We just reported about the Linux 5.12 changelog with a focus on Arm, MIPS and RISC-V targets on Tuesday, and at the time, the expectation was a delay of about one week after Linux 5.12-rc8 was outed on Sunday, April 18.
But Linux 5.12 could be further delayed due to shenanigans from two Ph.D. students doing a research project on open-source vulnerability at the University of Minnesota. This was announced by Greg Kroah-Hartman on the Linux kernel mailing list.
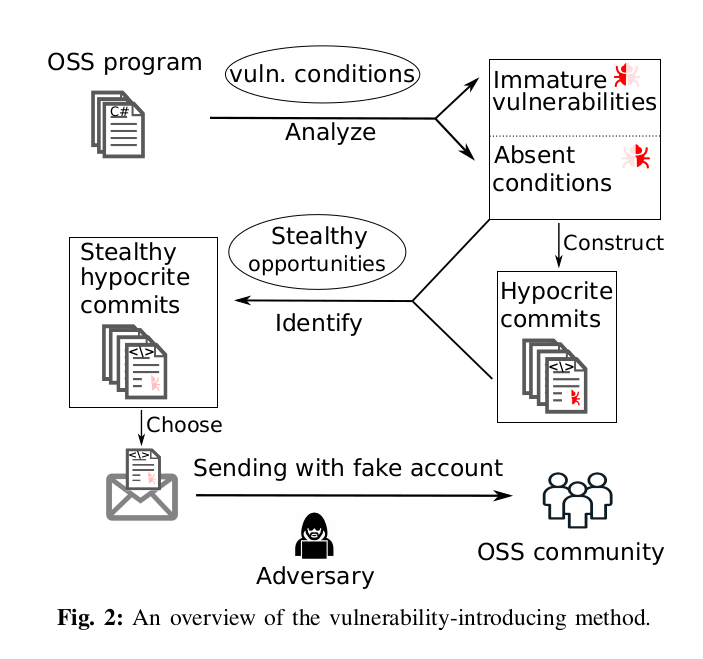
Commits from @umn.edu addresses have been found to be submitted in “bad faith” to try to test the kernel community’s ability to review “known malicious” changes. The result of these submissions can be found in a paper published at the 42nd IEEE Symposium on Security and Privacy entitled, “Open Source Insecurity: Stealthily Introducing Vulnerabilities via Hypocrite Commits”
So their work at to be reverted with 190 reversions so far. It also means future commits from the University of Minnesota will be rejected from mainline Linux by default.
You’ll find the research paper hosted on Github. The research paper mentions targets for “hypocrite commits” include large projects that accept commits from third parties including the Linux kernel, Android, FreeBSD, Firefox, Chromium, OpenSSL, and others. But it appears their Proof-of-Concept experiment only targets the Linux kernel using UAF (use-after-free) vulnerabilities as they identified over “6K immature UAF vulnerabilities in the Linux kernel that can potentially be turned into real vulnerabilities”.
The paper also implies they did so ethically and informed the maintainers as soon as one of their patchsets was confirmed.
Our goal is not to introduce vulnerabilities to harm OSS. Therefore, we safely conduct the experiment to make sure that the introduced UAF
will not be merged into the actual Linux code…
Once a maintainer confirmed our patches, e.g., an email “looks good”, we immediately notify the maintainers of the introduced UAF and request them to not go ahead to apply the patch.
…
All the UAF-introducing patches stayed only in the email exchanges, without even becoming a Git commit in Linux branches. Therefore, we ensured that none of our introduced UAF bugs was ever merged into any branch of the Linux kernel, and none of the Linux users would be affected
They also wrote they point out the bug to the maintainers and provide the correct patches. But after reading Greg KH email I don’t think he shares the same feeling. It could be due to miscommunication, we just don’t know at this point.
Evaluating the security of open-source projects is a commendable initiative, but testing is certainly an issue, as it can’t be done by informing maintainers that you’re about to introduce “hypocrite commits” in advance. I don’t know the right answer, but if you feel you do, please feel free to comment below.
Thanks to dgp for the tip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress