BrakTooth is a family of new security vulnerabilities in commercial, closed-source Bluetooth Classic stacks that range from denial of service (DoS) via firmware crashes and deadlocks to arbitrary code execution (ACE) in certain IoT devices.
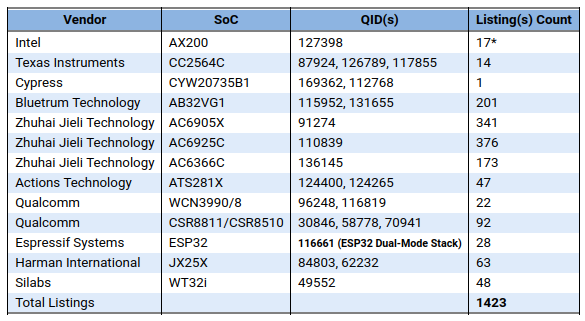
A team from Singapore has discovered 16 new security vulnerabilities after evaluating 13 Bluetooth devices from 11 vendors, but after browsing through the list of certified Bluetooth devices with impacted processors, they estimate it could impact 1400 devices.
We can see the list of BrakTooth-impacted SoCs include some familiar names like Intel AX200 (found in many laptops and computers through M.2 cards), Espressif Systems ESP32, Texas Instruments CC2564C, Qualcomm CSR8811/CSR8510, Bluetrum AB32VG1 board (based on AB5301A SoC) which I’ve just reviewed, and more…
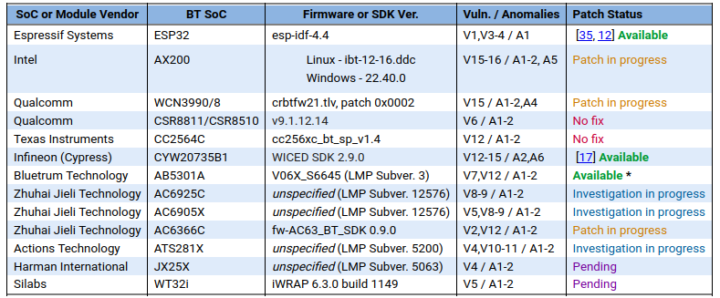
The good news is that most vendors have either already submitted a patch or working on it.
Espressif, Infineon (previously Cypress), and Bluetrum already have released patchsets for their firmware. It’s really important to update the ESP32 firmware as they were the only vendor subject to arbitrary code execution (ACE). Harman International and Silbas are still shown as pending since the status is unknown.
Qualcomm will work on a fix for WCN3990/8, but not CSR8811/CSR8510, while Texas Instruments will only work on resolving the issues for CC2564C if customers request it as explained below:
The vendor Texas Instruments has successfully replicated the security issue, however, at this stage has no plan for producing a patch. In particular, according to the Texas Instruments PSIRT team, they will consider producing a patch only if demanded by customers.
Our team approached Qualcomm to inquire whether a patch would be available for the affected devices. We were informed that they are working on a fix for WCN3990/8 and that the security issue reported in Qualcomm CSR8811A08 has been fixed since 2011 only for ROM Versions A12 and beyond. However, new products in 2021 are still being listed to use CSR8811A08, which has no plan to be fixed. Moreover, a patch for the issue on CSR8510A10 …. is not possible … due to the lack of ROM patch space.
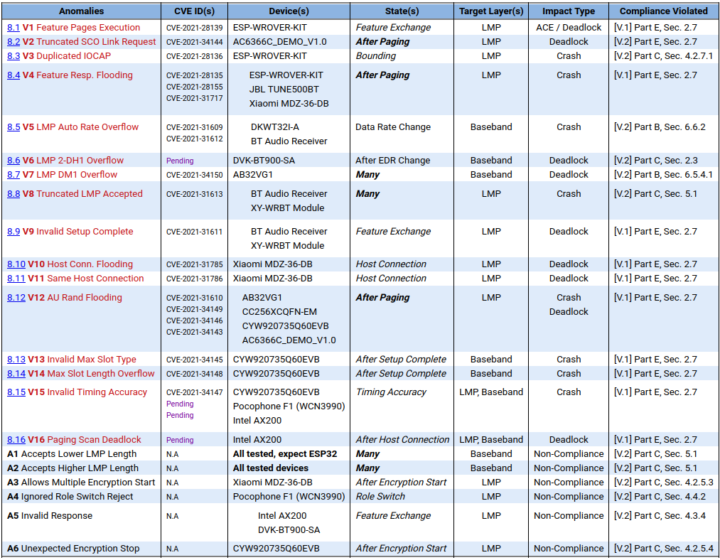
You may find the full details about the vulnerabilities listed above in the research paper.
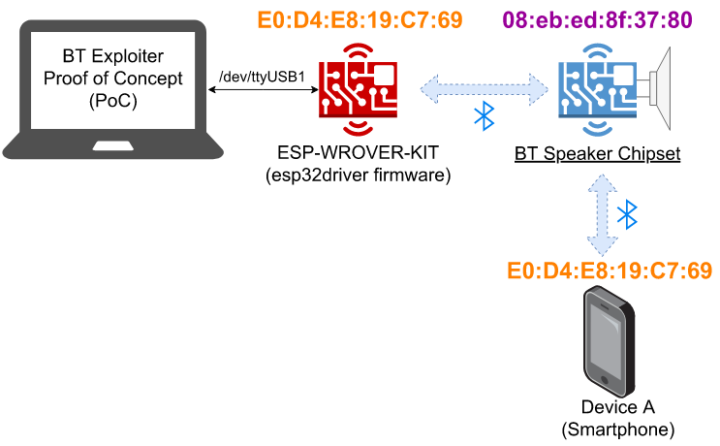
You can see how BrakTooth vulnerabilities can be exploited with a denial-of-service attach using a Bluetooth headset as a test device.
The BrakTooth PoC Tool is available to researchers, Bluetooth semiconductor, module, and OEM vendors only until October 30, 2021, after which it will be made public.
Via ThreatPost and thanks to Zoobab for the tip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress