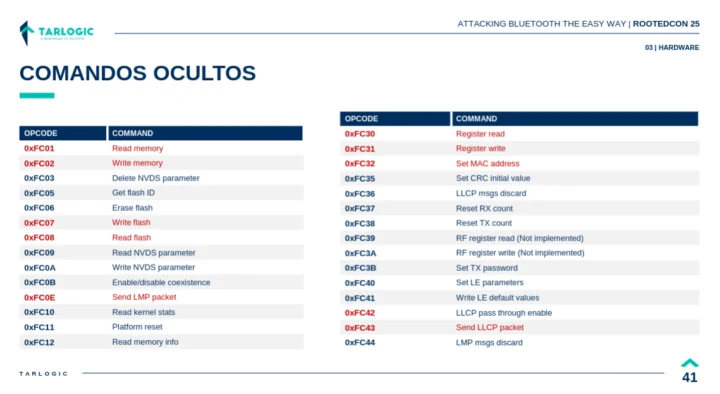
Specifically, they found hidden proprietary Bluetooth HCI (Host Controller Interface) commands used to read & write controller memory, and typically used for debugging. However, they could also facilitate supply chain attacks, the concealment of backdoors in the chipset, or the execution of more sophisticated attacks. Tarlogic initially called it a “backdoor”, but some disputed the claim (more on that later), and the company eventually issued an update downgrading it to a “hidden” feature:
We would like to clarify that it is more appropriate to refer to the presence of proprietary HCI commands—which allow operations such as reading and modifying memory in the ESP32 controller—as a “hidden feature” rather than a “backdoor.”
The use of these commands could facilitate supply chain attacks, the concealment of backdoors in the chipset, or the execution of more sophisticated attacks. Over the coming weeks, we will publish further technical details on this matter.
According to the researchers, bad actors could potentially infect not only the ESP32 chips themselves, but devices that connect to them through Bluetooth such as smartphones or even medical devices:
Exploitation of this hidden functionality would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
That looks scary, especially since over one billion ESP32 devices are in the wild. Let’s have a closer look.
Tools used for discovery included a LibUSB-based Bluetooth device driver and Scapy sockets developed by Antonio Vazquez from Tarlogic, and ROM ELF documentation from Espressif. These allowed them to enable raw access to Bluetooth traffic, and after reverse-engineering work, they eventually discovered 29 undocumented HCI commands in the ESP32 Bluetooth firmware. Those commands can be used to read and write RAM and Flash, MAC address spoofing, and LMP/LLCP packet injection.
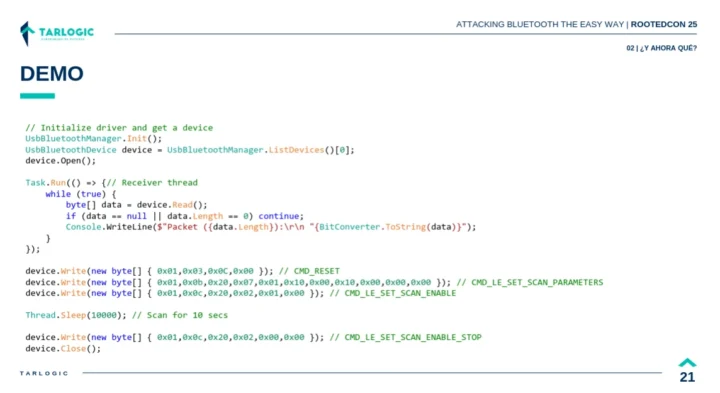
The ESP32 Bluetooth security vulnerability has its own CVE (CVE-2025-27840) with a medium severity score of 6.8 points. Targlogic says they will provide more technical details later, and still need specific hardware that will allow them to implement advanced attacks.
A post by Xeno Kovah from Dark Mentor LLC provides more insights. First, it rejects the initial “backdoor” assessment:
What the researchers highlight (vendor-specific HCI commands to read & write controller memory) is a common design pattern found in other Bluetooth chips from other vendors as well, such as Broadcom, Cypress, and Texas Instruments. Vendor-specific commands in Bluetooth effectively constitute a “private API”, and a company’s choice to not publicly document their private API does not constitute a “backdoor”.
Backdoor claims aside, they also tried to assess whether this feature constitutes a security vulnerability. The short answer is that it depends. The longer answer explains that it’s not a vulnerability for customers who do not make a distinction between the privileges of the Host and the Controller. However, it would be for a customer who does not want a compromised userspace on the Host to automatically guarantee a compromised Bluetooth Controller firmware. In any case, they consider use of VSCs granting the capability to read and write memory, flash, or registers is a bad security design, but it impacts all Bluetooth vendors.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress