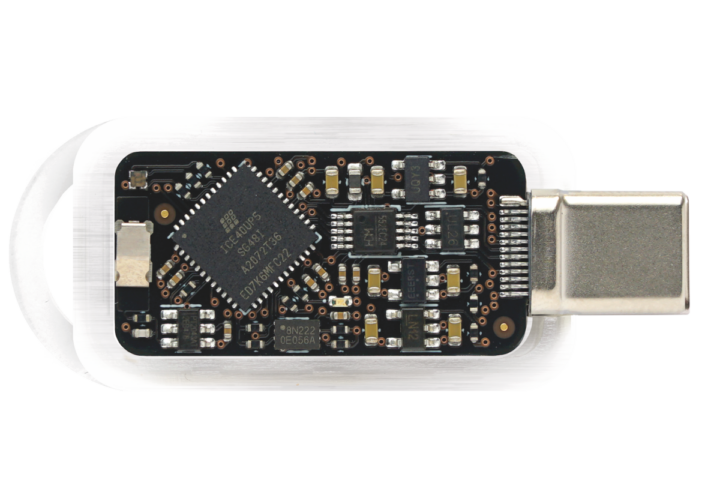
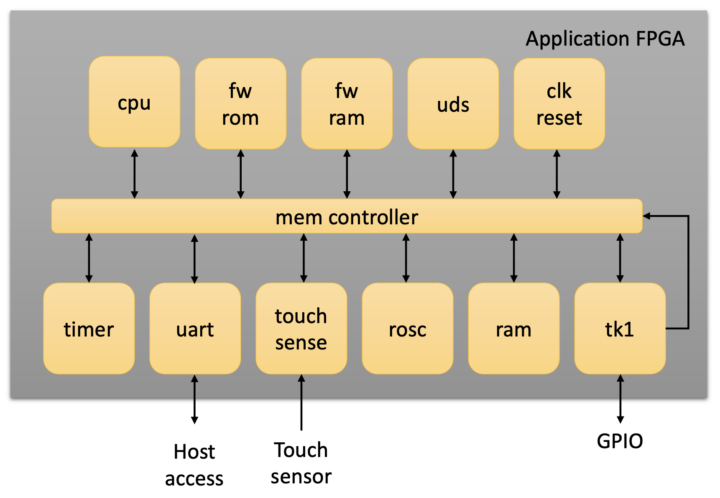
Tillitis’ TKey is a small, simple security key in a USB-C form factor, and described as a “new type of flexible USB security token” that is inspired by DICE (Device Identifier Composition Engine) and measured boot powered by a simple 32-bit RISC-V core, the PicoRV32, in a Lattice iCE40 UP5K FPGA.
While we have covered hardware security modules in the past, this is the first security key we have seen that is based on an FPGA running a RISC-V core. The security token lacks persistent, onboard storage, unlike alternatives such as Yubikey Neo. Apps need to be loaded onto the key every time it is connected to a host device. It uses measured boot to generate a unique identifier for each application and is more secure than the alternatives since private keys are not stored on the device. Also, the hardware and software for the TKey are completely open-source for trustability.
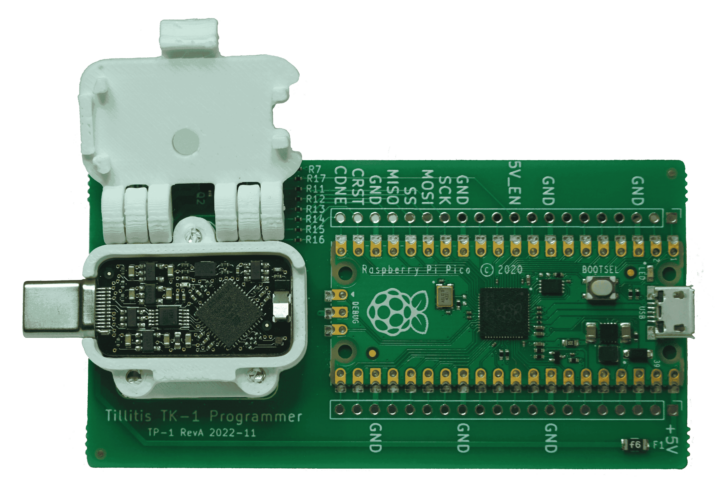
Tillitis is a Swedish security firm that was spun out of the Mullvad VPN company in 2022. Tillitis is a play on the Swedish word tillit, meaning trust or confidence. It is an appropriate name for a brand that specializes in hardware trust products. There are two versions of the TKey security token: locked and unlocked. The locked TKey is aimed at general users and cannot be reprogrammed. The TKey Unlocked, on the other hand, is targeted at general users and enables full configuration of the TKey with the aid of another device, the Tillitis TK-1 Programmer based on a Raspberry Pi Pico.
TKey specifications:
- Processor
- 32-bit RISC-V PicoRV32 core @ 18 MHz
- FPGA: Lattice iCE40 UP5K
- 128 KiB RAM for TKey device application
- 2 KiB RAM for firmware
- 6 KiB ROM
- Execution monitor
- RAM protection
- Connector – USB-C
- Hardware Privilege Modes – Firmware mode and application mode
- Misc: Touch sensor, power indicator, status indicator
- Input voltage – 5V
- Max current consumption – 100mA
- Operating temperature – 0°C – 40°C
You can find several pre-built TKey applications on the company website available for download. The TKey Developer Handbook covers developing your own device and client applications for the TKey. As noted earlier, the Tillitis TKey is completely open-source and all software, firmware, Verilog source code, schematics, and PCB design files can be found in the GitHub repository.
The end-user and the advanced user versions of the TKey RISC-V security key can be bought from the Tillitis shop for 880 Swedish krona (about $90) while the programmer is priced at 500 Swedish krona (around $50).
Via Hackster.io

Tomisin is a writer specializing in hardware product reviews, comparisons, and explainers. He is very passionate about small form factor and single-board computers.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress