We started the review of GL.inet GL-MT2500A security gateway, aka Brume 2, with an unboxing and teardown, and I’ve now had time to test the router in more detail so I’ll report my experience using the router with OpenVPN and WireGuard VPN, Tor, Adguard Home, and more. In a nutshell, it’s super easy to use, unless your ISP causes troubles, which it did in this case.
Brume 2 connection and initial setup
I connected the WAN port of the Brume 2 router to 3BB’s modem router (3BB is an ISP in Thailand), the LAN port to my laptop, and finally the USB-C power supply (power draws is 2.3 Watts at idle).
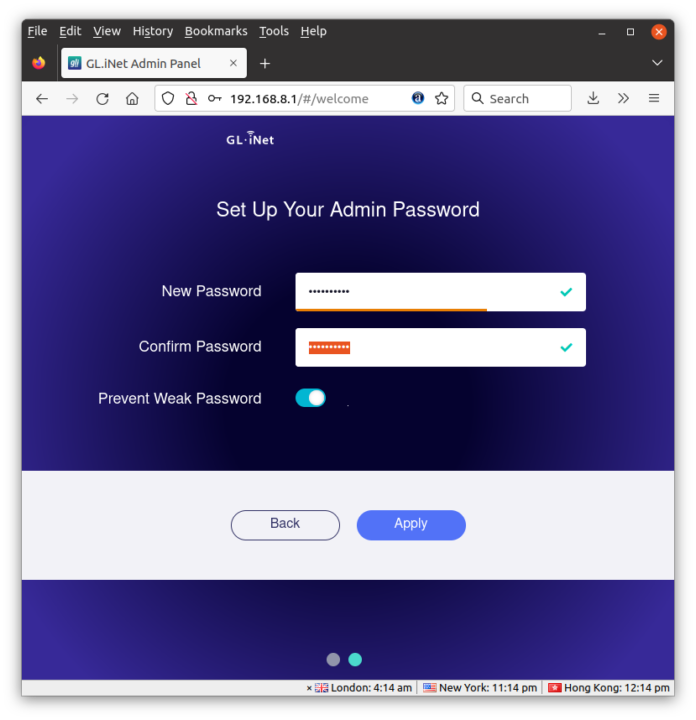
Let’s now go to the dashboard using the default IP (192.168.8.1).
This will take us through the configuration wizard to select the language and set up the admin password. I was then immediately greeted by an “Upgrade Reminder” and went with the OTA firmware upgrade without issues.
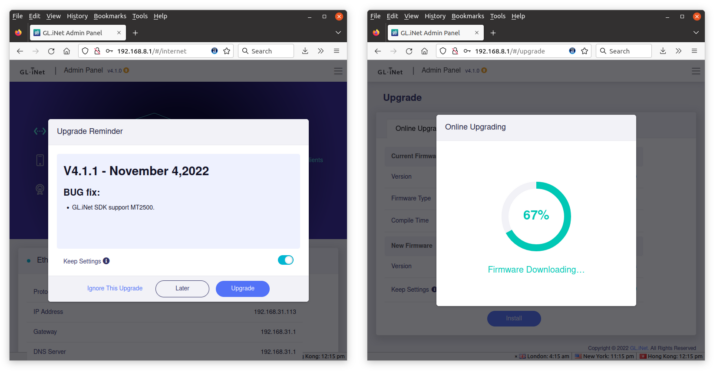
After that, I had access to the Admin Panel, now version 4.1.1.
There’s still one last step you may want to go through before considering the initial setup complete: Time Zone selection.
Brume 2 VPN options
There are six sub-menus in the VPN section: the dashboard, OpenVPN client/server, WireGuard client/server, and Tor.
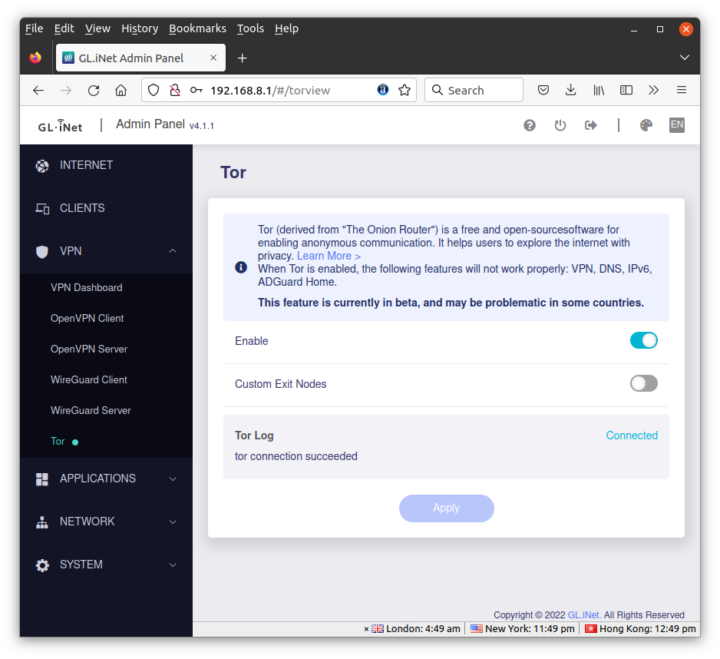
 I’ll start with Tor since it was the easiest to set up in my case as I just had to toggle the Enable slider.
I’ll start with Tor since it was the easiest to set up in my case as I just had to toggle the Enable slider.
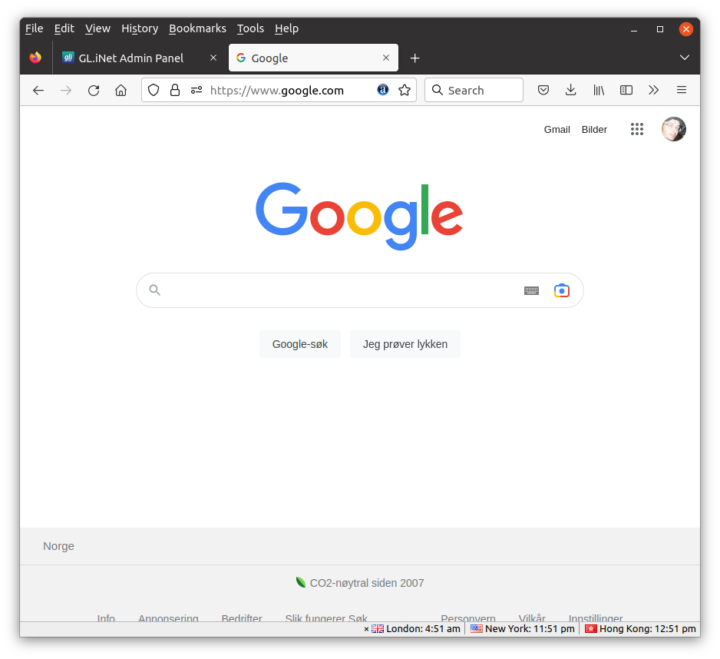
It’s easy to check whether it works by simply visiting Google, and I was redirected to Google Norway…
When visiting websites behind CloudFlare, such as CNX Software, you may see a “checking if the site connection is secure” page before reaching the request page…
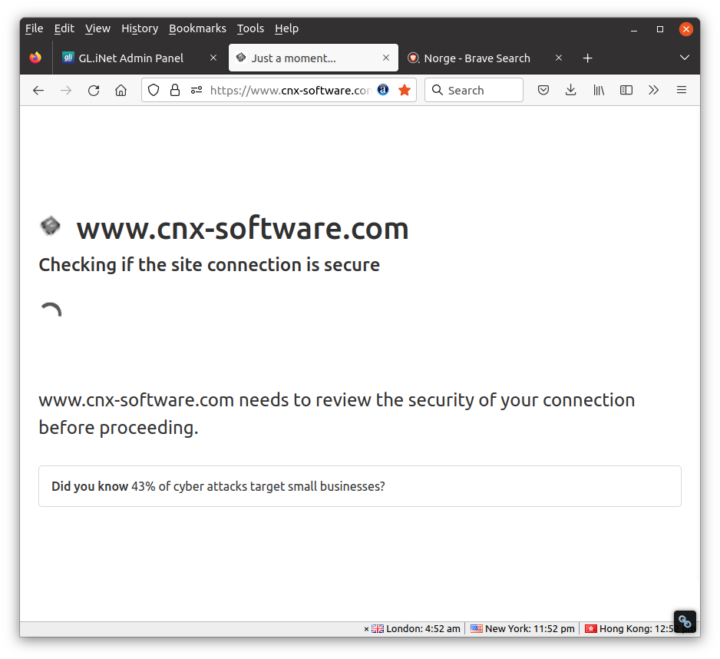
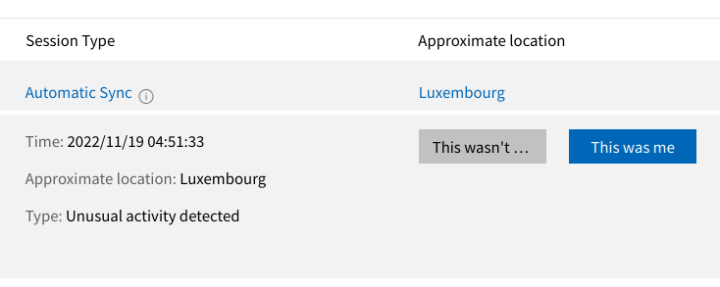
… and I got the Microsoft unusual activity…
and was even forced to change my password… Browsing anonymously through Tor is great, but it does have its little inconveniences.
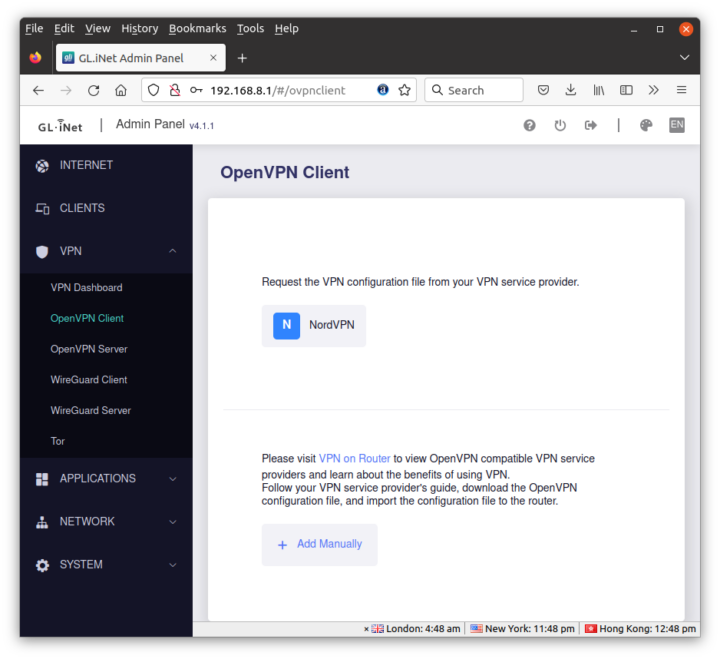
I’m not subscribed to another VPN service nor do I have setup my own VPN server, so I’ll just quickly just the settings for the OpenVPN Client supporting NordVPN by default,
and the WireGuard Client supporting AzireVPN and Mullvad by default.
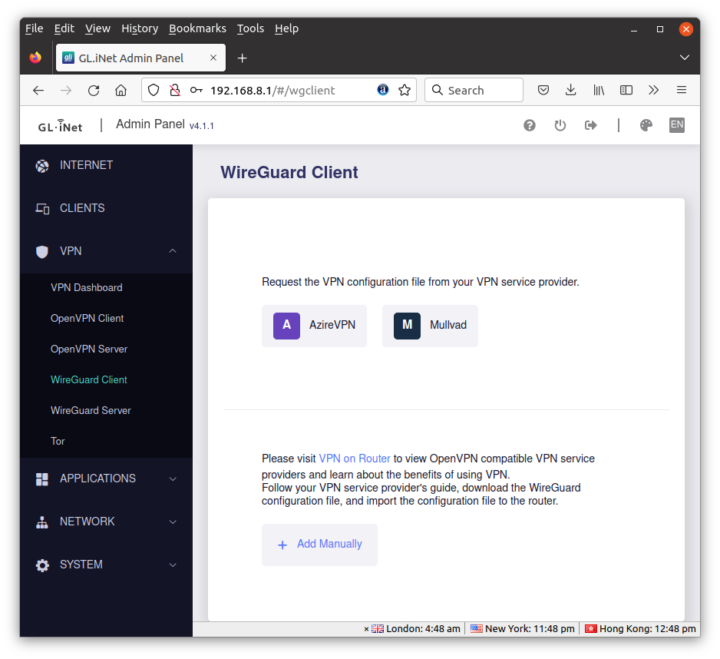 But you can obviously use any other VPN service with either the OpenVPN or WireGuard client. It may just require a bit more effort for the configuration.
But you can obviously use any other VPN service with either the OpenVPN or WireGuard client. It may just require a bit more effort for the configuration.
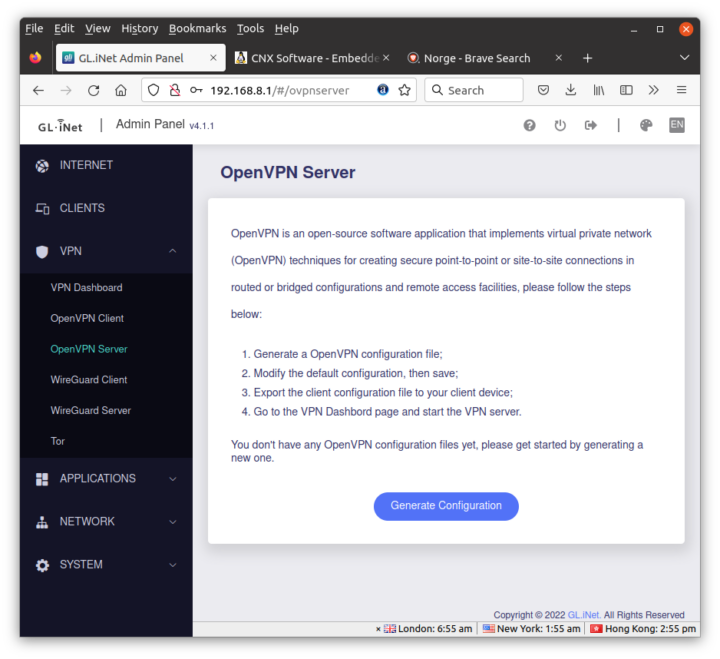
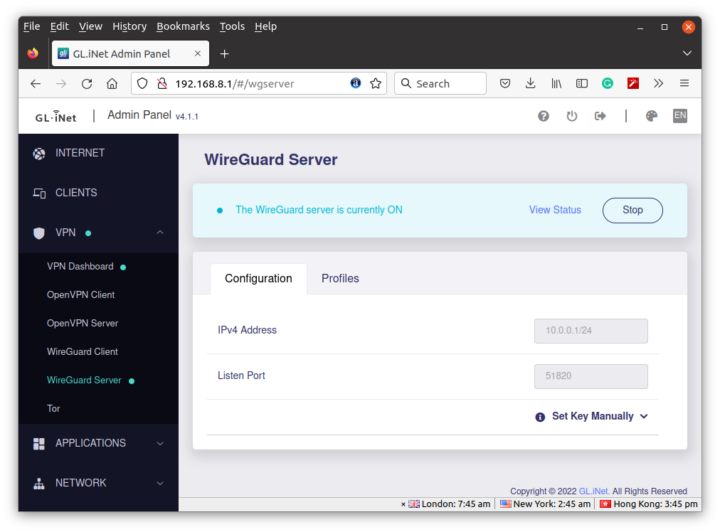
What I did try are both the OpenVPN and WireGuard servers. Let’s start with the OpenVPN Server.
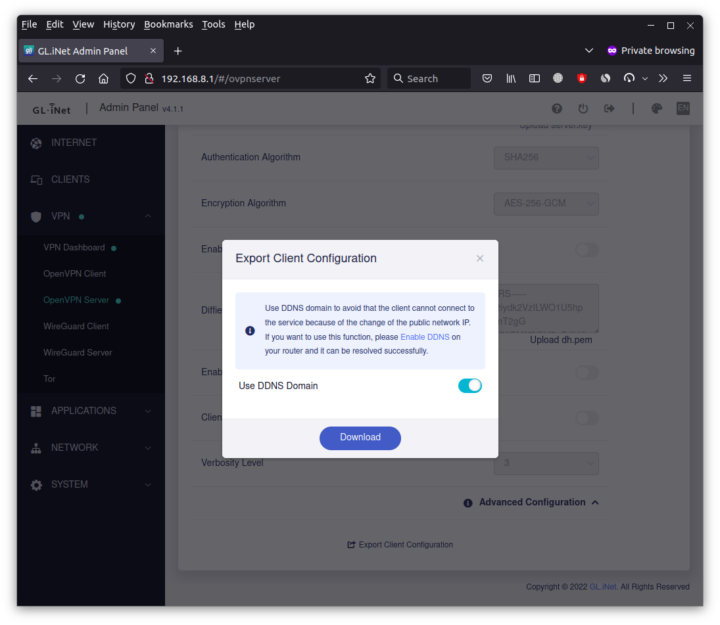
GL.iNet Admin Panel can generate the configuration automatically for the Brume 2 router using port UDP port 1194.
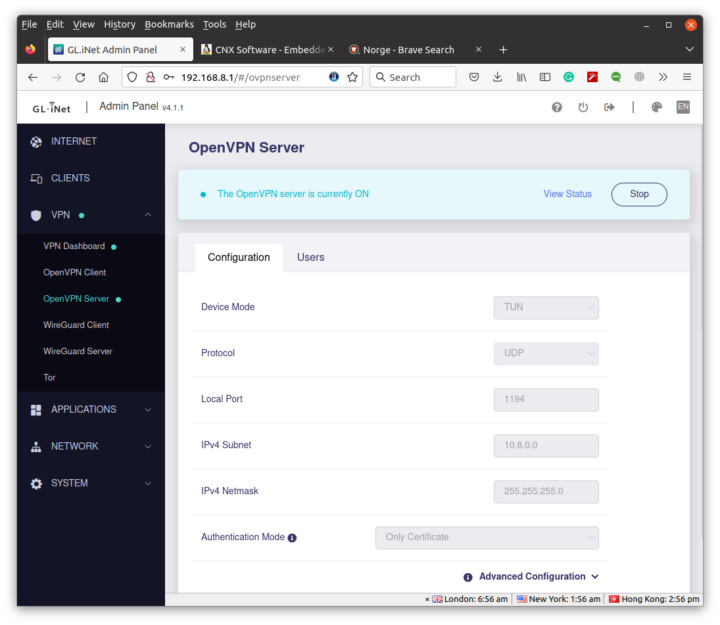
If we scroll down we can click on Export Client Configuration and select use DDNS domain since most people will have a public IP, just not a fixed public IP.
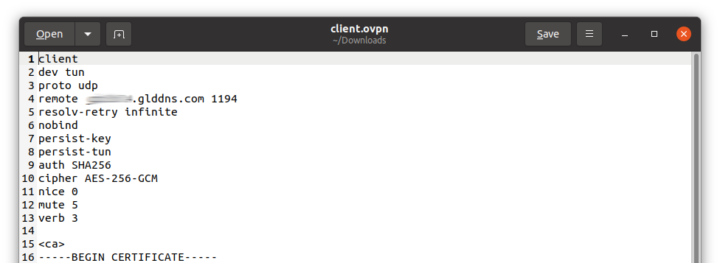
The client.ovpn file includes all parameters needed including the required certificates.
I also enabled Dynamic DNS in the Applications section of the Admin Panel.
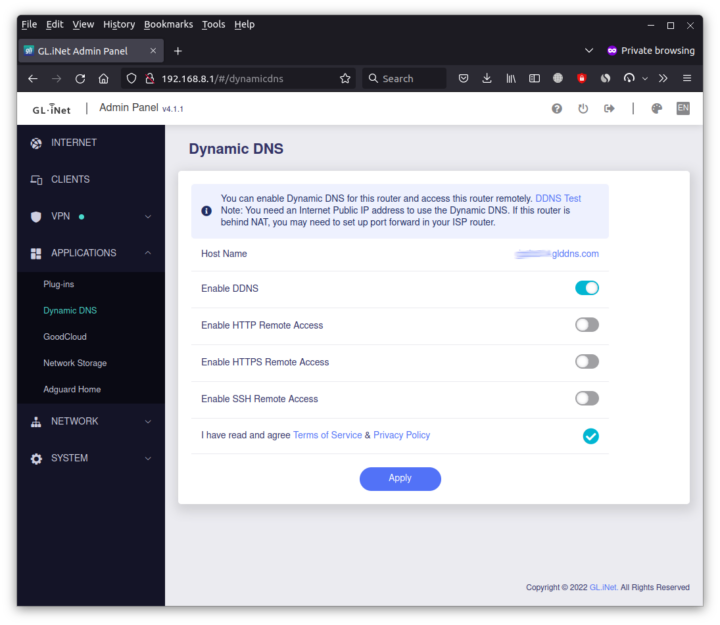
In theory, I couldinstall the OpenVPN Connect app on my Android and import the client.opvn file to get started. But not so fast, as since the Brume 2 security gateway is behind my 3BB modem router, I also added it to the DMZ zone.
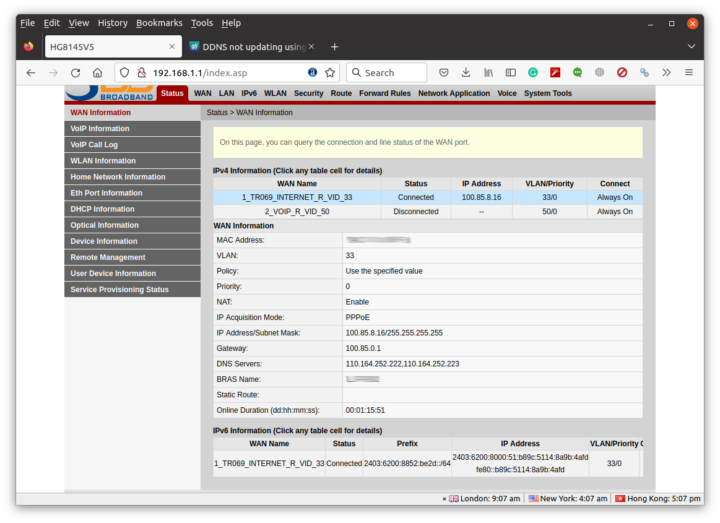
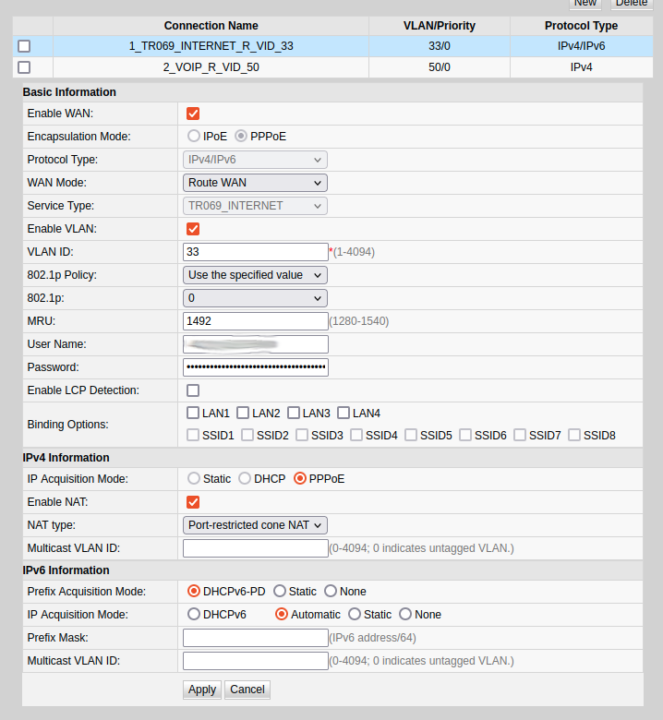
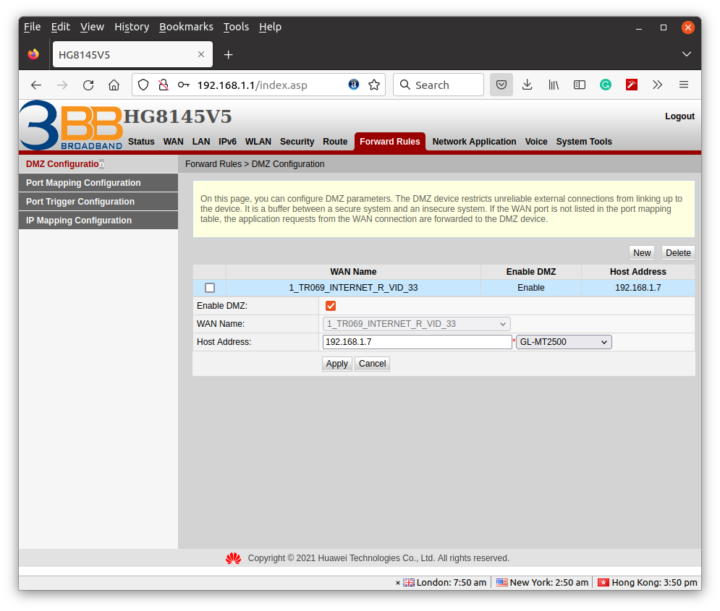 I quickly found out that the IP address provided by the 3BB router through DHCP would change after each reboot, so I just forced it to 192.168.1.8 for the MAC address of the Brume 2’s WAN port. I could see what looked like a public IP address, but I was unable to ping it. Then I realize the IP address inside 3BB’s router dashboard was different and my internet connection was inside a VLAN.
I quickly found out that the IP address provided by the 3BB router through DHCP would change after each reboot, so I just forced it to 192.168.1.8 for the MAC address of the Brume 2’s WAN port. I could see what looked like a public IP address, but I was unable to ping it. Then I realize the IP address inside 3BB’s router dashboard was different and my internet connection was inside a VLAN.
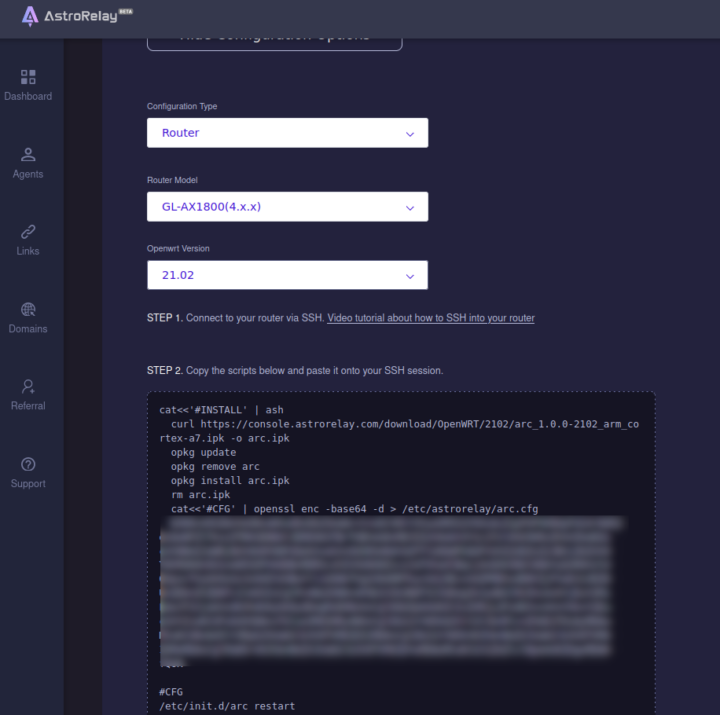
In other words, I had no public IP address. GL.iNet told me that the only solution was to use a reverse proxy, such as the company’s Astrorelay service, to use the router as a VPN server. So I signed up for a free trial account for the service providing 1GB of data. I followed some older documentation for Admin Panel 3.x, and created an agent, but I could not find anything for Brume 2 / GL-MT2500 router since it’s too new. So I selected another router running OpenWrt 21.02.
The instructions for the GL-AX1800 router require access to the terminal via SSH and let us install the Astrorelay daemon for a 32-bit Arm Cortex-A7 system, but the Brume 2 is powered by a MediaTek MT7981B (Filogic 820) dual-core 64-bit Arm Cortex-A53 processor.
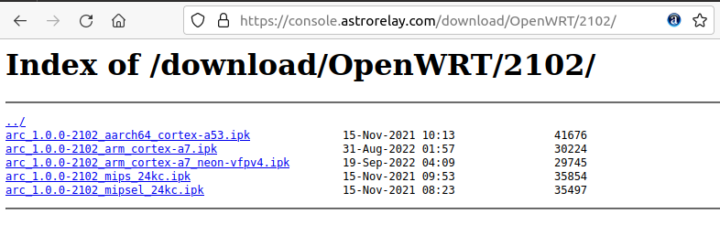 But good news, there’s also a 64-bit Aarch64 page arc_1.0.0-2102_aarch64_cortex-a53.ipkthat will work on your router. So I could successfully install Astrorelay with the commands provided in the Astrorelay dashboard since replacing the link to the ipk package.
But good news, there’s also a 64-bit Aarch64 page arc_1.0.0-2102_aarch64_cortex-a53.ipkthat will work on your router. So I could successfully install Astrorelay with the commands provided in the Astrorelay dashboard since replacing the link to the ipk package.
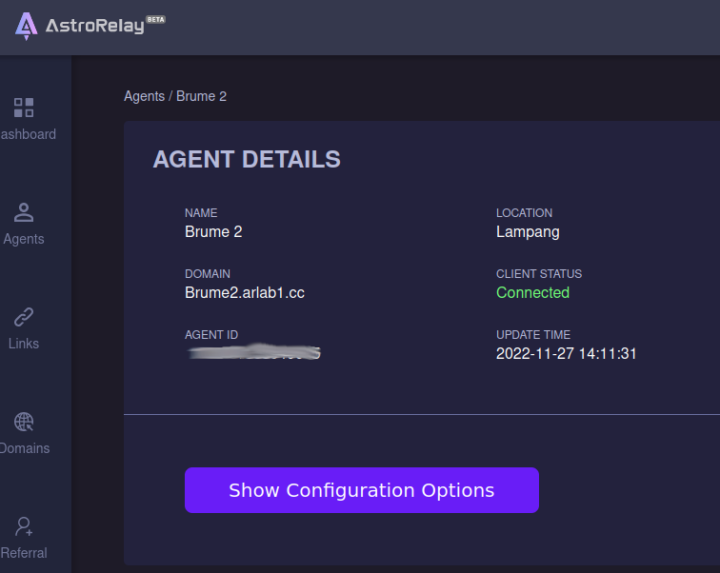
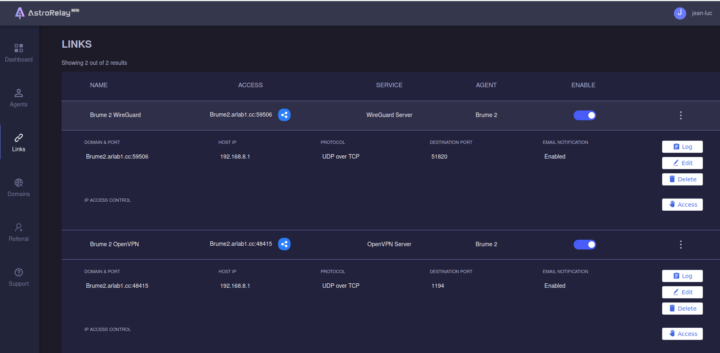
At this point, the AstroRelay dashboard showed my Brume 2 was properly connected. The next step was to create a link for OpenVPN, and I eventually did one for WireGuard too using the default 1194 and 51820 ports.
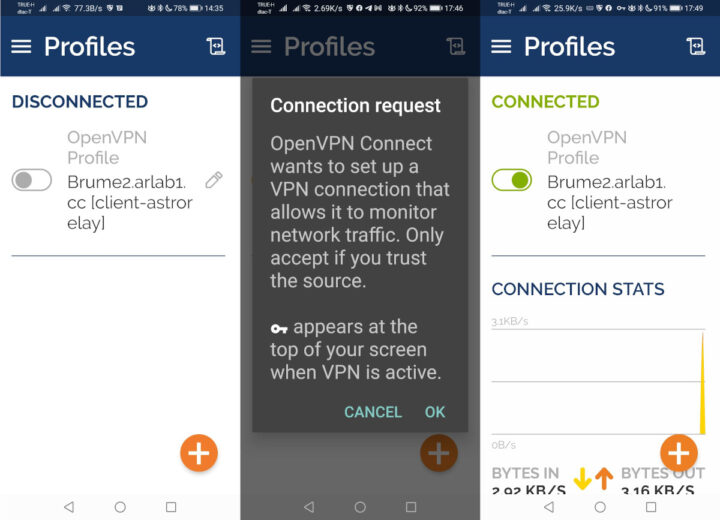
I could still not connect through OpenVPN Connect with the button turning orange for less than one second and nothing else happened. I eventually found out that I could not simply deactivate Blokada in my phone from the app, but I had to go to the VPN Settings in Android to do so.
I just had to change the remote field in the client.ovpn configuration file to the link and port defined in AstroRelay: Brume2.arlab1.cc:48415. There’s a warning the first time you connect, and then you are good to go. It took an awful amount of time, but I eventually managed to make it work. It would have been much easier with a public IP address…
Once we get this working, setting up WireGuard Server is fairly easy.
The important part is to create Profiles for each of the devices you want to connect to the network.
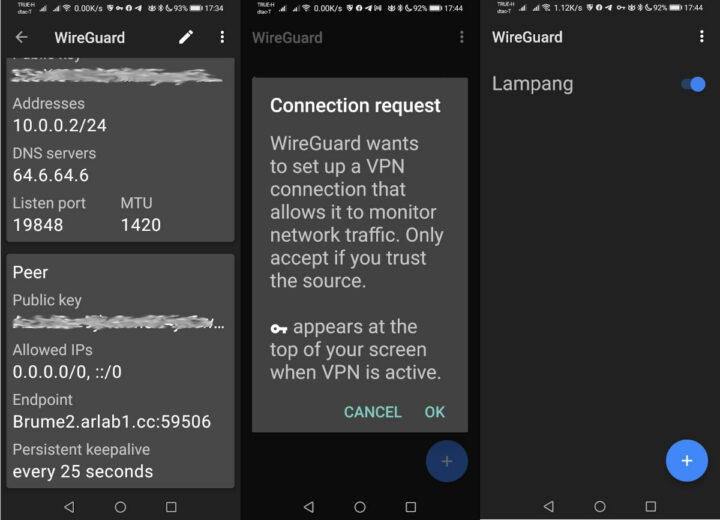
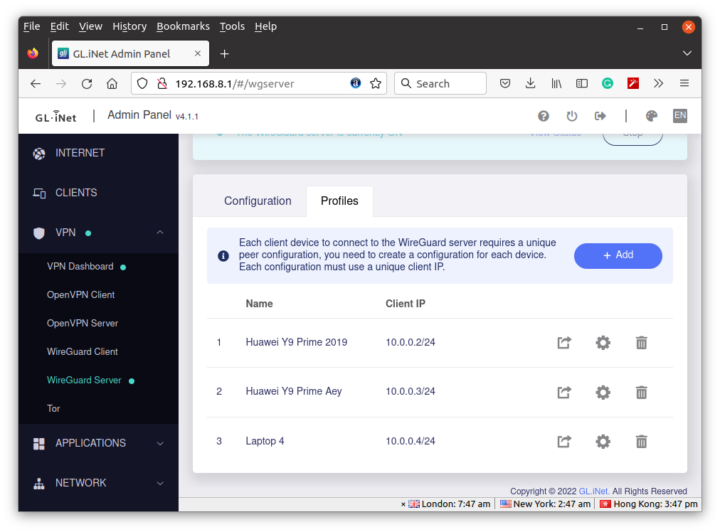 Then you can click on the icon with the arrow to get the QR code or configuration file for each device. I used the QR code with the WireGuard app in Android, and the config files with Ubuntu.
Then you can click on the icon with the arrow to get the QR code or configuration file for each device. I used the QR code with the WireGuard app in Android, and the config files with Ubuntu.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
[Interface] Address = 10.0.0.4/24 ListenPort = 2666 PrivateKey = <hidden> DNS = 64.6.64.6 MTU = 1420 [Peer] AllowedIPs = 0.0.0.0/0,::/0 Endpoint = Brume2.arlab1.cc:59506 PersistentKeepalive = 25 PublicKey = <hidden> |
In Ubuntu 20.04, I had to install the wireguard package and one dependency:
|
1 |
sudo apt install wireguard |
Create the /etc/wireguard/wg0.conf config file with the content shown further above, and start the interface:
|
1 |
sudo wg-quick up wg0 |
The interface should show up with ifconfig or ip command:
|
1 2 3 4 5 6 7 8 |
$ ifconfig wg0 wg0: flags=209<UP,POINTOPOINT,RUNNING,NOARP> mtu 1420 inet 10.0.0.4 netmask 255.255.255.0 destination 10.0.0.4 unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 1000 (UNSPEC) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 7 bytes 1036 (1.0 KB) TX errors 0 dropped 492 overruns 0 carrier 0 collisions 0 |
and we can’t ping the Brume 2 router in our VLAN:
|
1 2 3 4 5 |
$ ping 10.0.0.1 PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data. 64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=0.494 ms 64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=0.575 ms 64 bytes from 10.0.0.1: icmp_seq=3 ttl=64 time=0.560 ms |
You can bring the interface down with:
|
1 |
sudo wg-quick down wg0 |
I wanted to test performance with my phone over cellular data since I have a DTAC SIM card with “MAX speed” up to 60GB of data per month.
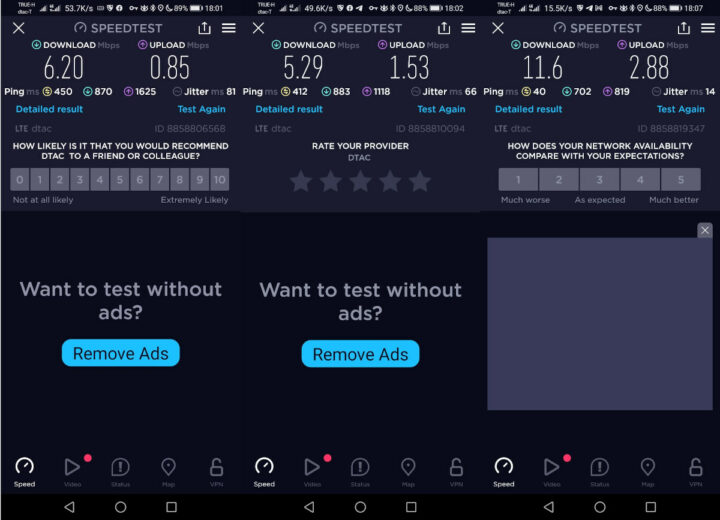
OK. I have to admit I had a slightly different expectation of the meaning of “MAX speed”. But anyway, since I’m using AstroRelay, I think the traffic goes through the Japanese server I selected (for the Asia zone), so it may not make that much sense to test performance… More importantly, I’m now unable to get any Internet traffic despite being able to connect to the VPN, and I’m not sure what may have happened, since I did not change any configuration. The AstroRelay server does not seem to reply to ping requests either… I’ll probably try later in another house with another Internet service provider.
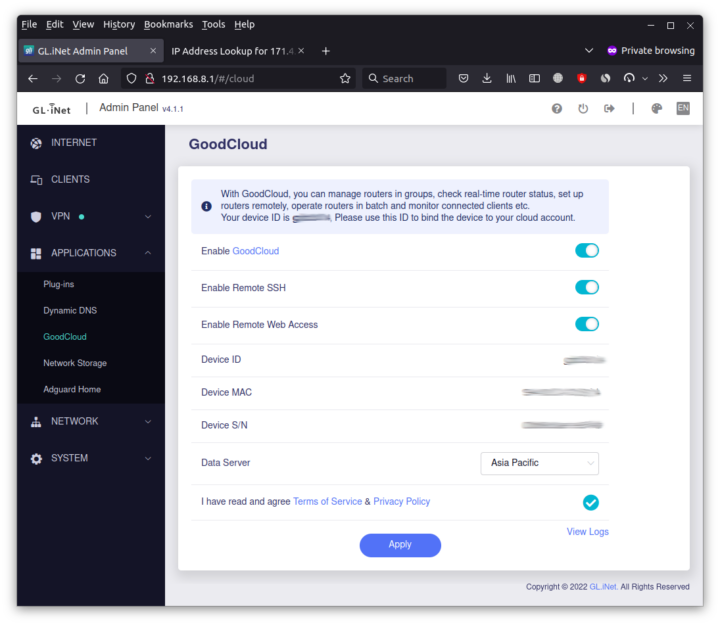
GoodCloud remote management
If you plan on managing the Brume 2 router outside of your local network, you’ll want to enable GoodCloud.
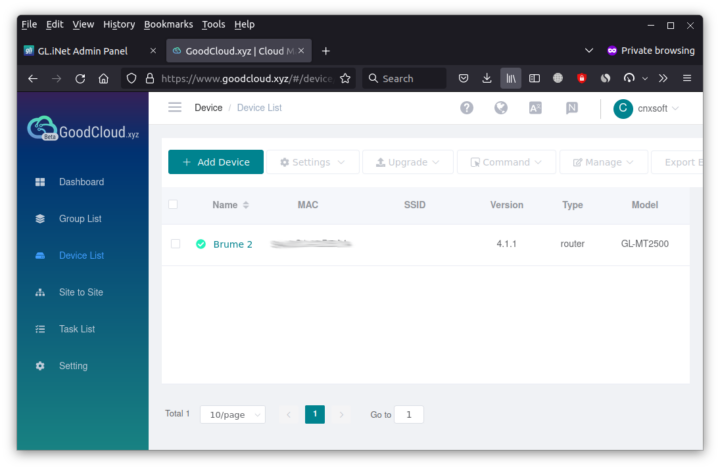
Since the dashboard will have limited options, you may want to enable remote SSH and/or Web Access if you need. After registering at https://www.goodcloud.xyz/, you should see your device(s)
If you click on a specific device you’ll see its status, client list, and have the ability to reboot it or upgrade it firmware.
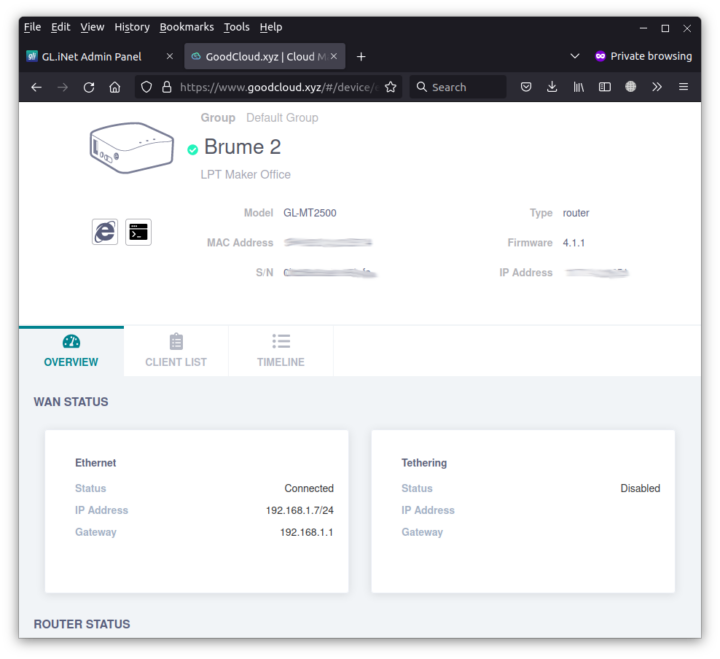
The “Internet Explorer” icon on the left side is for web access and the icon beside it is for SSH access.
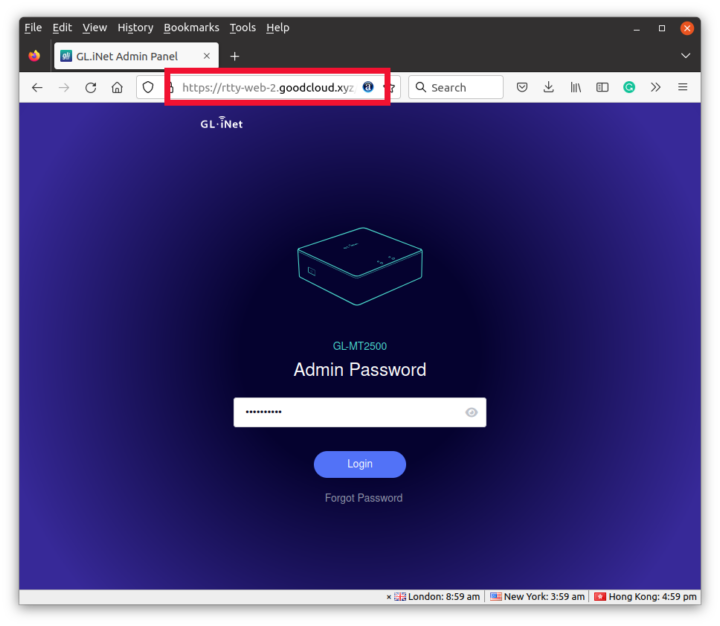
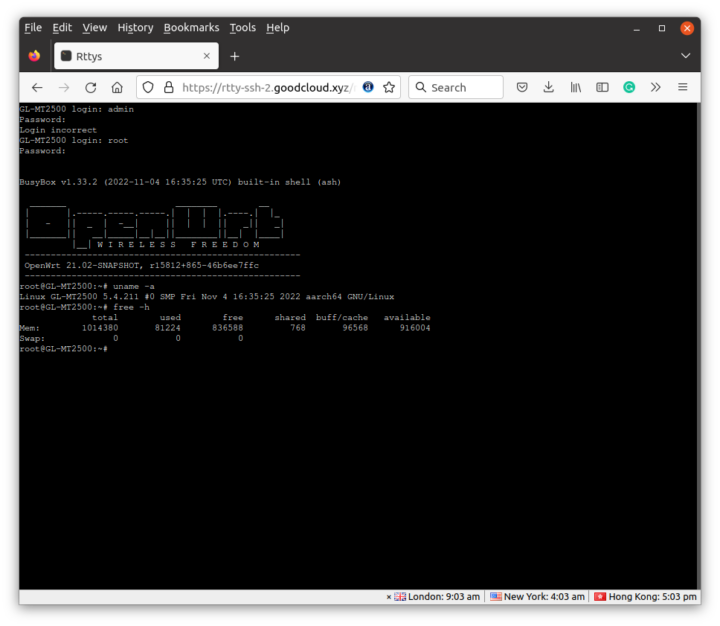
It’s extremely easy and convenient, and you could turn it off for extra security if you don’t think you need those features.
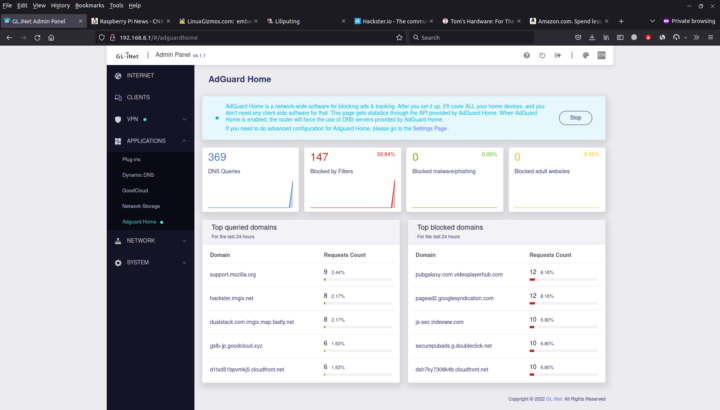
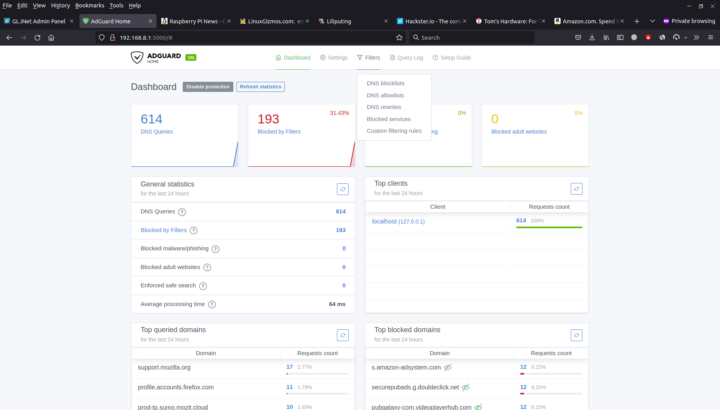
Adguard Home
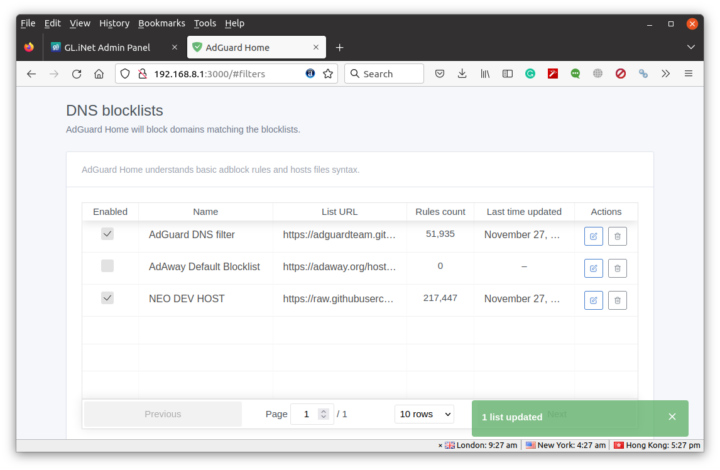
The Brume 2 security gateway also comes with an Adguard Home to block tracking and ads in all machines connected to the router. It’s also super easy to enable with one single toggle.
That means you don’t need to install plugins like Adblock Ultimate or apps like Blokada on all your devices to block ads. The rendering is a bit different as there will be white spaces for removed banners making the website look a bit cluttered. Some banners are not blocked either, but you can always click on the “Setting Page” link at the top of the Admin Panel to blacklist or whitelist specific websites or strings.
If you place the router before your WiFi access point, it will also filter tracking and ads for mobile devices without having to run a separate program that may reduce the battery life of your mobile device.
Final words
The Brume 2 is a great little security gateway for VPN, ad blocking, and remote management, that is very easy to use in most cases. Having said that I really struggle with the VPN server since my ISP does not provide a public IP address, and the documentation to use a reverse proxy such as AstroRelay could be improved. Somehow, even after it appeared that I found a solution, it was not reliable and the next day my WireGuard or OpenVPN server stopped working. I’m sure it would work better if I had a public IP address. I had not problem with Adguard Home for the ~10 days I used the router.
The model I received is the GL-MT2500A with a metal enclosure, but I’m not convinced the $20 extra it costs is worth it compared to the lighter GL-MT2500 with a plastic case. The company did not bother adding a thermal pad on the processor to use the metal case as a heatsink since based on their testing it was not necessary. For reference, the enclosure temperature was around 40°C in a round with an ambient temperature of around 28°C.
I’d like to thank GL.iNet for sending the Brume 2 (GL-MT2500A) for review. It can be pre-ordered for $79, but as just noted you may end up being better off with the GL-MT2500 with a plastic case for $59. Deliveries are scheduled to start next month.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress