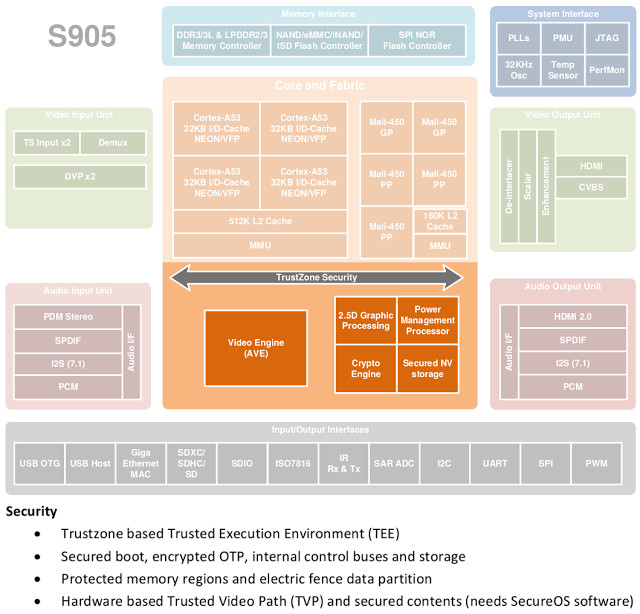
Amlogic S905 processor used in many Android TV boxes and ODROID-C2 development board implements ARM TrustZone security extensions to run a Trusted Execution Environment (TEE) used for DRM & other security features.
He explains the steps they went through and how they managed to exploit vulnerability to bypass secure boot in a detailed technical blog post.
They first started by looking for info in Amlogic S905 datasheet, but most info about TrustZone had been removed from the public version. So not that much help here except a potential address for BOM Root (ROMBOOT_START 0xD9040000). The next step was to connect the UART pins in order to access the serial console, but he could not read the BootROM from there most probably because you can’t access secure code from an non-secure memory.
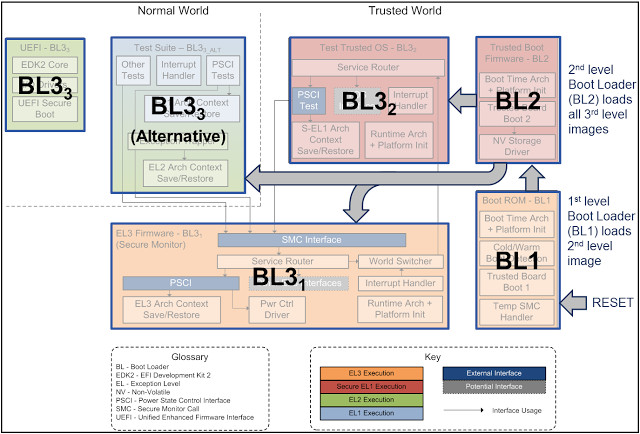
However, a closer look at the boot log lead them to find the bootloaders were based on the ARM Trusted Firmware (ATF) reference implementation, which include BL1x (BootROM in SoC), BL2, and BL3x bootloaders as shown in the diagram below.
At this point everything becomes much more technical, as he explains various attempts using U-Boot bootloader, SMC (Secure Monitor Call) interface, and bypassing the Secure Boot chain. The first attempt was a non-stater, the second could have been exploitable but might have required some expert skills and time, but the third one was successful after an analysis of the mechanism used by BL2 to parse and authenticate the BL31 image, and finding out the cryptographic code came from OSS PolarSSL/mbed TLS project.
Further reverse-engineering of the “authentication” header revealed that BL2 is only using SHA-256 hash to verify the integrity of the firmware, and that there’s no actually authentication. To confirm their findings, they customized a BL31 firmware, updated the SHA-256 hash (using aml-bootloader-tool script), and it would boot, and eventually they managed to dump the BootROM from Amlogic S905 SoC.
That’s the conclusion:
The S905 SoC provides hardware features to support Secure Boot, however OEMs can still choose to enable it or not. But even when Secure Boot is enforced, a flaw in the current version of Amlogic’s BL2 allows to bypass it. So Trusted Execution Environment cannot be trusted. The good news is BL2 can be patched, unlike BootROM.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress