Code gets continuously written and updated for new features, optimizations and so on. Those extra lines of code sometimes come at a cost: a security bug gets inadvertently introduced into the code base. The bug eventually gets discovered, a report is filled, and a software fix is committed to solve the issue, before the new software or firmware to push to the end user. This cycle repeats ever and ever, and this means virtually no software or device can be considered totally secure.
The University of Michigan has developed a new processor architecture called MORPHEUS, and that blocks potential attacks by encrypting and randomly reshuffling key bits of its own code and data several times per second through a “Churn Unit”.
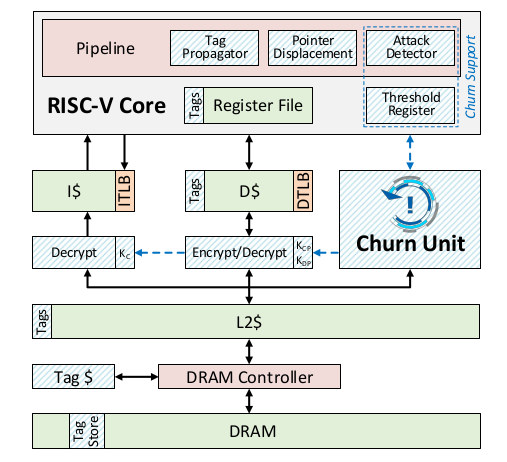 The new RISC-V based processor architecture does not aim to solve all security issues, but focuses specifically on control-flow attacks made possible for example by buffer overflows:
The new RISC-V based processor architecture does not aim to solve all security issues, but focuses specifically on control-flow attacks made possible for example by buffer overflows:
Attacks often succeed by abusing the gap between program and machine-level semantics– for example, by locating a sensitive pointer, exploiting a bug to overwrite this sensitive data, and hijacking the victim program’s execution. In this work, we take secure system design on the offensive by continuously obfuscating information that attackers need but normal programs do not use, such as representation of code and pointers or the exact location of code and data. Our secure hardware architecture, Morpheus, combines two powerful protections: ensembles of moving target defenses and churn. Ensembles of moving target defenses randomize key program values (e.g., relocating pointers and encrypting code and pointers) which forces attackers to extensively probe the system prior to an attack. To ensure attack probes fail, the architecture incorporates churn to transparently re-randomize program values underneath the running system. With frequent churn, systems quickly become impractically difficult to penetrate.
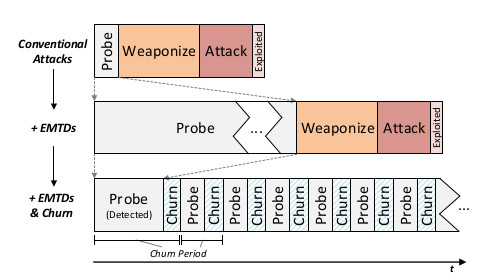
The chip’s churn rate is set to 50ms by default since it only slows performance by about 1% and is said to be several thousand times faster than the fastest electronic hacking techniques. But it can adjusted, and the processor does increase the churn rate is a suspected attack is detected by the built-in attack detector.
MORPHEUS architecture was successfully tested using real-world control-flow attacks including stack overflow, heap overflow, and return-oriented programming (ROP) attacks, as all of the attack classes were stopped in a simulated Morpheus architecture
You can find more details in the paper entitled “Morpheus: A Vulnerability-Tolerant Secure Architecture Based on Ensembles of Moving Target Defenses with Churn“.
Thanks to TLS for the tip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress




