When I think about geolocation in I normally think about global navigation satellite systems such as GPS, GLONASS, Galileo, or Beidou, as well as IP geolocation, but the latter is highly inaccurate, and often only good for find out about the country, region, or city.
But if you’ve ever been into your phone location settings, you’d know GPS is only one option, as it can also leverage cellular base stations and WiFi SSIDs, where the former working where there’s coverage, and the later in area with a high enough density of access points. Somehow, I had never thought about using such technology to find location with WiFi modules until Espressif Systems released an application note entitled “Geolocating with ESP8266“.
This document describes how the ESP8266 module may be used to scan for nearby Wi-Fi access points and, then, use their SSID, RSSI and MAC address to obtain a potential fix on the device’s geolocation, using Google geolocation API.
That’s basically a two step process with an AT command returning the list of available APs, SSID, RSSI, and MAC Address:
|
1 2 3 4 |
AT+CWLAP +CWLAP:(2,"HotelFlower",-76,"c8:3a:35:b3:16:48",11,0,0) +CWLAP:(3,"IoTBits",-93,"08:bd:43:66:6a:86",6,-27,0) |
and after setting up a secure SSL connection, you can then feed that data to Google Geolocation API to get the location with a command that looks like (wifiAccessPoint data not filled here):
|
1 2 3 4 5 6 7 8 9 |
AT+CIPSEND=336 > POST /geolocation/v1/geolocate?key=AIzaSyCNStbdlDS_L HTTP/1.1 Host: www.googleapis.com Content-Type: application/json Content-Length: 166 {"homeMobileCountryCode": 310, "homeMobileNetworkCode": 410, "radioType": "gsm", "carrier": "Vodafone", "considerIp": "true", "cellTowers": [], "wifiAccessPoints":[]} |
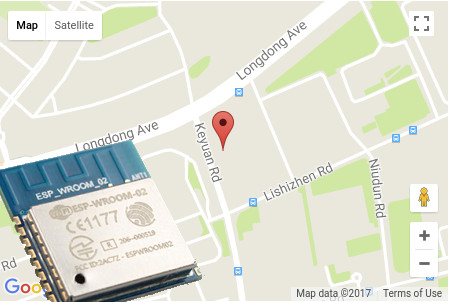
Further research led me to m0xpd experimentation with Geolocation on ESP8266 last year, using both IP geolocation (found to be very inaccurate), and Google or Mozilla APIs, and posted his Arduino source code on Github. The Google API found his actual home in Manchester with just the information retrieved from the list of access points.
That also means that unsecured devices on the public Internet can easily be located, as an hacker logins to a router or IoT device, he just needs to run a command to find out the information required by his preferred geolocation API.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress