The Linux Foundation has just announced the full schedule for the Embedded Open Source Summit, which will take place on June 27-30, 2023 in Prague, Czech Republic, as well as virtually starting on June 26.
Over 175 sessions, birds of a feather (BoF) tracks, and workshops related to embedded and open-source innovation will be presented at the event itself comprised of six micro conferences: Automotive Linux Summit Europe, Embedded IoT Summit, Embedded Linux Conference, LF Energy Embedded Summit, Safety-Critical Software Summit, and Zephyr Project Developer Summit. Even though I’m not going to attend personally, I’ve gone through the schedule to create my own little virtual schedule with some sessions relevant that should be interesting to me and hopefully to CNX Software readers.
Monday, June 26 (Virtual sessions)
The first day of the event will have a Yocto Dev training in the morning, and a bunch of virtual sessions that are shown to start at 12:00, but the time is not relevant, as those appear to be on-demand sessions that you can watch when convenient. So I just selected three:
- Outsmarting IoT Defense: The Hacker’s Perspective by Natali Tshuva, Sternum IoT
Endless patching is a race that cannot be won. To build sustainable, secure IoT solutions we must change that ineffective paradigm. To appreciate what we can do differently, we should start by considering both the defender’s and attacker’s perspectives. This session will provide a unique view of that attacker’s perspective, from former exploit/attack experts within the IDF Unit 8200. We will review the impossible task of identifying and mitigating all vulnerabilities – and will demonstrate the inadequacies of current IoT security practices focused on continuous patching, static analysis, encryption, and risk controls. We will also explain how attackers can easily evade such barriers. By contrast, the session will explore methods for achieving embedded, on-device runtime exploits protection to immunize devices from all underlying vulnerabilities, and provide zero-day protection as well. These methods, commonplace in IT endpoint detection and response, are just now finding their way into heretofore unprotected and unmanaged IoT edge devices.
- Secure Virtualization for MCUs using Wasm by Dan Mihai Dumitriu, Midokura (Sony Group)
IoT devices have traditionally been developed using a monolithic approach, with firmware written by a single vendor and infrequent updates. With the increasing connectivity of IoT devices to the cloud, it is now possible for these devices to be customized and updated frequently. However, the current software development paradigm for IoT devices has not kept pace. We are preparing to open source Wedge, a virtualization platform for IoT devices based on WebAssembly.
Wedge works together with IoT platforms, such as ThingsBoard, AWS IoT, etc, to manage the lifecycle of applications on the IoT device. Wedge also provides various primitives for apps to use, and SDKs in multiple languages. Wedge uses AoT (ahead of time) compilation, done securely in the cloud, to optimize execution. On top of Wedge, we have developed a programming paradigm called Vision Sensing Pipeline for sensor data processing at the edge. Using information gathered from the IoT platform, the cloud-based Sensing Pipeline Service automatically specializes the modules for the target devices. Developers never need to care about the architecture or exact capabilities of the devices. On top of the REST API, we have also added a visual programming interface, inspired by Node-RED. A brief demo will be shown.
- Zephyr Footprint – Where Are We and Where Are We Going by Ederson de Souza, Intel Corporation
Zephyr memory usage is of interest for those who want to use it in constrained hardware, limited to a few hundred kilobytes. In this talk, the audience will be taken into what Zephyr currently does to keep its footprint down – such as compiler and linker options, as well as explore different approaches that can be used in the future; for example, a look into Zephyr current APIs (Application Programming Interfaces), based on function pointers, and how a “static dispatching” mechanism could help the linker to shave some dead code and reduce Zephyr’s memory usage further.
All other virtual sessions are also part of the Zephyr Project Developer Summit which represents a significant part of all sessions from the Embedded Open Source Summit 2023 up until June 28.
Tuesday, June 27
- 09:00 – 09:40 – Secure Boot: What Is It, and Do I Need It? by Eystein Stenberg, Northern.tech
Secure boot is a term heavily used within connected devices and IoT in particular, but it can also apply to other computing devices such as laptops and smartphones. A lot of confusion exists around what “secure boot” means because some hardware vendors have named their own implementation the same, or some variation of it, even though the general term is commonly used for a more broad implementation. This makes it difficult to understand what secure boot is, and which elements can be interesting in a given context. This talk aims to clear up the confusion around secure boot, in particular covering implementations in connected devices and IoT, where secure boot is very relevant. In this talk we will:
- Decompose secure boot: the different use cases and technologies involved
- Demonstrate real-world threats and use cases where secure boot can prevent
- Cover threats where secure boot cannot help
- Provide market data on the status of implementation of secure boot in IoT
- List key components that you need to worry about for supporting secure boot
- 09:50 – 10:30 – Porting an AI-Powered Wearable Health Monitor to Zephyr on Open Hardware by Szymon Duchniewicz, Avanade & Jakub Duchniewicz, Tietoevry
To RTOS or not to RTOS? Szymon and Jakub will introduce obstacles they faced and decisions behind moving a closed-source single-threaded wearable health monitor to an RTOS, open-hardware-based system with an AI model deployed on a Field-Programmable Gate Array (FPGA). They will share tips on how to get started with Zephyr development, when and why to build a system using an RTOS. They will also share best practices and experiences on deploying a Machine Learning model to an embedded FPGA and interacting with it from Zephyr OS. The project dissected in this talk uses QuickLogic’s and Antmicro’s QuickFeather board, powered by Open Hardware EOS S3 System on Chip. The Machine Learning Model is deployed using TensorFlow Lite and then integrated using an open-source FPGA toolchain. The device collects data from an SPO2 sensor that is parsed by Zephyr at runtime and finally passed to the model deployed on the FPGA for inference. The results are then returned to the Zephyr RTOS and displayed on a small OLED screen. The model is trained using open-source data pertaining to blood pressure estimation based on SPO2 levels and is tailored specifically for deployment in embedded scenarios.
- 11:00 – 11:40 – Reliable And Robust Applications Using Container-like Abstractions On Non-MMU SoCs by Gustavo Henrique Nihei, Espressif Systems
Kernel and Userspace separation is a technique commonly employed in general-purpose operating systems for improving the security and reliability of a system via the isolation of unprivileged applications from accessing privileged Kernel resources. With the ever-improving feature-set of microcontrollers, small real-time operating systems caught up and are now able to grant the required security for the widespread connected devices. However, usage of such features is usually restricted to single-application scenarios. This presentation proposes the exploration of security features of microcontrollers to extend this privilege separation to a container-like architecture where the user space may be composed of completely isolated mixed-criticality applications.
The Apache NuttX RTOS has been chosen as the test bed for this experiment, which provides a Protected Mode build where the Kernel resources may be accessed from the unprivileged Userspace exclusively via system calls. Isolation between distinct userspace applications is achieved by means of a combined work of the memory protection unit and a TEE (Trusted Execution Environment) controller, which manages the access permission to critical resources of the system.
- 11:50 – 12:30 – Brewce: Brewing Beer with Zephyr, Android and Thingsboard by Christian Hirsch
Beer is one of the oldest known cultural beverages. Its main ingredients are water, (barley) malt, hop, and yeast. The process of brewing beer is well-known and in order to dissolve the starch from the malt into the water, also called mashing, the malt and water mixture is heated up to specific temperatures that need to be held for a certain amount of time. This gives the enzymes in the malt the ability to break up the starch to dissolve it. Hobby brewers normally use home brew kits and commercially available equipment to brew their own beer. In this talk, Christian Hirsch presents brewce: a setup of home-brewed electronics for home-brewing beer. brewce consists of four devices: a modified induction cooker, a temperature sensor, a pump control, and a smartphone. The induction cooker was reverse-engineered and equipped with some electronics which runs the Zephyr RTOS and which let one control it via Bluetooth Low Energy (BLE). The same is true for the temperature sensor and the pump control. An Android app on a smartphone connects to all three devices via BLE and controls the induction cooker and a pump based on the temperature sensor’s readings to run the mashing procedure. Christian presents the setup, the electronics and firmware, the obstacles, and the results.
- 14:00 – 14:40 – New USB Device Class API Introduction by Johann Fischer, Nordic Semiconductor ASA
As part of the experimental USB support, a new device stack has been added to the Zephyr RTOS since version 3.3.0. Existing implementations of the USB classes (or functions) will be ported to the new USB device support (porting should be completed by presentation time). The USB device stack itself does not provide any useful functionality. The functionality can be provided by a class implementation like CDC ACM. There are USB-IF class specifications, like CDC ACM, or third-party specifications, like the Bluetooth HCI transport layer. New USB device support has a common API to interface with class implementations. A vendor-specific class or function must also use this API. The API will be mandatory for all new implementations. The stack also has management functions, such as adding or removing a class instance to or from a configuration at runtime. Johann will give an introduction to the new USB device class API in USB support, show how to implement a simple function that supports multiple instances, and briefly describe the API. The author will also cover relevant differences and features in the new USB device support.
- 14:25 – 14:35 – Lightning Talk: SWUpdate Over CAN Bus – Can It? by Stefano Babic, DENX
Embedded Linux will be more used in automotive, and even ECUs based on simpler microcontrollers are starting to be exchanged with more sophisticated processors with Linux as OS. Software is becoming complex and the size of the firmware increases. On the other side, even if other network technologies (LTE, Wireless, etc.) are making the first steps into vehicles, the primary bus for communication is CAN (Controller Area Network), with limitations regarding transfer size and low bandwidth. This talk is the description of the journey done by the author about how to implement an update mechanism using SWUpdate to upgrade an ECU over the CAN bus, showing which limitations we must face and what can be done in the future.
- 14:50 – 15:30 – Fearless Embedded Rust by Martin Mosler, Zuehlke Engineering AG
Have you heard how steep the learning curve for new Rust developers is? Even worse, you heard horror stories about fighting the borrow checker and that you have to write unsafe code for embedded devices. Then this talk might be for you. Martin will demonstrate to you, how easy it can be to develop a small but complete application in Rust during this talk. Let’s get started and develop a temperature logger running on an embedded device sending its data to the cloud.
- 15:50 – 16:30 – OTA DFU Without Compromise by Brandon Satrom, Blues Wireless
Over The Air Device Firmware Update is one of the most-desired features for any IoT device management solution. In a world where all solutions are cloud-connected, DFU is a table-stakes feature. But modern DFU approaches are brittle, and developers are forced to choose between either an “OS DFU” approach, in which a vendor solves the DFU problem end-to-end within the kernel, while specifying a very narrow choice of hardware, language, and IDE; or “Co-operative DFU,” in which a vendor provides a cloud service to securely host firmware images and transport onto the device, but in which the “last mile” of the update process is the developer’s responsibility. Both methods can be made reliable, but are risky and can be inadvertently rendered nonfunctional by an errant ‘infinite loop,’ memory or flash overwrite, or bad interrupt handler. What if there was a third way? An approach for performing firmware updates “from the outside” without MCU involvement? An approach that can update firmware regardless of RTOS or language, and can even be used to switch between them? In this session, Brandon Satrom will introduce such an approach, and demonstrate how this capability allows developers more choices of host, language, and RTOS, without sacrificing the stability of end-to-end DFU.
- 16:40 – 17:20 – Open Source to the Core: The CORE-V MCU by Frédéric Desbiens, Eclipse Foundation
Open source has transformed the way we build and consume software. And yet, the computers we run our software on are the realm of proprietary technology. The recent emergence of the RISC-V instruction set was a first step to challenging the status quo. However, while the instruction set is open source, the chips that leverage it have been proprietary. That is, up to now. The CORE-V Microcontroller from the OpenHW Group changes that. Based on an open-source 32-bit four-stage RISC-V core, the MCU offers a rich set of peripherals, an embedded FPGA, and much more. In this presentation, you will learn everything there is to know about the CORE-V MCU and OpenHW Group. You will also discover how the OpenHW Group and the Eclipse Foundation are building a comprehensive RISC-V ecosystem together. Finally, you will see how to leverage RTOSes and the wider ecosystem of Eclipse IoT components on the CORE-V MCU.
Wednesday, June 28
- 11:10 – 11:50 – Finding the Best Block Filesystem for Your Embedded Linux System by Michael Opdenacker, Bootlin
It can be difficult to find the most appropriate filesystem for your embedded system’s eMMC or SD card storage. You can benchmark your system with each of them, but it can be time-consuming. In this talk, we will compare all the actively maintained block filesystems supported in the Linux kernel: ext2, ext4, xfs, btrfs, f2fs, squashfs, and erofs. Each of them will be properly introduced, with its basic design principles and main features. We will then compare each filesystem in terms of kernel module size and load time, filesystem mount time (important for boot time), filesystem size, as well as read and write performance on a few simple scenarios. We will also look for the best compression algorithms for filesystems with compression options. Performance comparisons will be run both on a 32-bit ARM board and on a 64-bit ARM one, both using a fast SD card as a storage device. Filesystem performance can really depend on the benchmark, on your storage, and on your CPU, so no universal results should be expected. However, you will learn what the best solution is in specific hardware configurations and test cases. No AI will be used to prepare, write this presentation and answer your questions. Only a human brain with 20 years of experience with Embedded Linux.
- 12:00 – 12:40 – Status of Embedded Linux by Tim Bird, Sony Electronics
In this talk, Tim will give an overview of issues in Linux in the embedded space that have come about in the past year. Tim will discuss recent developments in the Linux kernel that are of interest to embedded developers, covering such topics as filesystems, networking, tracing, and real-time. He will also discuss security, testing, and other technical topics. Tim will also talk about community and industry news related to Linux in embedded systems, including the status of major processor vendors, projects at the Linux Foundation, and other relevant community projects. It is hoped that through this talk, developers can learn about changes to the kernel or initiatives in the industry that might be of benefit to their own embedded Linux development. This year, Tim may focus a bit more on the use of Linux in space applications! Come to the session and find out what’s new with embedded Linux!
- 14:00 – 14:40 – Stateless V4L2 Video Encoding by Andrzej Pietrasiewicz, Collabora
Andrzej will start his talk by explaining the difference between stateful and stateless video codecs. He will outline the implications of each approach and highlight the benefits of the stateless approach. Andrzej will also share his experience with a particular VP8 stateless encoder integrated peripheral and talk about the currently available Open Source userspace software for stateless VP8 encoding, as well as his work on the corresponding upstream kernel driver. Having described this background Andrzej will discuss the proposed encoding uAPI and the prospects of new hardware implementing stateless VP8 encoding. He will also explain what rate control is and share the idea of how it can be implemented for stateless video encoders. The talk will conclude with a review of possible future directions for stateless video encoding in Linux.
- 14:50 – 15:30 – WirePlumber, Propelling PipeWire for Embedded by Ashok Sidipotu, Collabora
WirePlumber is the modular and preferred session manager of PipeWire, the next-generation multimedia framework for Linux-based systems. With its upcoming 0.5 release, WirePlumber will see some fundamental changes to its system, including a move from Lua to a JSON-based syntax to define configuration settings, and a re-architecting of its scheduling mechanism. In this talk, we’ll take a closer look at these major changes, and discuss how they’ll make the PipeWire and WirePlumber ecosystem more manageable on embedded.
- 15:50 – 16:30 – Zephyr & Visual Studio Code: How to Develop Zephyr Apps with a Modern, Visual IDE by Jonathan Beri, Golioth
Visual Studio Code (or VS Code) has become a very popular developer environment for front-end and backend projects. But increasingly, embedded developers are turning to this tool too. “How do I get started with Visual Studio Code” is the most asked question in the Zephyr community Discord server. Out of the box VS Code isn’t setup up for embedded development but by leveraging extensions, supporting tools, and the right configs, it can be a powerful IDE for you to use while building Zephyr apps. In this talk, we’ll cover the current state of Zephyr support in VS Code and I’ll share my VS Code setup and tips ‘n tricks along the way.
- 16:40 – 17:20 – VZLUSAT-2: CubeSat with a Linux Payload Computer by Martin Sabol & Tomas Novotny, Czech Aerospace Research Centre (VZLÚ)
The VZLUSAT-2 nanosatellite, which started the second year of its mission in space, has the primary objective of taking images of the Earth’s surface and collecting scientific data from gamma-ray and X-ray measurements. It demonstrates the possibilities of image data retrieval and processing using a Linux computer built on a COTS SoC. Using an embedded computer in low Earth orbit requires a specific approach, increased resistance to radiation, temperature fluctuations, and limited cooling capabilities. The main design advantages come from using Linux and exploiting its capabilities, i.e., automation of on-board processes and the possibility to extend functionality.
Thursday, June 29
- 11:20 – 12:00 – Arduino to RTOS – A Pilgrim’s Progress by Brandon Satrom, Blues Inc
The gulf between the tools we use to prototype and the tools we use to scale is broad. Or is it? Over the years, the embedded world has developed a narrative that there are two types of engineers: “makers” and “real-world engineers.” Makers use Arduino and Raspberry Pi, and develop using Arduino Wiring/C or Python. Real-world engineers use eval boards from semiconductor companies and are never found without an RTOS. The problem is, this narrative isn’t true. Engineers of all types use Arduino, the Pi, and eval boards, depending on the need. And the choice of language is often more about the problem being solved and the goal of the application being written than an engineer’s experience or skill. And yet, for many of us, the venerable Real-Time Operating System (RTOS) is still an area of perceived complexity. Perhaps due to the unwieldy-sounding “Operating System” part of the name, RTOSes are still looked upon as a tool only needed for “real” applications. But they don’t have to be. In this session, Brandon Satrom will share his own journey from the Arduino world into ZephyrRTOS while building a case for developers to embrace Zephyr for all types of applications, and to make it a primary tool in their tool belt, available for all kinds of embedded applications.
- 12:10 – 12:50 – Introducing CHESTER Platform for Industrial IoT Applications by Pavel Hübner, HARDWARIO
In this talk, Pavel will introduce the CHESTER platform, which helps developers to address many industrial IoT use cases requiring LPWAN (LTE-M, NB-IoT, LoRaWAN) or satellite connectivity. CHESTER scales to many applications because of its rich hardware extension module ecosystem and multiple Zephyr RTOS mechanisms, which help developers craft a truly modular software design.
HARDWARIO (the CHESTER platform vendor) provides CHESTER SDK, which imports nRF Connect SDK (NCS) from Nordic Semiconductor. This layer has multiple reference application implementations, subsystems, drivers, samples, and shields. All those additions, altogether with the Zephyr RTOS and NCS foundations, give CHESTER users (even newcomers) the super-powers to develop and deploy industrial IoT applications in a fast manner. The talk may inspire any IoT firmware engineer about the often forgotten paradigms, such as modularity, re-usability, coherency, and cross-dependency avoidance.
- 14:10 – 14:50 – Building a Matter-Based Product for a Good Cause Using ZephyrOS and NordicSemi’s NRF52840 by Ramin Zaghi, visualSilicon
Matter is a new standard that targets the smart home sector and is supported by Google, Apple, Amazon, and other companies. It aims to reduce fragmentation across different vendors and achieve interoperability among Smart Home devices. We have been enabling Matter in a product that is designed to help people with disability and which uses Nordic Semi’s nRF52840 and ZephyrOS. In this talk, we discuss the challenges we faced and how we addressed them.
- 15:00 – 15:40 – Simplifying Zephyr Usage Through Linux Host Integration by Jason Kridner, BeagleBoard.org Foundation
By creating a tight connection between Linux and Zephyr, introducing new IoT devices can be done quickly. Linux and Zephyr are both great databases of well-tested, community-reviewed sensor, actuator, indicator, and connectivity drivers. Linux and Zephyr code bases are very different from the multitudes of available Arduino and Micropython code with vastly diverse quality levels and no driver model for standardizing usage within an application. This presentation explores 6 different mechanisms for connecting a new peripheral device to a Zephyr host and creating an associated data/control connection through a Linux host on a private network, namely:
- Arduino code on Zephyr
- Micropython on Zephyr
- Linux userspace code over Greybus network-exported interfaces
- Linux kernel driver usage over Greybus
- Native Zephyr driver
- Native Zephyr driver with Greybus-based sensor transport
We’ll explore the pros and cons of each to build awareness of the importance of native Zephyr and Linux drivers to open-source IoT development. Support of Arudino and Micropython provides rapid prototyping, but more critically, it introduces over-the-air updates and built-in networking stacks. The benefits of the Zephyr device driver model are explained from this perspective.
- 16:00 – 16:40 – Shield Your Devices: The Strength of Open-Source Software and Hardware by Marouene Boubakri, NXP
The RISC-V software ecosystem is a rapidly growing community of developers and companies working to create software and tools for the RISC-V architecture. This includes operating systems, compilers, debuggers, and other software development tools, as well as libraries and middleware for specific applications. However, one limitation of the ecosystem is the lack of a fully trusted operating system for RISC-V being able to run on a Trusted Execution Environment (TEE) as a companion to a features-rich operating system (rich OS), such as Linux. This presentation aims to fill this gap by proposing a port of Open Portable Trusted Execution Environment (OP-TEE) to RISC-V with a fully compatible design and maximum reuse of existing Trusted Applications (TAs). The TA ecosystem has grown as a result of the transition from vendor-controlled, single-purpose TEEs to open TEEs that host from multiple sources with various use cases in mind. This created more robust and customized security used in a wide range of applications, varying from mobile, automotive, industrial to IoT to enabling technologies such as AI/machine learning and connectivity. This makes the project a core security project with the final goal of delivering enhanced security at a lower cost to devices based on RISC-V and Linux.
- 16:50 – 17:30 – RISC-V and Open Source Hardware BoF by Drew Fustini, BayLibre
This BoF is a friendly space for people to learn about and discuss topics around the open RISC-V instruction set architecture and the exciting ecosystem of open-source hardware projects happening today. This spans from open-source CPU cores and open-source FPGA toolchains, to the ability to design your own chip that is completely open-source all the way to the transistor cell! Bring your questions and stories to this informal talk and learn more about the state of open hardware. RISC-V Ambassadors as well as individuals from RISC-V International should be able to attend to both spark discussion and answer questions.
- 19:00 – 20:00 – The Zephyr Project Security Overview, Progress, and Status by David Brown, Linaro & Flavio Ceolin, Intel
As more and more devices become connected, the security of these devices is becoming more and more visible. With an increase in governmental standards regarding the security of devices sold to consumers, the security of devices built using Zephyr is becoming ever more important. David and Flavio are the security chair and architect for the Zephyr project. This talk will give an overview of our security journey, so far, what is being done now to improve the security of the project, and where we hope to go. The focus will be on the idea of a security vulnerability: what happens when a vulnerability is reported, how it gets fixed, tracked, and who is notified and when, ending with the public disclosure through the CVE system.
Friday, June 30
- 09:00 – 09:40 – Building Embedded Systems with AOSP – Why You Should Consider, Best Practices and Pitfalls by Anna-Lena Marx, inovex GmbH
In our community, building embedded systems based on Linux, e.g. with Yocto or buildroot, is standard and well-known. Considering Android, respectively the AOSP as a base system feels strange at the beginning as it is a huge ecosystem that implies high system requirements. Of course, embedded Android is not a solution for each issue. Nevertheless, the AOSP provides a sophisticated base platform that is packed with a – modern UI stack – robust media and camera implementation – modern AI runtime – well-known abstraction between system and app development – energy optimization, and lots of other helpful infrastructure. This makes AOSP an interesting approach for building more complex embedded systems. A first goal of this talk is to show in which situations choosing AOSP over a plain Linux system really adds value and where not. But where to start and how are the best workflows? The AOSP is a massive and complex code base with a few hundred GB of source code. Navigating the sources, finding the right place to do changes and working with several code repositories at once is a tough task at the beginning. Thus, the second goal of this talk is to share best practices and hints to avoid lots of pitfalls from 8 years of doing embedded Android projects in different setups and sizes.
- 09:50 – 10:30 – EVerest: Electric Vehicle Chargers With Open Hardware and Software by Kai-Uwe Hermann, PIONIX GmbH
In this presentation, you will learn how to build your own electric vehicle charger using open hardware designs in combination with the EVerest open-source software stack for EV charging infrastructure. Following a quick introduction to EV charging technology, with explanations of the standards, protocols, and complexities involved, the talk will go into a deep dive into how you can build your own AC charging station. Reference hardware designs for a power board, as well as a high-level control board, will be explained in detail. This will be followed by a comprehensive overview of the EVerest software stack and the different use cases that can be implemented with it. Implementations of relevant communication protocols, such as ISO 15118, DIN SPEC 70121 and OCPP are integrated seamlessly. Drivers for hardware devices such as power meters and charging controllers are included as well. Additionally, comprehensive tools for simulating the charging process are provided. EVerest is an Apache 2.0 licensed project within LF Energy. It was initiated by PIONIX GmbH to support the electrification of the mobility sector. The hardware designs presented in this talk are CERN Open Hardware Licence Version 2 – Permissive licensed, initially developed by PIONIX GmbH as well.
- 11:00 – 11:40 – The End of the Paved Road: Maintaining Linux Kernel 4.4 Beyond LTS by Ulrich Hecht
They said it’s pointless. They said it can’t be done. Here’s how the Civil Infrastructure Platform is doing it. And why. In its mission to provide a software base for industrial and civil infrastructure projects, the Linux Foundation’s Civil Infrastructure Platform project (CIP) is committed to maintaining their Super Long Term Support (SLTS) kernels in both their regular and real-time versions for a minimum of ten years from the time of release. When a kernel is brand-new that is a rather straightforward task. For several years much of the work is done by the Linux stable kernel maintainers as they provide maintenance for Long Term Support (LTS) kernels. But there inevitably comes a time for any kernel version at which it is discontinued. That is the time the CIP kernel maintainers have to get out of the back seat and take the wheel, because giving up is not an option. That time is now. The retirement of LTS kernel 4.4 marks the first time in the CIP project’s existence that their kernel maintainers have to go it alone. Ulrich Hecht, current maintainer of the SLTS 4.4 kernel, will tell you how the CIP project intends to keep 4.4 (and its future SLTS kernels) alive for as long as it takes.
- 11:50 – 12:30 – Learn How to Support Your SoC and ISP in Libcamera by Laurent Pinchart, Ideas on Board
libcamera is the only open-source camera framework for Linux systems that supports ISP-based cameras. Thanks to its integration with other key multimedia frameworks such as GStreamer or PipeWire, libcamera’s adoption is increasing across all market segments, from embedded devices to desktops. More and more ISP and SoC vendors are exploring how to add support for their platforms to the project. Yet, while libcamera’s goals, design, architecture, and application API have been presented at multiple conferences over the last few years, little has been said of how to support a new platform. This talk will dive into the libcamera’s internals, and explain, with real-life examples, how to support a new platform. The audience will learn how to implement a pipeline handler, write image processing algorithms to control the ISP and use the compliance test suite to validate the result.
- 14:00 – 14:40 – Threads in Embedded Linux- 6 Easy Pieces by Loïc Domaigné, Doulos
Processes, lightweight processes, (green) threads, fibers, co-routines, tasks, you named it. All these names refer to programming models for implementing concurrent processing efficiently. In this talk, Loïc is going to provide you with a map of how to navigate the threads landscape on Linux. The talk starts with a brief review of the clone(2) system call, and how this translates to processes and threads at user-space level. It then reviews the thread life cycle (creation, joining, detaching, exiting), followed by a focus on the thread stack and size, and illustrates how glibc and musl differ in that regard. Loïc then discusses memory synchronization, mutexes, and condition variables and shows typical use. The talk concludes by looking at threads and signal delivery. This is a practical hands-on talk, so we’ll demo (broken-) code, look under the hood at what’s going on using tools like pmap, strace, ltrace,.. and possibly will have a peek at some musl or glibc code implementation! Featuring: Help, compiling with “-pthread” breaks my non-threaded code! When threads strike and refuse starting. Did you say stack size? Aren’t mutex just binary semaphore? What’s the condition in condition variable? There was once a happy bunch of threads in a process, suddenly a signal is delivered…
- 14:50 – 15:30 – ELISA Status and Outlook: Advancing Open Source Safety-Critical Systems by Philipp Ahmann, Robert Bosch GmbH
These days, open-source software can be found in almost every reasonably complex product running software. It runs in medical devices, robots, vehicles, and even outer space. In the underlying industry sectors, certification and safety integrity standards play an important role which at first glance seem at odds with the use of pre-existing open-source software, not developed strictly in accordance with industry standards. In this talk, recent ELISA project deliverables in the field of elements, processes, and tools are highlighted. These include system theoretic process analysis, workload tracing, call-tree visualization on kernel level, and reproducible example use cases from the field of medical devices and automotive. Their role in reducing the burden for companies to build and certify open source-based safety-critical applications is shown. Additionally, an overview of upcoming ELISA activities in 2023 is provided and how cross-project collaboration is established, as the ELISA work streams include interaction with e.g. the Zephyr, Xen, AGL, Yocto, and SPDX community. A few statements on the overall challenges of safety-critical use cases using free open-source software will help to pick up the audience which is new to safety-critical or open-source software development.
- 16:00 – 16:40 – Linux Power! (from the Perspective of a PMIC Vendor) by Matti Vaittinen, ROHM Semiconductor
Powering-up a modern SOC can require a few different stable power sources. Also, a run-time control for voltages is often required to enable optimal power usage and power savings – or to mitigate heating issues. In many cases, some more advanced features like RTC, Watchdog, or battery chargers are tightly coupled with power input. This talk aims to give a generic overview of what a Power Management Integrated Circuit (a PMIC) is and what kind of drivers may be required. From this very generic overview, the talk will dive deep into providing functional-safety-related notifiers via the Linux regulator framework. The talk attempts to shed some light on how to inform abnormal conditions like over-/under [voltage, current, temperature] via the notifiers – while asking the audience about any experience with using these notifiers.
- 16:50 – 17:30 – Camera Applications with Libcamera and PipeWire by Kieran Bingham, Ideas on Board
libcamera support is growing rapidly. With support from PipeWire, desktop integrations, and convergent applications can run on laptops and mobile alike. WebRTC has gained support for using the PipeWire Camera Portal, allowing browsers and conference applications to talk to PipeWire, to manage a complex camera through libcamera. But video is not the only use case for cameras through libcamera. Platform-agnostic camera photography applications are being developed and supported including Gnome-Camera, and Harbour-Pinhole which can run on a Desktop PC, small board computers, or supported mobile phones running PostmarketOS or a custom Linux distribution. This talk continues from the previous talk “Application Support with libcamera” given at ELCE-2022, and will explore the progress being made with browser integration for the camera portal and how that will bring conference calling features expected by Linux users with complex cameras back into the 21st century, and further look at how libcamera can be used for photography use cases with mobile devices using standard applications. Demos will be made with the latest implementations.
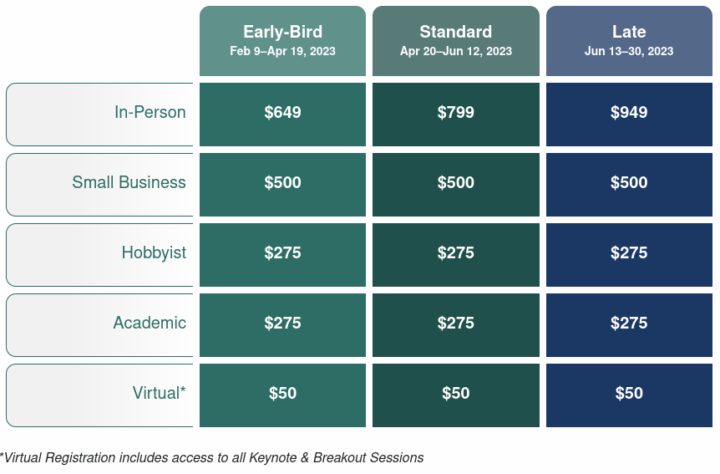
You can check out the full schedule on the Linux Foundation website. You’ll need to register to attend the event with pricing starting at $50 for virtual attendance and $275 to $949 for in-person attendance with the fees depending on when you purchase your ticket and whether you qualify for discounts.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress