Around 400 gallons of gas were stolen from a gas station a few days ago by using a special remote to put it in “dispense mode” and get the gasoline for free. It is not an isolated incident and over the years gas pumps have been hacked using different methods, with some running embedded Linux and connected to the Internet just like a router.
We previously noted devices connected o the internet like IP cameras and routers were often not secure since most were configured with default credentials (username/password). I went backpacking a few years ago, and each time I stayed somewhere I tried to log in to the router web interface using the infamous admin/admin, and it worked about 80% of the time. In 2016, I also noticed that changing the default credentials may not help, as the telnet port of my modem router was opened to the outside and configured with default credentials.
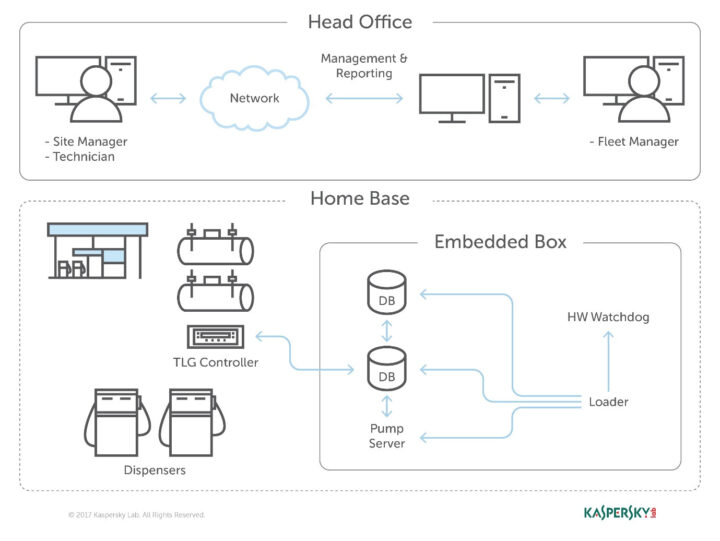
Gas pumps have a lot more in common with routers than I initially thought, as reported by FOX 8, many models come with a default passcode that may not always be changed by the gas station’s manager, and using a special remote it’s possible to change the price and other parameters. Some gas stations are also part of the Internet of Things with all gas pumps connected to the Cloud through gateways (called “embedded box” below) to enable remote monitoring, but that also introduces security vulnerabilities as noted in a Kaspersky study in 2018.
They noticed an embedded box running a Linux with a tiny httpd server, and responsible for managing every component of the station, including dispensers, payment terminals, and more. That embedded box was connected to the Internet, and searching for a specific string on service like Shodan would locate over 1,000 embedded boxes installed over the world. At the time of the study, Kaspersky said around 29% of gas stations in India, and 27% in the US were connected to the Internet.
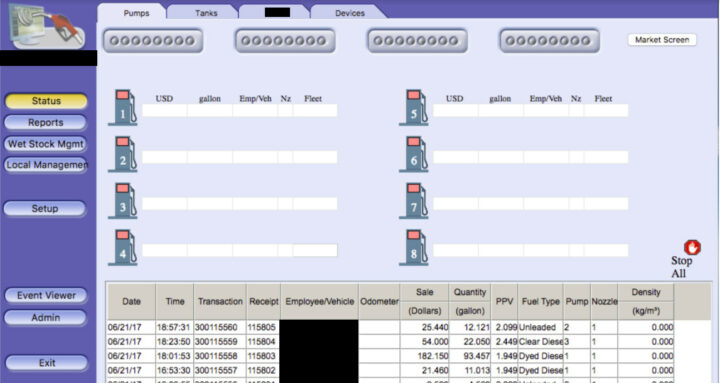
The user manuals from the manufacturer of the embedded box included screenshots, default credentials, different commands, and a step-by-step guide on how to access and manage each of the interfaces, and it did not require a skilled hacker to access the dashboard. Kaspersky “understood how obsolete the device was when we realized it was operative and accessible remotely using services you don’t expect to see in modern devices”, so I’d assume the HTTP (80) and telnet (23) ports were opened…
Once you have access to the dashboard you could potentially do some “fun things”:
- Shut down all fueling systems
- Cause fuel leakage and risk of casualties
- Change fueling price
- Circumvent payment terminal to steal money
- Scrape vehicle license plates and driver identities
- Halt the station’s operation, demanding a ransom in exchange
- Execute code on the controller unit
- Move freely within the gas station network
Further investigation of the firmware also revealed hardcoded username and password, as well as insecure code allowing remote code execution. Those vulnerabilities were fixed four years ago, but it remains to be seen if all affected embedded boxes (gateways) were updated.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress