Until today, I only knew of two authentication methods for SSH: the traditional username/password and key-based login with private/public keys with the latter being more secure and not requiring any password.
But I’ve just found out it’s also possible to login to SSH using two-factor authentication relying on your smartphone to get an OTP code like you would to access some banking services as it can easily be enabled in Armbian.
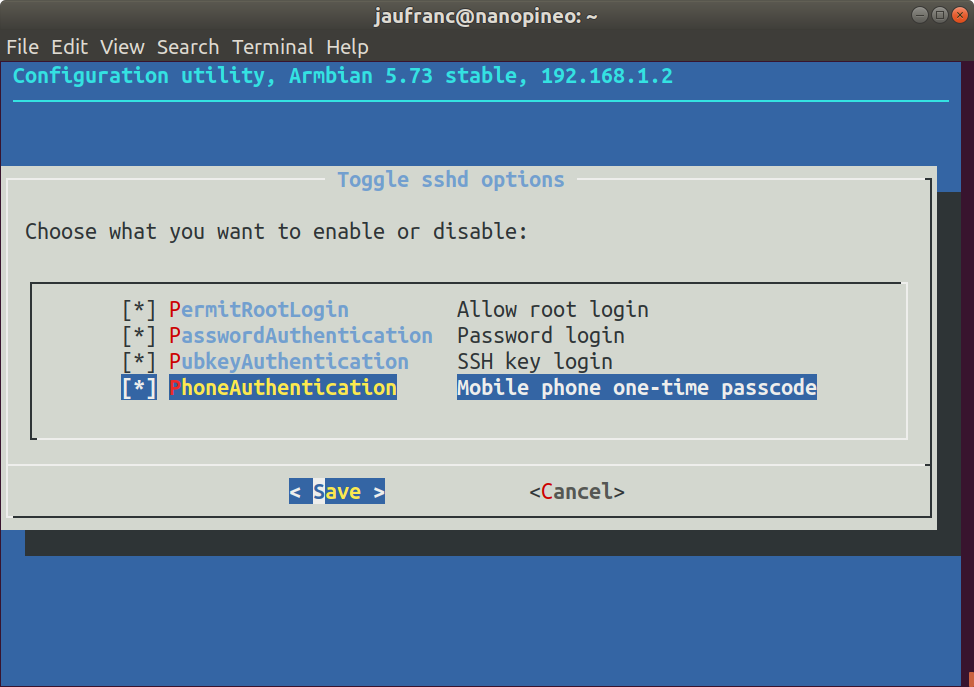
First you’ll want to enable key-based login with private/public keys, or you won’t be able to access your board anymore after enabling 2FA except via the serial console. Now simply start armbian-config, and go to System Settings->Reconfigure SSH daemon to enable PhoneAuthentication “mobile phone one-time passcode”. We’re not done yet, so don’t close Armbian-config
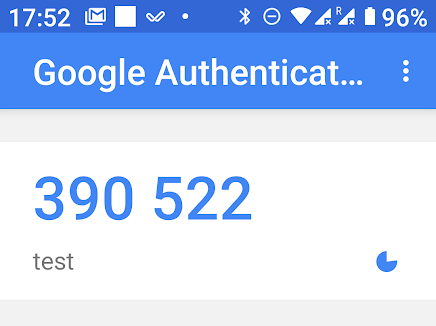
You’d then need an Android or iOS phone running Google Authenticator app to receive the OTP (one-time password). After enabling PhoneAuthenticator in armbian-config, you’ll see a new option to generate token select it, and it should show a QR core. Open Google Authenticator and scan the QR core to register the app. The app will then generate a code every 60 second for “test” device which you can use to login.
You can obviously rename the device to something more relevant. But next time you login through SSH, you should be asked for the code showing in your phone. For some reasons it did not work for me, even after I disable all SSH methods except for “PhoneAuthentication”, I can just login without any password to my NanoPi NEO board running the latest version of Armbian.
If you’re not running Armbian, instructions to setup 2FA authentication in Debian 9 can be found here.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress